When your company becomes an AWS ally through the AWS Partner Network program (APN), your team must go through several stages to demonstrate their knowledge and experience in analyzing and identifying potential opportunities for enhancing customers' environments.
To complete the essential stages, it is necessary to carry out a Foundational Technical Review (FTR).
What is Foundational Technical Review?
The Foundational Technical Review (FTR) is a kind of examination done by Amazon Web Services (AWS) to check how well a solution offered by an AWS Partner is working. This examination looks at how well the partner is following the best methods recommended by AWS in areas like:
- Keeping things safe
- Making things run fast
- Managing day-to-day operations
All of this is super important to make sure customers are happy with the service they get.
To meet the FTR criteria for a software product that includes a Partner Hosted part on AWS, you need to provide two things:
- An automatically generated security report
- Self-assessment form
These documents should include information about all the AWS accounts used for handling customer data.
Passing the FTR is a must for AWS Software Partners if they want to join different AWS Partner Network (APN) programs, like AWS Competency and AWS Service Ready.
Some of the required CIS AWS Foundations Benchmark Controls for your FTR to be approved are:
- CIS 1.5/Security Control IAM.9 - Ensure MFA is enabled for the 'root' user account
- CIS 1.4/Security Control IAM.4 - Ensure no 'root' user account access key exists
- CIS 1.10/Security Control IAM.5 - Ensure multi-factor authentication (MFA) is enabled for all IAM users that have a console password
- CIS 1.14/Security Control IAM.3 - Ensure access keys are rotated every 90 days or less
- CIS 1.16/Security Control IAM.1 - Ensure IAM policies that allow full "*:*" administrative privileges are not created
- CIS 5.3/Security Control EC2.2 - Ensure the default security group of every VPC restricts all traffic
- CIS 5.1/Security Control EC2.21 - Network ACLs should not allow ingress from 0.0.0.0/0 to port 22 or port 3389
Are you wondering what the purpose of this introduction is? Well, let me explain. Today, we are here to learn about AWS SecurityHub, a crucial tool for successfully completing the FTR.
What is AWS SecurityHub?
Security Hub is a service that helps manage the security of your Amazon Web Services (AWS) resources. It does this by regularly checking if you're following the best security practices automatically. With Security Hub, you can get a single security score that shows how well you're doing in terms of security across all your AWS accounts and regions. It also checks the security of your AWS resources by looking at things like the AWS Foundational Security Best Practices and other rules set by compliance frameworks.
How does AWS SecurityHub work?
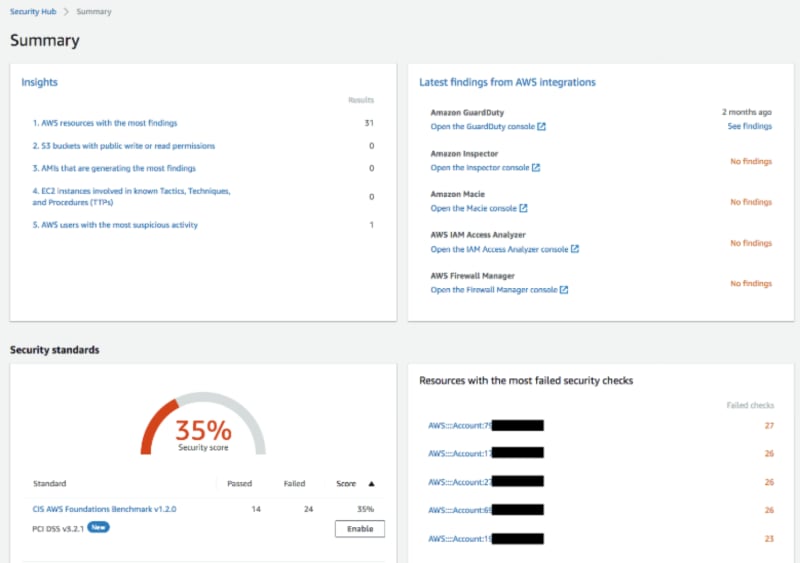
Security Hub does a couple of important things. It checks if you're following good security practices, and it also collects security information from AWS services and partner tools. It takes all this information and puts it together so that you can see a complete picture of your security situation. You get useful dashboards that show all the security findings, and it even suggests ways to fix any problems it finds. Sounds powerful, doesn't it?
Dashboard-Sample
By now, I hope you recognize the importance of AWS SecurityHub, whether you're an APN partner or anyone looking to safeguard their AWS setup.
The million-dollar question.
How much does AWS SecurityHub cost?
Security Hub's pricing is based on two things: how many security checks you run and how many security findings you collect each month.
You can also give Security Hub a test run for free with a 30-day trial on the AWS Free Tier. During this trial, you get access to all of Security Hub's features and the security checks it offers. When you activate Security Hub in each AWS account and region, you get this free trial, and it gives you an idea of what your monthly bill might be if you decide to keep using Security Hub in those same accounts and regions.
Congratulations on completing reading this blog and I hope you enjoyed it. Now it's time for you to take a well-deserved break. Why not grab a cup of coffee or take a refreshing walk outside?
Please stay tuned, and I invite you to subscribe to this blog to receive an alert 🚨 notifying you when I have added the repository section. In the meantime, you can have a look at my 20+ available projects here:.
🚨Here's the link to the repository section of this blog!🚨
I'm all set to resume building on AWS. Are you ready too?
The GitHub repository and deployment instructions for this project is available at the link below. With hands-on experience, you can learn how to deploy a complete AWS SecurityHub account with just a few commands.
Code previews
#--securityhubmain--
resource "aws_securityhub_account" "x_securityhub" {
}
resource "aws_securityhub_finding_aggregator" "findind_security_issues" {
linking_mode = var.regions
depends_on = [aws_securityhub_account.x_securityhub]
}
Please don't forget to share your comments and follow me for more AWSome content.







Top comments (0)