Introduction:
This blog post details how to securely invoke AWS Lambda functions using Lambda URLs with AWS IAM authentication and throttling limits to add more security to the Lambda function. It covers setting up the necessary infrastructure using AWS CloudFormation, generating AWS Signature Version 4 for authenticated requests, and testing the setup using both the command line and testing tool like Postman.
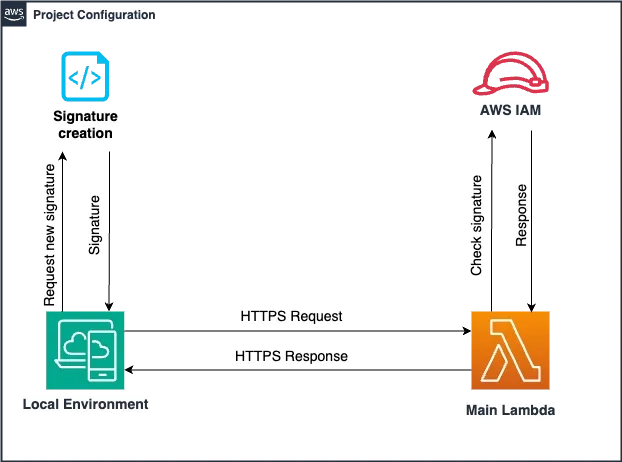
About the project:
Use Case Scenario: Invoking Lambda Functions from Different Environments. This setup allows Lambda functions to be invoked from various environments, including non-AWS infrastructure, such as local environments, on-premises servers.
For unauthorized or throttled requests that don’t invoke the Lambda function, no charges will be incurred. Here are the key points:
Throttling and Concurrency: Setting ReservedConcurrentExecutions will limit the number of concurrent executions. If the limit is reached, additional requests will be throttled, and no charges will be incurred for these throttled requests.
Authorization Failures: Requests that fail due to authorization errors (e.g., invalid IAM credentials) will not result in Lambda function invocation. These requests are handled only by the IAM service, and no charges will be incurred for these unauthorized requests.
Additional Security: AWS Shield Standard is automatically available for Lambda functions. More information can be found here.
Monitoring: Monitoring of the Lambda function throttling can be helpful by creating a CloudWatch alarm based on the “Throttles” metric.
References and useful links:
Authenticating requests documentation: AWS S3 — Authenticating Requests.
Examples of creating AWS SigV4 signatures in different programming languages: AWS SigV4 Signing Examples.
Note: Function URLs are not supported in some regions. More information can be found here.
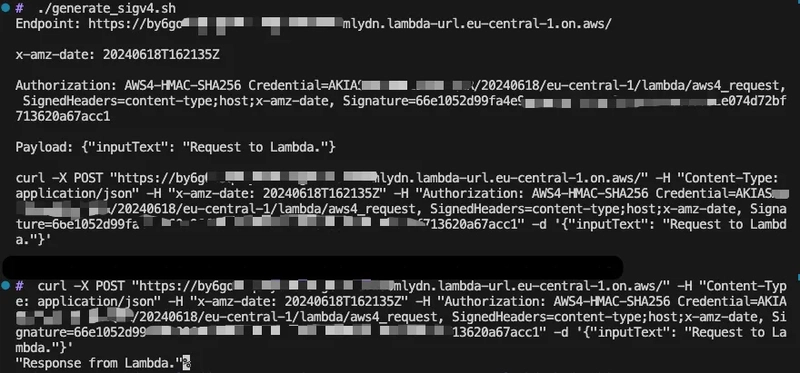
The generate_sigv4.sh script:
#!/bin/sh
# Request parameters
METHOD="POST"
SERVICE="lambda"
REQUEST_PAYLOAD='{"inputText": "Request to Lambda."}' # simple payload
# Environment variables
AWS_ACCESS_KEY=$AWS_ACCESS_KEY_ID
AWS_SECRET_KEY=$AWS_SECRET_ACCESS_KEY
REGION=$AWS_REGION
HOST=$LAMBDA_FUNCTION_HOST
ENDPOINT="https://${HOST}/"
# Check if environment variables are set
if [ -z "$AWS_ACCESS_KEY" ] || [ -z "$AWS_SECRET_KEY" ] || [ -z "$HOST" ]; then
echo "Error: AWS_ACCESS_KEY_ID, AWS_SECRET_ACCESS_KEY, and LAMBDA_FUNCTION_HOST must be set as environment variables."
