Introduction¶
You have learned about the AWS Shared responsibility model, Have you stopped and thought, how do you check if your VPC is accessible from outside network? Does my application compromises the EC2 in any regards?
You should remember that network accessibility and software security is the user's responsibility in AWS Shared responsibility model.
Being a beginner using the AWS, this responsibility may seem daunting. No worries, when AWS gives you a challenge, it also shows you the path.
You will learn how can we use an AWS Service to check the security vulnerability of your software. You will also learn how this service helps in checking the network accessibility of the VPC.
Let's dive into the inspected world of AWS Inspector.
What is AWS Inspector?¶
AWS inspector is a service provided by AWS, which helps you in two ways
- Finding security vulnerabilities in your software.
- Checking the network accessibility of the VPCs.
AWS inspector gives findings for the checks done, on which you can act on. You can use the findings and corrects the weakness in your application or the network.
AWS Inspector Agent¶
You should be thinking by now, okay, network assessment can be done via some external tools or service given sufficient permission via the IAM Roles.
How does AWS inspector do a security vulnerability test on an EC2 instance? Is some application is running beyond your knowledge in your own EC2 instance.
The answer to this is, When you enable the AWS Inspector to do a security vulnerability test on your application running on the EC2 instance, it asks permission to install an AWS inspector agent on the EC2 instance.
The AWS inspector agent does software telemetry for application and the OS running on the EC2 instance.
It provides various information about EC2 instance and the application running on it. Installation of this AWS inspector agent is optional.
If installed, AWS inspector agent monitors
- Behavior of the EC2 instance.
- checks the network file system
- process activity
- collects a lot of behavior and configuration data
Benefits of AWS Inspector¶
You have learned that AWS inspector does network assessments and security vulnerability checks on the EC2 instance, is this the only use of the AWS inspector?
No, you do get the other benefits of using the AWS inspector including
-
Automation
- You can integrate the security vulnerability, and network assessments automatically in your CI/CD pipeline.
- This gives your findings if any security or network related check are broken in the upgrade and could be corrected.
-
Application security
- The application security checks also can be automated, providing you with valuable information.
- AWS inspector vulnerability scanning when automated, helps in finding issues which can lead to hacking of your application.
Caution while using AWS Inspector.¶
You shouldn't relax knowing that AWS inspector does both network assessments and security vulnerability test. This should not give you a false sense of security that you will find all types of vulnerability by just running the AWS inspector.
AWS inspector helps in finding some of the security issues with your EC2 instance and application running on it.
AWS Inspector does not find issues in real time by log analysis like an AWS GuardDuty, or AWS Trusted Advisor, which even provides optimization techniques for your architecture.
The application running on the EC2 instance, and it's instance configuration itself poses complexity, which AWS inspector may not be configured for.
We as a user have a responsibility, which we should fulfill by running some complementary test like the AWS GuardDuty or AWS Trusted Advisor.
AWS inspector is part of the security and network monitoring not the heart of it.
AWS Inspector Pricing¶
Pricing is an important parameters while choosing a particular AWS Service, especially when we have 3rd party tools also competing
The AWS inspector pricing is based on these two dimensions.
- Number of EC2 instance included in each assessment.
-
Number of rules invoked in each run.
- Host assessment
- Common vulnerability and exposures ( CVE )
- CVE is a mission which identify, define and catalogs publicly disclosed CyberSecurity vulnerabilities.
- Center for Internet security ( CIS ) benchmarks
- CIS provides more than 100 configuration guidelines across 25+ vendor product families to safeguard systems against today’s evolving cyber threats.
- Security best practices
- Runtime behavior analysis.
- Network assessment
For more detailed pricing report, visit the AWS official pricing page. The pricing on Free Tier is very easy, read along to find out.
Free tier¶
You do not have to bother about all the above complexities, accounts which have never run AWS inspector once, are eligible for
- 250 agent assessments with host rules package
- 250 instance assessments with the network reachability.
In the first 90 days. Other assessments will be billed at the normal price.
