In this blog the objective in the AWS environment, utilizing policies and roles in the IAM console to restrict access to AWS resources and conclude by assuming a role and ensuring our policies are correct and that we have completed all objectives.
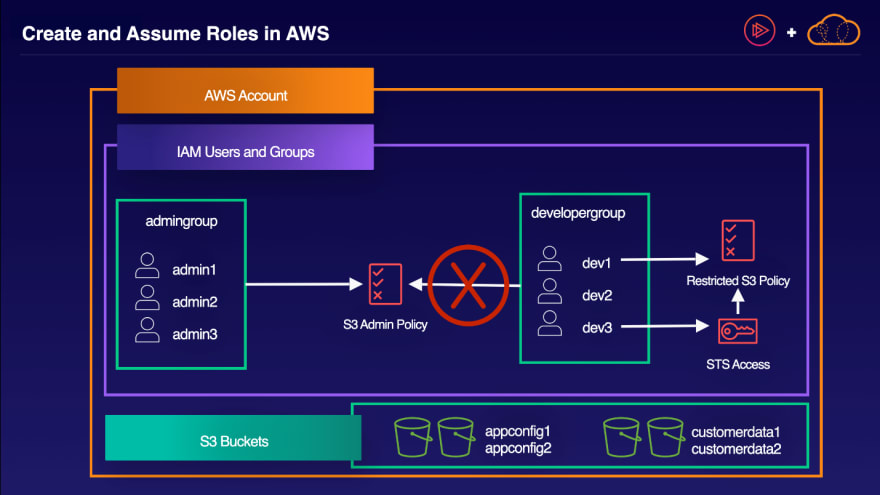
Image: ACloudGuru
Create the Correct S3 Restricted Policies and Roles
- Create the S3RestrictedPolicy IAM policy. Ensure only the appconfig buckets are accessible.
- Select the S3 service and all S3 actions
- Select all resources except bucket
- Add the appconfig bucket names to the policy
- Create the S3RestrictedRole IAM role.
- Set the trusted entity to another AWS account
- Add your account ID
- For permissions, select the S3RestrictedPolicy
- Revoke the AmazonS3FullAccess access policy from the developergroup.
- Attach the S3RestrictedPolicy to the dev1 user.
Configure IAM So the dev3 User Can Assume the Role
- Create the AssumeS3Policy IAM policy.
- Select the STS service
- Select AssumeRole under the write options
- Add the S3RestrictedRole
- Attach the AssumeS3Policy to the dev3 user.
- Assume the S3RestrictedRole as the dev3 user.
- Log in as the dev3 user
- Switch roles to the S3RestrictedRole
- Verify access in S3






Top comments (0)