exit 1
fi
# Get the current date and time
AMZ_DATE=$(date -u +"%Y%m%dT%H%M%SZ")
DATE_STAMP=$(date -u +"%Y%m%d")
# Create a canonical request
CANONICAL_URI="/"
CANONICAL_QUERYSTRING=""
CANONICAL_HEADERS="content-type:application/json\nhost:${HOST}\nx-amz-date:${AMZ_DATE}\n"
SIGNED_HEADERS="content-type;host;x-amz-date"
PAYLOAD_HASH=$(printf "$REQUEST_PAYLOAD" | openssl dgst -sha256 | sed 's/^.* //')
CANONICAL_REQUEST="${METHOD}\n${CANONICAL_URI}\n${CANONICAL_QUERYSTRING}\n${CANONICAL_HEADERS}\n${SIGNED_HEADERS}\n${PAYLOAD_HASH}"
# Create a string to sign
ALGORITHM="AWS4-HMAC-SHA256"
CREDENTIAL_SCOPE="${DATE_STAMP}/${REGION}/${SERVICE}/aws4_request"
STRING_TO_SIGN="${ALGORITHM}\n${AMZ_DATE}\n${CREDENTIAL_SCOPE}\n$(printf "$CANONICAL_REQUEST" | openssl dgst -sha256 | sed 's/^.* //')"
# Create the signing key
kSecret=$(printf "AWS4${AWS_SECRET_KEY}" | xxd -p -c 256)
kDate=$(printf "${DATE_STAMP}" | openssl dgst -sha256 -mac HMAC -macopt hexkey:"$kSecret" | sed 's/^.* //')
kRegion=$(printf "${REGION}" | openssl dgst -sha256 -mac HMAC -macopt hexkey:"$kDate" | sed 's/^.* //')
kService=$(printf "${SERVICE}" | openssl dgst -sha256 -mac HMAC -macopt hexkey:"$kRegion" | sed 's/^.* //')
kSigning=$(printf "aws4_request" | openssl dgst -sha256 -mac HMAC -macopt hexkey:"$kService" | sed 's/^.* //')
# Create the signature
SIGNATURE=$(printf "$STRING_TO_SIGN" | openssl dgst -sha256 -mac HMAC -macopt hexkey:"$kSigning" | sed 's/^.* //')
# Create the authorization header
AUTHORIZATION_HEADER="${ALGORITHM} Credential=${AWS_ACCESS_KEY}/${CREDENTIAL_SCOPE}, SignedHeaders=${SIGNED_HEADERS}, Signature=${SIGNATURE}"
# Output the necessary information for test tool like Postman
echo "Endpoint: ${ENDPOINT}\n"
echo "x-amz-date: ${AMZ_DATE}\n"
echo "Authorization: ${AUTHORIZATION_HEADER}\n"
echo "Payload: ${REQUEST_PAYLOAD}\n"
# Output the curl command
echo "curl -X ${METHOD} \"${ENDPOINT}\" -H \"Content-Type: application/json\" -H \"x-amz-date: ${AMZ_DATE}\" -H \"Authorization: ${AUTHORIZATION_HEADER}\" -d '${REQUEST_PAYLOAD}'\n"
Prerequisites:
Before starting, ensure the following requirements are met:
- An AWS account with permissions to create resources.
- AWS CLI https://aws.amazon.com/cli/ installed on local machine.
- OpenSSL installed on the test environment.
Deployment:
1.Clone the repository.
git clone https://gitlab.com/Andr1500/lambda-url-with-iam-auth.git
2.Check and increase the Lambda function Concurrent Executions quota (if necessary).
aws service-quotas get-service-quota \
--service-code lambda \
--quota-code L-B99A9384
aws service-quotas request-service-quota-increase \
--service-code lambda \
--quota-code L-B99A9384 \
--desired-value 100
3.Fill in all necessary parameters in the infrastructure/root.yaml CloudFormation template and create the CloudFormation stack.
aws cloudformation create-stack \
--stack-name invoke-lambda-url-iam-auth \
--template-body file://infrastructure/root.yaml \
--capabilities CAPABILITY_NAMED_IAM \
--disable-rollback
4.Retrieve outputs for setting up environment variables.