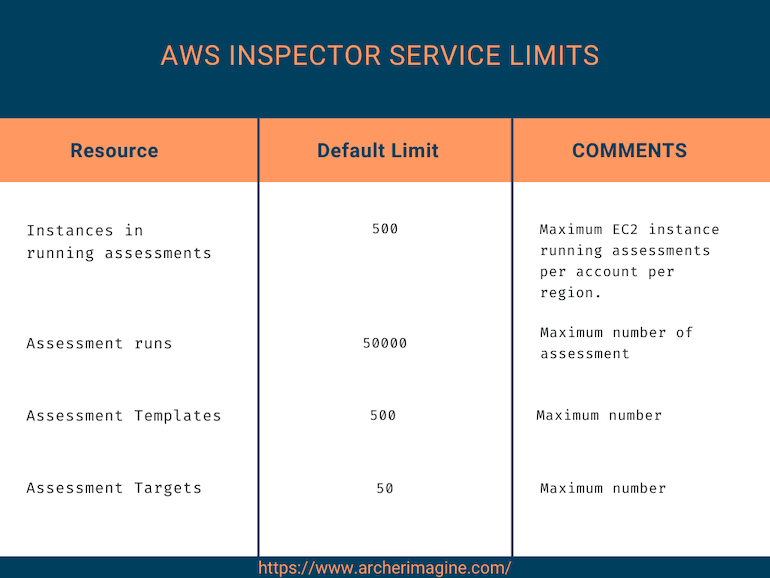
AWS Inspector service limits¶
AWS Inspector has a predefined service limits for different resource you can use. AWS inspector provides these four major categories for resources.
- Number of instance running assessment.
- Number of assessment running.
- Number of various assessment template in every assessment.
- Number of assessment targets
Getting started with Amazon Inspector¶
Let's dive into configuring AWS inspector, and how it can be used.
There are certain prerequisite for starting AWS inspector configuration.
Prerequisite for AWS Inspector¶
- You much have at least one EC2 instance running. What will AWS inspector check if there is no EC2 instance running?
- For Host assessment, you may need to install the AWS inspector agent on the EC2 instance.
Lets first see how to configure AWS Inspector.
You can see that AWS inspector uses a service-linked role , to describe the EC2 instance and network configuration.
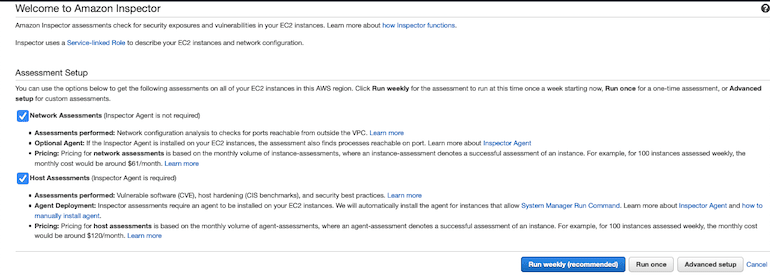
You can see there are two types of AWS inspector setup we can do.
- Network Assessment (Inspector Agent is not required.)
- Host Assessment (Inspector Agent is required.)
The default option is the most easiest configuration to trigger AWS Inspector. Let us understand Network Assessment and Host Assessment.
Network Assessment¶
The checks performed by AWS inspector without the installation of an agents are
- Network configuration analysis to checks which ports are reachable from outside of the VPC.
If you have the AWS inspector agents installed , it can provide you with additional information like,
- The process whose ports are reachable from outside of the VPC.
Host Assessment¶
Host assessment requires the installation of the AWS inspector agent, so once it is installed we get this information
- Common vulnerability and exposures (CVE)
- The host is checked towards the know CyberSecurity vulnerabilities.
- Center for Internet security (CIS) benchmarks
- Security best practices
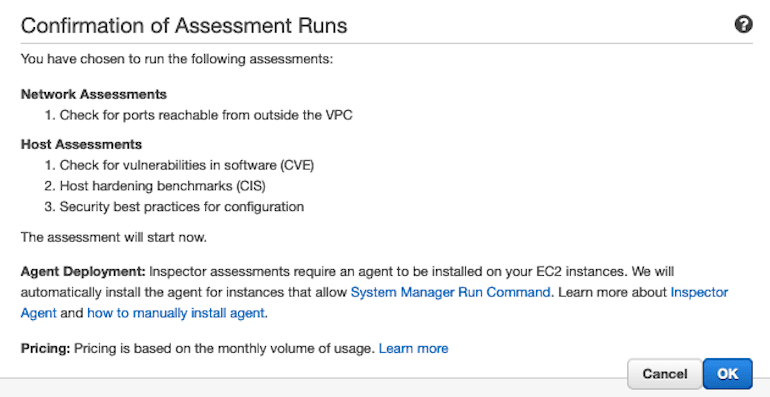
Once you click on Run Once , the confirmation screen is displayed like this.
