IAM Users
IAM users are an important AWS resources. This is the identity given to a physical user or application when he logs into AWS.
AWS identifies an IAM user with these identifiers.
- Friendly user name: We provide an identifiable user name.
- ARN: An amazon resource name (ARN),
- Access ID: A unique identifier which is returned when working with SDKs or CLIs.
IAM Users | User Permission
The default IAM User permission is non-explicit deny for all AWS services. To provide the user access we can be provided explicit permission in one of these ways.
- Adding a user to a group.
- Copying permission from another user.
- Attaching a policy directly.
IAM Users | Groups
In an organization, it makes sense to group each department into a group and the assign users to these groups.
IAM Users | ARN
ARN (Amazon resource name), is specified in this format.
arn:aws:iam:<region>:<account_id>:user/admin
the IAM user ARN is like this
arn:aws:iam::<account_id>:user/admin
- The
<region>is missing in a IAM user ARN, as IAM is a global service. - The
user/admindefines the actual resource.
IAM Users | Create a new user.
IAM user creation is a 5 step process.
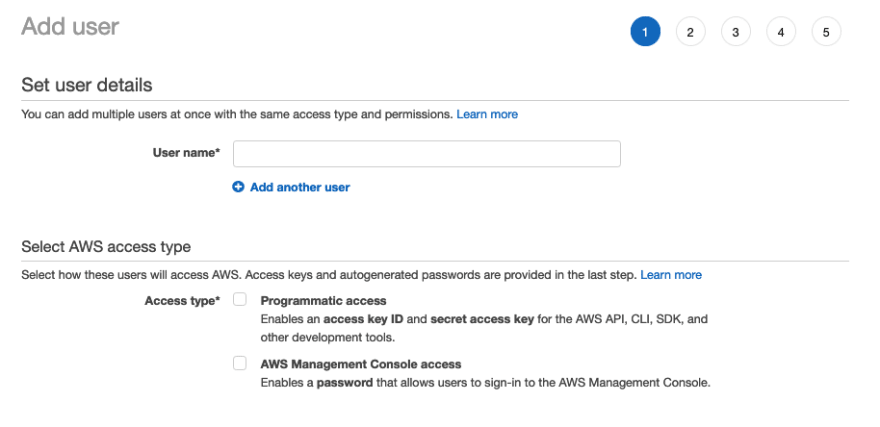
IAM Users | Creation | Step 1 | Add user
The first step in the IAM User creation process is: Add user.
We have to fill a few of the fields. Lets understand these fields.
-
Set user details
- We should provide the user name for the IAM user, mostly a friendly name.
- We can add multiple user in this step.
-
Select AWS access type: There are two ways for the user to access AWS resources
- Programmatic Access : This is to generate the access key ID and secret access key for AWS CLIs, SDKs and other development tools.
- AWS management console access : Creates a user who can log into the AWS console using a password.
- We can mix and match the programmatic access and also management console access.
IAM Users | Creation | Step 2 | Set Permissions
The next step in user creation is to set permissions.
There are 3 ways to add permissions to a user.
- Add user to a group.
- Add the new user to a group based on the job function.
- Copy permission from existing users.
- If we have existing user, we can copy policy for that user.
- Attach existing policies directly.
- We can singularly attach a multiple policy to a user directly, both AWS managed and customer managed.
The most efficient way to add permission to a group of user is to add the user to a group.
IAM Users | Creation | Step 3 | Add Tags
Tags are an important component in all service creation. We can assign a key/value pair to manage user efficiently.
IAM Users | Creation | Step 4 | Review
The penultimate steps of user creation is to review the configuration we have provided. As show in the screen shot above, it displays all the configuration selected till now based on which the user will be created.
IAM Users | Creation | Step 5 | Success
In the last step of user creation it has given these options.
- Download csv

- This CSV gives these details
- User Name
- Password
- Access Key ID
- Secret access key
- These two are provided when we have the programmatic access enabled.
- Console login link
- This is the only time we get the Secret access key along with the access key ID, there is no way to recreate the same secret access key again.
- We also got the some of the above information displayed accordingly the way the user was created.
IAM User Properties
Lets see a few of the properties displayed for the user in the AWS IAM dashboard.
The above screen shot shows that the IAM user summary / property can be grouped into
- Permissions
- Groups
- Tags
- Security Credentials
- Access Advisor
From the above group, the most important to consider is Security credentials.
Permissions
The above screen shot clearly depicts, this property displays the permission present to the user. In the above case, the user gets 2 IAM policy
- Attached directly.
- The IAMUserChangePassword is the policy applied directly to the user.
- Attached from group.
- The Administrator access is attached via the Group.
Groups & Tags
This property depicts the groups and the tags associated with the user.
Access Advisor
There is always a need as an administrator to review user behavior in AWS like the number of services used, the frequency in which it is used. In the Access Advisor tab, IAM provides this information about the user, and helps in identifying the unused permissions.
Security Credentials
The major section of security credentials are
-
Sign-in credentials
- Provides with link to console sign-in link
- Console password: is it enabled or not
- Assigned MFA device: Is the device assigned or not
- Signing certificate: We can upload any specific X.509 certificate for use.
-
Access Keys
- The keys to make programmatic calls to AWS by CLI, SDKs, API calls.
- We can even create an access key from here.
-
SSH Keys for AWS code commit
- SSH public key to access AWS code commit.
-
HTTPS Git credentials for AWS code commit
- User name and password to access AWS code commit
-
Credentials for Amazon keyspaces.
- User name and password to access Amazon Keyspaces.
Conclusion
The AWS IAM user is anybody who will use the login credentials or the programmatic access to AWS. Each IAM user can easily be identified using a friendly name, or a unique ARN or an Access ID. The IAM user can get permission by getting itself attached to a group, or having the policy attached directly or copying from an existing user. Providing permission by adding them to a group is the best IAM policy.
AWS IAM user creation is a 5 step process, but the important steps are only 2, the first one has given a user name to the user, along with the type of access it needs. This is followed by, adding permission to the user, which can be done by attaching it to a group or copying from an existing user or by attaching the policy directly.
The AWS IAM user has specific properties like permission which it has and from where it got the permission, like attached directly or received it from a group. There is a specific property called Access Advisor, which an administrator can use to review if the user is regularly using the permissions or not and depending on that can review to keep the permission or remove it. AWS IAM users also have a property called security credentials, which tells if the user has a password or not and also if MFA is enabled or not, we can also see the access ID but not the key, and we can add the ssh keys for code commit.
Each action done on AWS is done by some type of user.

















Top comments (0)