As a DevOps engineer, your primary focus is automation, constantly seeking new opportunities to improve the efficiency of your organization's deployments. However, it's important not to overlook the automation and security of your credentials, which are often underestimated. By automating the management and protection of your credentials, you can ensure the security and integrity of your organization's sensitive data, while freeing up valuable time and resources for other critical tasks. So, in addition to streamlining your deployment processes, make sure to prioritize the automation and security of your credentials to maintain a secure and efficient DevOps environment.
In a DevOps environment, you likely have a pipeline within an orchestration tool such as Jenkins that executes custom logic to carry out deployments. To execute these deployments to an organization or environment, credentials must be passed into the orchestration tool.
With the Akeyless API, you can easily manage these credentials with native plugins and automatic secrets migration tools. These tools can import credentials from your current repository or vault and seamlessly inject them into your CI/CD workflows and configuration management processes. This saves time and ensures the secure management of your organization's sensitive information throughout the entire deployment process.
 (Source)
(Source)
By installing Akeyless into your Kubernetes cluster, you can manage your application through the use of a Kubernetes operator. After installation, you can create a vault that will allow you to manage your encryption keys and secrets through the Akeyless CLI or API. Once your vault is set up, you can begin adding your desired encryption keys and secrets to further streamline your security management process.
You can then use Akeyless in your K8s manifests to access your encryption keys and secrets in your containerized applications. Akeyless provides access to the keys and secrets through Kubernetes Secrets and ConfigMap.
Let's paint this picture further with an example of an organization facing issues surrounding manual credential management. Let's call this organization Bob's Financial Services or BFS for short.
As one of the top financial creditors in existence, BFS is struggling with its need to securely manage and rotate secrets, such as API keys, passwords, and certificates, for their DevOps pipelines. However, they have just scaled their business through Kubernetes and their manual processes for managing secrets are now time-consuming and error-prone. Not to mention, the auditing team is not happy about them storing secrets in plaintext or unsecured files.
Some of the issues BFS is facing manually securing its K8s cluster are:
K8s Complexity: Securing K8s clusters is difficult without sufficient expertise and resources due to their complex distributed nature.
Configuration management: Securing a K8s cluster involves managing configuration, monitoring for vulnerabilities, enforcing security policies, and access controls.
Threat detection: Securing a K8s cluster is a continuous process that involves constant monitoring, analysis, and mitigation of security threats, including detecting breaches, identifying vulnerabilities, and implementing countermeasures that can't be maintained under manual processes.
Compliance: Meeting compliance requirements like HIPAA or PCI in a K8s environment involves implementing relevant security controls, logging and auditing practices, and access controls, which can be challenging if not automated.
After a brainstorming session, one of the DevOps engineers brings forth the Akeyless solution to manage secrets in their pipeline and Kubernetes cluster. The engineer emphasizes that Akeyless is a central repository for secrets accessed using multi-factor authentication and role-based access control. The plan to implement Akeyless is as follows:
- First add the Akeyless helm repository to the K8s environment
- With the repository added, install Akeyless Secrets Injection store chart
- Now use the Akeyless Secrets Injection Store to inject secrets into the Kubernetes pods. To do this, Kubernetes secrets that reference the Akeyless Secrets Injection Store are needed
- Create a Kubernetes target in Akeyless that will store the Kubernetes API servers access credentials, such as the server address, certificate, and token
- In Jenkins, install the Akeyless Jenkins plugin for integration
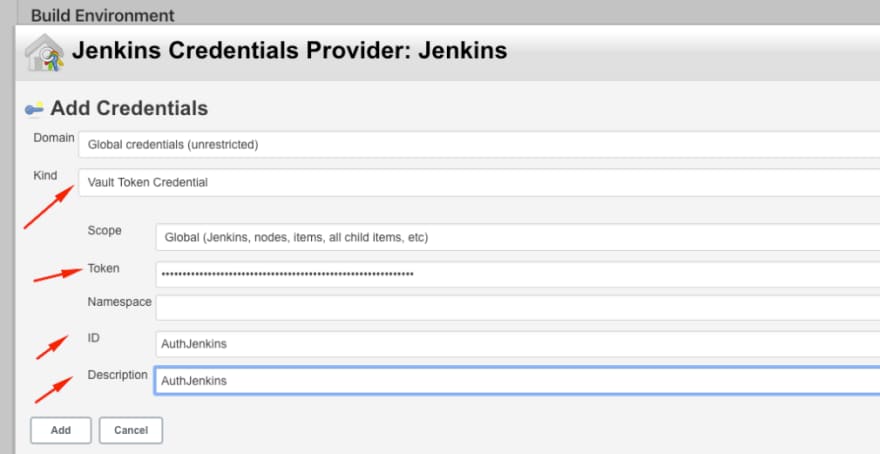 (Source)
(Source)
- Create a Jenkins credential in Akeyless that will store the Kubernetes API servers access credentials, such as the server address, certificate, and token. This credential will be used in the Jenkins pipeline for deploying to Kubernetes
- In the Jenkins file, add the Akeyless credential binding for the Kubernetes API server access credentials
- Update the Kubernetes deployment configuration file to reference the Kubernetes secrets stored in Akeyless. This can be done by replacing the static secret references with the dynamic references to the secrets stored in Akeyless
- In the Jenkins pipeline, add the deployment step that applies the Kubernetes deployment configuration
The implementation plan above for Akeyless will ultimately put BFS in a more sustainable, secure, and compliant environment when it comes to credential management versus their old manual human intervention dependent culture.
Of course, this is only one way of implementing Akeyless into a DevOps process within a multi-cloud environment, but as we know there is always more than just one way home. Depending on your current infrastructure, Akeyless can also integrate with many other DevOps tools, such as Jenkins, GitLab, or GitHub Actions, to retrieve secrets at runtime. Akeyless can also automatically rotate secrets on a schedule or in response to security events, such as a suspected breach, which is another article all on its own. This ensures that the organization's DevOps pipeline is always using up-to-date and secure secrets.
In summary, Akeyless offers a comprehensive and secure secrets management solution for organizations utilizing DevOps and Kubernetes. By automating secrets management, Akeyless helps to reduce the risk of data exposure, improves collaboration and auditability. With strong encryption and granular access controls Akeyless provides a reliable platform for managing sensitive data.







Top comments (0)