When we complete the test, we will receive a findings from the test. Before looking into findings, lets see there is an Advanced setup.
AWS Inspector | Advanced Setup¶
As shown in this screen, advance setup is a three step process.
- Define an assessment target
- Define an assessment template
- Review.
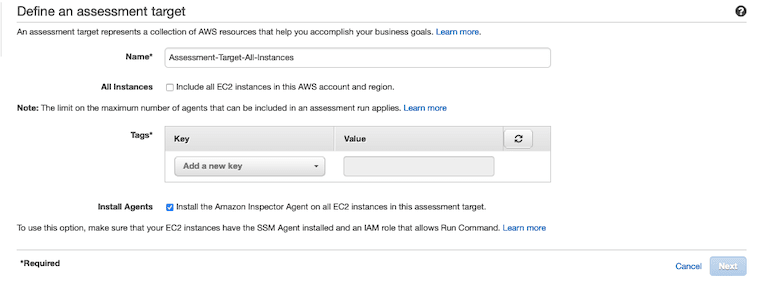
Advance Setup | Define an assessment target¶
You might have guessed by now, an assessment, target is the AWS resources on which you can run the AWS inspector. As of now it is restricted by the operating system and region.
Network reachability test can be run on any EC2 instance without using the AWS inspector agent.
For running the assessment with an AWS inspector agent let us first check the supported Linux based operating systems.
- 64-bit x86 instance
- Amazon Linux 2
- Ubuntu
- Debian
- Red Hat Enterprise Linux
- CentOs
- ARM instance
- Amazon Linux 2
- Red Hat Enterprise Linux
- Ubuntu
The supported Windows operating systems are
- Windows Server 2019 Base
- Windows Server 2016 Base
- Windows Server 2012 R2
- Windows Server 2012
- Windows Server 2008 R2
The supported AWS regions are
- US East (Ohio) us-east-2
- US East (N. Virginia) us-east-1
- US West (N. California) us-west-1
- US West (Oregon) us-west-2
- Asia Pacific (Mumbai) ap-south-1
- Asia Pacific (Seoul) ap-northeast-2
- Asia Pacific (Sydney) ap-southeast-2
- Asia Pacific (Tokyo) ap-northeast-1
- Europe (Frankfurt) eu-central-1
- Europe (Ireland) eu-west-1
- Europe (London) eu-west-2
- Europe (Stockholm) eu-north-1
- AWS GovCloud (US-East) gov-us-east-1
- AWS GovCloud (US-West) gov-us-east-2
The first task of defining the assessment, target is to give it a name.
Then you have an option to run it on all EC2 instances in your account, or you can run it based on certain tags on the EC2 instance. Generally, we can run these assessments only on the production tagged system.
The AWS inspector agent is pre-installed on Amazon Linux AMIs. If you want to install on other AMIs manually you may have to uses AWS System Manager service. Best option is to use the install the agent automatically.
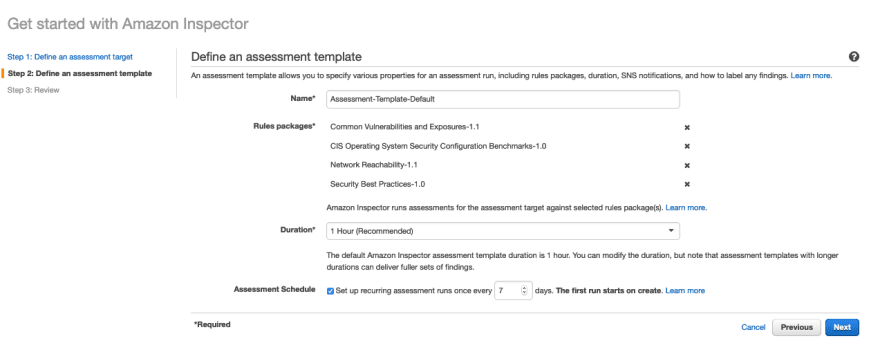
Advanced Setup | Define an assessment template¶
As shown below,
The first task is to Name the assessment templates. Once done, we have to define the rules packages to use. By default, there are 4 rules packages to select.
