To secure our AWS Cloud setup we use quite some tools: AWS Security Hub, AWS Inspector, AWS Guardduty and ECR Vulnerability Scanning just to name a few.
All these tools are both easy to set up and do a very nice job finding weaknesses and treats. The only issue I had, is that often their findings stayed under the radar way too long. I'm not the person to check all these dashboards on a daily basis for new findings, I simply forget to do so.
Chatops
On the other side, we heavily use Slack for chat and notifications from build pipelines, service changes, system errors, etc. All these notifications are collected in a dedicated room for which a company policy dictates those should be all read.
So ideally, we just had to add our security notifications to the same chatroom to get notified and to never miss a security issue again.
AWS Eventbridge, AWS SNS and AWS Chatbot
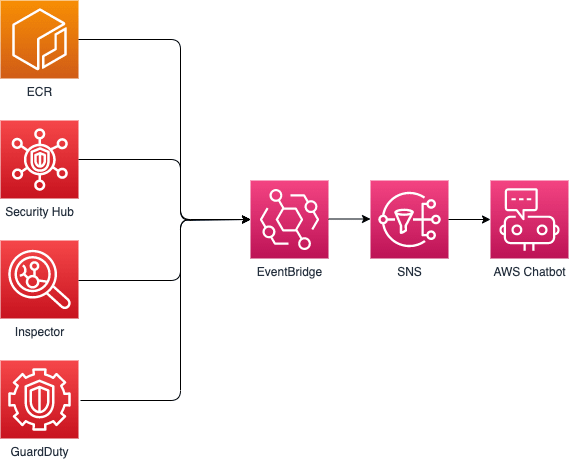
It turns out that showing all your security findings and alerts in your chat client is quite easy. This is how our setup looks like:
Using AWS Eventbridge, we collect all notifications on a single SNS topic named 'security-issues'. On top of that AWS Chatbot is configured to listen to that SNS topic and to forward all messages to Slack.
Creating the SNS Topic and setting up AWS Chatbot to listen to the SNS Topic and forward the messages to your chat client is very easy and done in a few clicks. The hardest part is capturing the EventBridge events and forwarding them to SNS, so here the CloudFormation to help you out on that part:
AWSTemplateFormatVersion: '2010-09-09'
Description: Forward EventBridge security events to AWS SNS
Parameters:
SecurityIssuesSnsTopic:
Type: String
Description: Contains the ARN of the SNS topic on which security issues are published.
Resources:
GuardDutyEventRule:
Type: AWS::Events::Rule
Properties:
Name: detect-guardduty-findings
Description: A CloudWatch Event Rule that triggers on Amazon GuardDuty findings.
State: ENABLED
EventPattern:
source:
- aws.guardduty
detail-type:
- GuardDuty Finding
Targets:
- Arn:
Ref: SecurityIssuesSnsTopic
Id: SecurityTopic
SecurityHubFindingEventRule:
Type: AWS::Events::Rule
Properties:
Name: detect-securityhub-findings
Description: A CloudWatch Event Rule that triggers on Amazon Security Hub findings.
State: ENABLED
EventPattern:
source:
- aws.securityhub
detail-type:
- Security Hub Findings - Custom Action
resources:
- !Sub arn:aws:securityhub:${AWS::Region}:${AWS::AccountId}:action/custom/reportfindings
Targets:
- Arn:
Ref: SecurityIssuesSnsTopic
Id: SecurityTopic
SecurityHubInsightsEventRule:
Type: AWS::Events::Rule
Properties:
Name: detect-securityhub-insights
Description: A CloudWatch Event Rule that triggers on Amazon Security Hub insights.
State: ENABLED
EventPattern:
source:
- aws.securityhub
detail-type:
- Security Hub Insight Results
resources:
- !Sub arn:aws:securityhub:${AWS::Region}:${AWS::AccountId}:action/custom/reportfindings
Targets:
- Arn:
Ref: SecurityIssuesSnsTopic
Id: SecurityTopic
EcrVulnerabilitiesEventRule:
Type: AWS::Events::Rule
Properties:
Name: detect-ecr-vulnerabilities
Description: A CloudWatch Event Rule that triggers on Amazon ECR vulnerabilities.
State: ENABLED
EventPattern:
source:
- aws.ecr
detail-type:
- ECR Image Scan
detail:
finding-severity-counts:
CRITICAL:
- exists: false
- numeric: [ ">", 0 ]
HIGH:
- exists: false
- numeric: [ ">", 0 ]
MEDIUM:
- exists: false
- numeric: [ ">", 0 ]
# UNDEFINED:
# - exists: false
# - numeric: [ ">", 0 ]
Targets:
- Arn:
Ref: SecurityIssuesSnsTopic
Id: SecurityTopic
This should get you started in a matter of minutes 😄
Here's how the result looks like in Slack. Pretty neat, isn't it!?
Currently, all of the above message types are supported by AWS Chatbot except for the ECR Vulnerabilities. Hopefully this changes in the near future (for now I also have an email subscription on the SNS Topic to cover those).
Enjoy and until next time!








Top comments (0)