aws cloudformation describe-stacks \
--stack-name invoke-lambda-url-iam-auth \
--query "Stacks[0].Outputs" --output json
5.Set up region, Lambda function host, Access, and Secret keys for the created IAM user as environment variables in the test environment.
export AWS_ACCESS_KEY_ID=<Access Key>
export AWS_SECRET_ACCESS_KEY=<Secret Access Key>
export AWS_REGION=<Region>
export LAMBDA_FUNCTION_HOST=<function-url.lambda-url-region.amazonaws.com>
6.Generate AWS Signature v4 and POST request using the generate_sigv4.sh script.
./generate_sigv4.sh
curl -X POST "https://.<url-id>.<region>.on.aws/" -H "Content-Type: application/json" -H "x-amz-date: 20240619T150022Z" -H "Authorization: AWS4-HMAC-SHA256 Credential=<ACCESS-KEY>/20240619/<region>/lambda/aws4_request, SignedHeaders=content-type;host;x-amz-date, Signature=<signarure-content>" -d '{"inputText": "Request to Lambda."}'
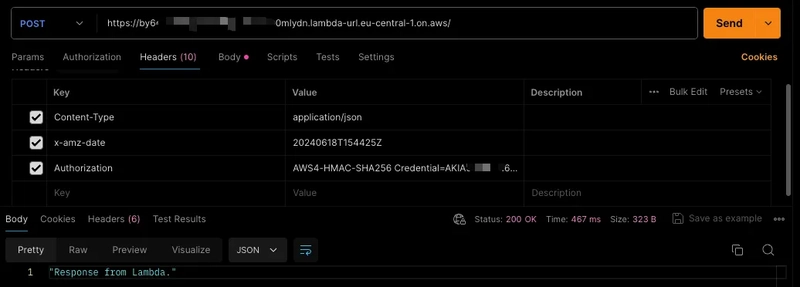
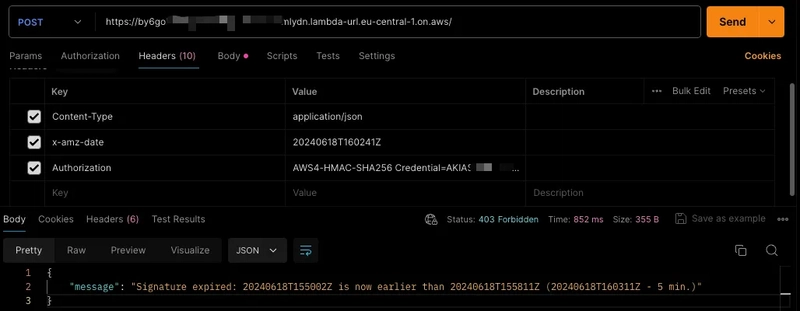
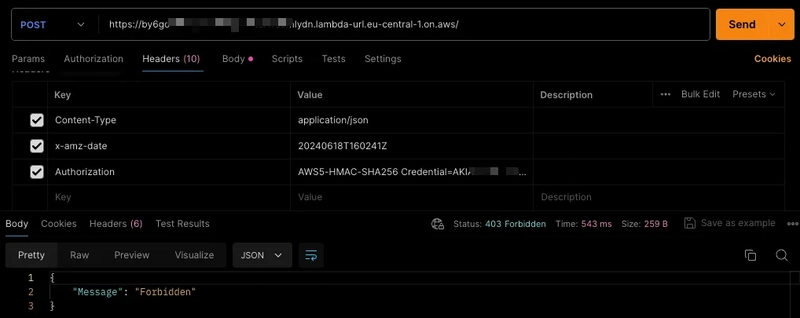
Tests from command line and Postman:
7.Delete the CloudFormation stack.
aws cloudformation delete-stack --stack-name invoke-lambda-url-iam-auth
Conclusion:
This project demonstrates how to securely invoke AWS Lambda functions using Lambda URLs with IAM authentication. Additional security can be added by throttling limits and monitoring the Lambda function with CloudWatch alarms.
If you found this post helpful and interesting, please click the button to show your support. Feel free to use and share this post. 🙂



Top comments (0)