- Common Vulnerabilities and Exposures-1.1
- CIS Operating System Security Configuration Benchmarks-1.0
- Network Reachability-1.1
- Security Best Practices-1.0
Once you select which of these 4 rules you want to run, next selection to be done is the duration of the test.
In addition, you also also schedule the assessment to be recurring.
The findings of these assessments can also be fed to an SNS topic.
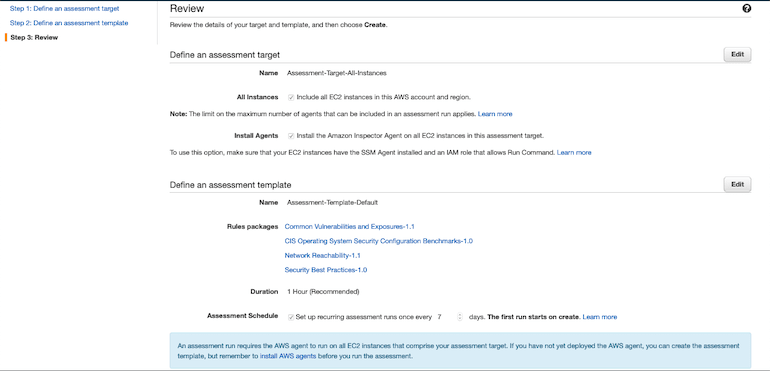
Advanced Setup | Review¶
As you might have seen many a times, the final step is the Review step.
Post all this you can just run the inspector assessment.
AWS Inspector Findings¶
Once you run any AWS inspector assessment, the result is called Findings. These are the potential security issues that AWS inspector has found during its assessment. Findings is not generated while the assessment is on going, it is only generated after the assessment is completed.
Individual findings from AWS Inspector cannot be deleted. You have to delete the completed assessment run.
Conclusion¶
AWS works in Shared responsibility model. In this model, as a user of AWS services you have certain responsibility. Two of them primarily are.
- Check the network reachability of the VPCs.
- Check the application's security running on the VPCs.
It would have been very difficult for you to accomplish this on your own. Just like for many other services, AWS has provided a managed service for this called the AWS Inspector.
AWS Inspector is a managed service which helps in finding security vulnerabilities in the application running on your EC2 instance and also checks if the instance's VPC is reachable from outside.
If we install an AWS inspector agent using the AWS system manager service, then we get additional telemetry about the application running on the EC2 instance.
You should not get a false sense of security thinking that AWS inspector will find all types of security vulnerabilities, It finds some, but it still does not find all the different possible vulnerabilities, it will be in your best interest to find some other alternatives to test complete security vulnerabilities.
AWS inspector has a limitation today on the type of resources it can evaluate, like it can evaluate the security vulnerabilities of an application on an EC2 instance running selective Linux and windows operating system. Though you can use its network reachability test for any type of hardware.
AWS inspector provides 250 agent and instance, assessment for the free tier, and then normal pricing.
Before running AWS inspector you should at least have 1 instance running and the agent should be installed.
You can use the most basic configuration to trigger the assessment which does both types of checks. The report or findings of the test, inform you about the vulnerabilities in different form.
AWS inspector is a great tool for doing the self evaluation of the application running on the EC2 instance, and also check the network reachability.
Info graphics¶
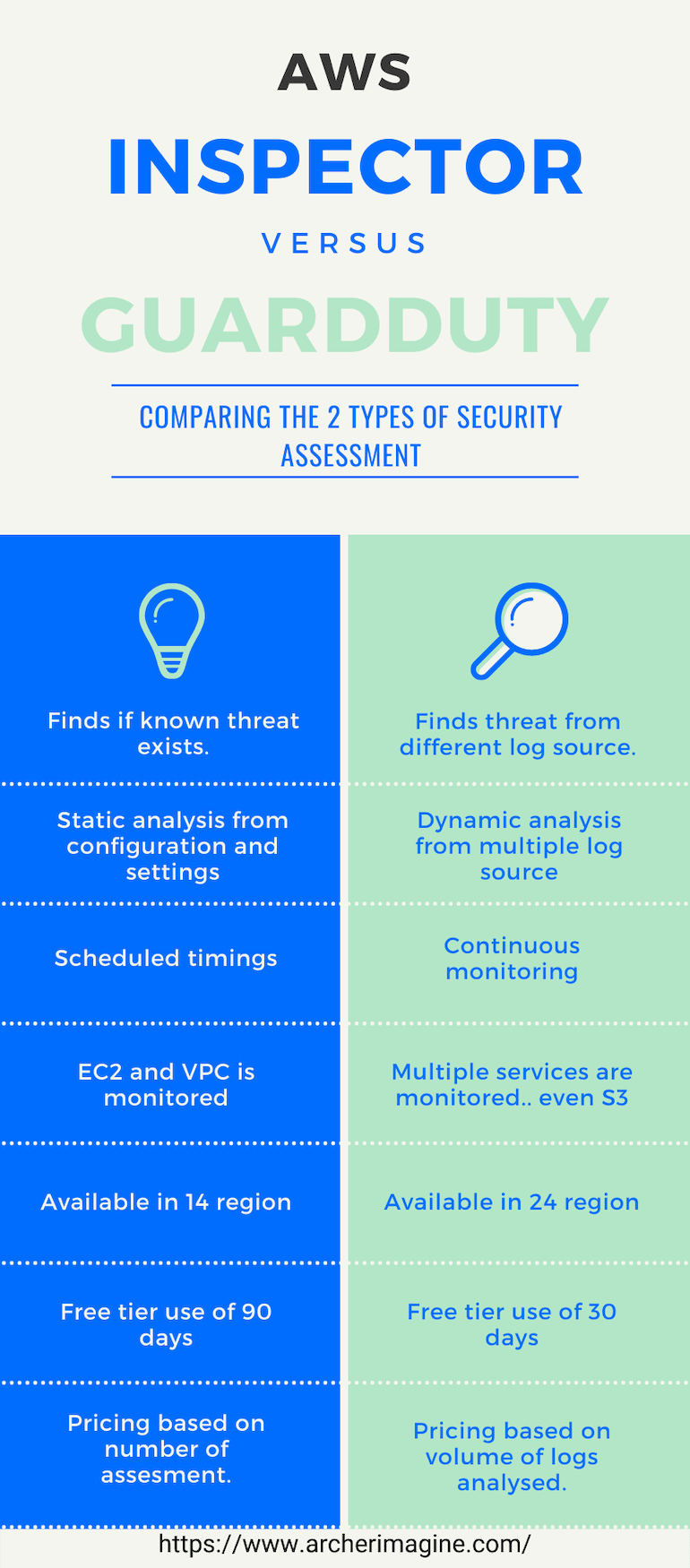
AWS Inspector Vs AWS GuardDuty¶
| AWS Inspector | AWS GuardDuty |
|---|---|
| Finds if known threat exists. | Finds threat from different log source. |
| Static analysis from configuration and settings. | Dynamic analysis from multiple log source. |
| Scheduled timings. | Continuous monitoring |
| EC2 and VPC is monitored | Multiple services are monitored.. even S3 |
| Available in 14 region | Available in 24 region |
| Free tier use of 90 days | Free tier use of 30 days |
| Pricing based on number of assessment. | Pricing based on volume of logs analysed. |
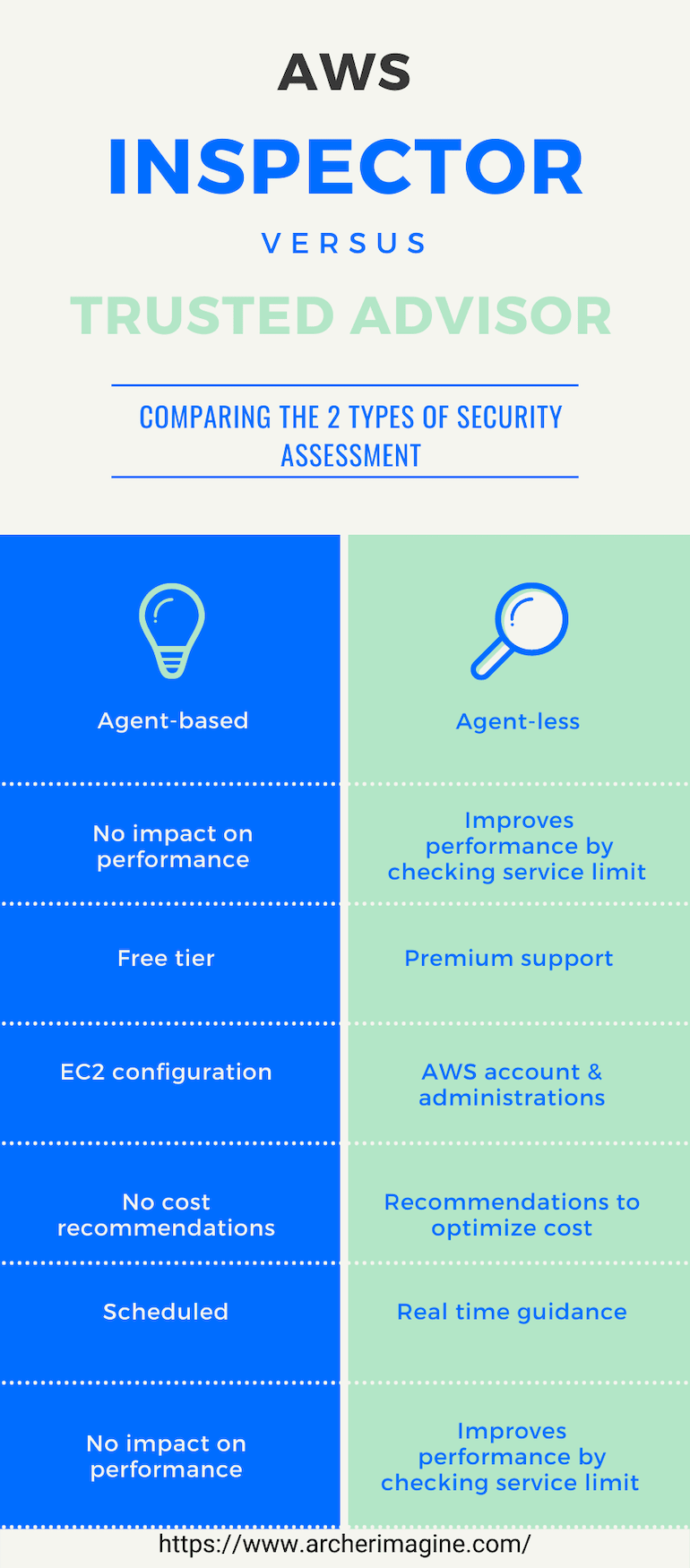
AWS Inspector Vs AWS Trusted Advisor¶
| AWS Inspector | AWS Trusted Advisor |
|---|---|
| Agent-based | Agent-less |
| No impact on performance | Improves performance by checking service limit |
| Free tier | Premium support |
| EC2 configuration | AWS account & administrations |
| No cost recommendations | Recommendations to optimize cost |
| Scheduled | Real time guidance |
| No impact on performance | Improves performance by checking service limit |
Reference¶
- How do I set up Amazon Inspector to run security assessments on my Amazon EC2 instances?
- AWS re:Invent 2015 | (SEC324) New! Introducing Amazon Inspector.
- AWS Hands on Lab - Amazon Inspector.
- AWS Tutorial - Amazon Inspector - Overview.
- What Is Telemetry? How Telemetry Works, Benefits of Telemetry, Challenges, Tutorial, and More.
- Amazon Inspector supported operating systems and Regions
- Amazon Inspector, Security Vulnerability Assessment Service Now Generally Available.
- What is Amazon Inspector?
- Getting started with Amazon Inspector.
- Amazon Inspector assessment templates and assessment runs
- 6 AWS Services for Cloud Security Detection.
- Amazon Inspector for beginners
- AWS trusted adviser vs Inspector
- AWS Trusted Advisor vs. AWS Config vs. AWS Inspector
- Difference between AWS Inspector and AWS Trusted Advisor
Let me know if you run the AWS inspector assessment on your EC2 instance, and what are its findings 👇.








Top comments (0)