Multi-factor for time-bound elevation
- Azure MFA is the two-step verification solution from Microsoft
- Azure MFA supplies added security for your identities by requiring two or more elements for full authentication
- These elements fall into three categories:
- Something you know: password or answer to security question
- Something you possess: mobile app or token device
- Something you are: biometric property such as fingerprint
- Using Azure MFA increases identity security by limiting the impact of credential exposure
Azure MFA comes as part of the following offerings:
- Azure Active Directory Premium licenses
- Azure MFA Service (Cloud)
- Azure MFA Server
- Multi-Factor Authentication for Microsoft Office 365
- Azure Active Directory Global Administrators

Understand users and groups
- In Azure AD, every user who needs access to resources needs a user account
- Azure AD defines users in three ways:
- Cloud identities
- Directory-synchronized identities
- Guest users
- You can add cloud identities to Azure AD by using:
- Azure portal
- Azure PowerShell

- A group helps organize users to make it easier to manage permissions
- There are two types of groups:
- Security groups
- Distribution groups
- There are two ways to add members to Azure groups:
- Directly assigned
- Dynamically assigned

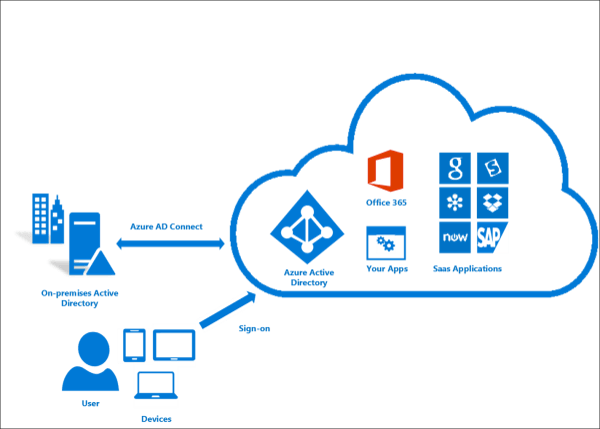
Install and configure Azure AD Connect
- Azure AD Connect integrates your on-premises directories with Azure Active Directory
- This integration allows you to provide a common identity for your users for Office 365, Azure, and SaaS applications integrated with Azure AD in a hybrid identity environment
- Azure AD Connect provides:
- Sync Services
- Health monitoring
- Active Directory Federation Services (AD FS)
- Password hash synchronization
- Pass-through authentication
Manage Azure AD directory roles
- Azure AD provides many built-in roles to address the most common security scenarios
- These roles include:
- Owner: has full access to all resources including the right to delegate access to others
- Contributor: can create and manage all types of Azure resources but can’t grant access to others
- Reader: can view existing Azure resources
- Each role is a set of properties defined in a JavaScript Object Notation (JSON) file, which includes:
- Name, ID, and Description
- Allowable permissions (Actions), denied permissions (NotActions), and scope (read access, etc.) for the role
Configure authentication methods
Microsoft highly recommends that administrators enable users to select more than the minimum required number of authentication methods, in case they do not have access to one method
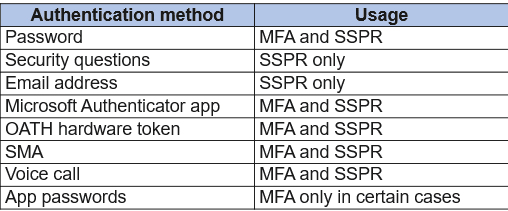
You can use the following authentication methods with Azure AD:
- Password
- Security questions
- Email address
- Microsoft Authenticator app
- OATH hardware tokens
- Mobile phone
- App password
Manage app registration
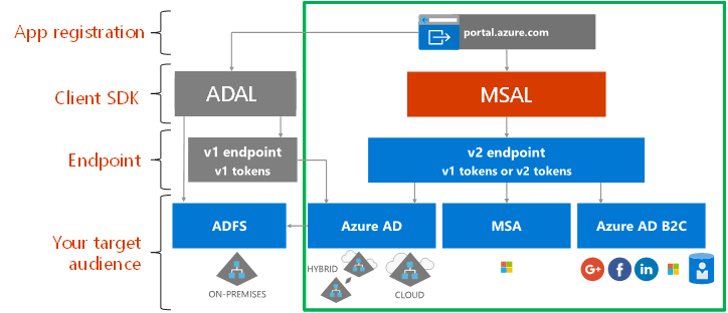
- The Microsoft identity platform is an evolution of the Azure AD identity service and developer platform
- The Microsoft identity platform has two endpoints (v1.0 and v2.0) and two sets of client libraries to handle these endpoints
- Azure AD supports five primary application scenarios:
- Single-page application (SPA)
- Web browser to web application
- Native application to web API
- Web application to web API
- Daemon or server application to web API
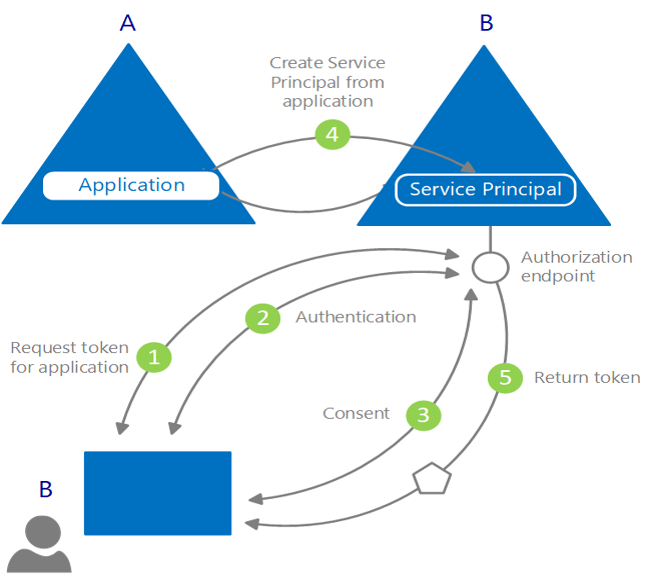
- Any application that outsources authentication to Azure AD must be registered in a directory
- Registration involves telling Azure AD about the application, including the URL where it’s located, the URL to send replies to after authentication, the URI to identify your application, and more
- Azure AD represents applications following a specific model that's designed to fulfill two main functions
- Identify the app according to the authentication protocols it supports
- Handle user consent during token request time and facilitate the dynamic provisioning of apps across tenants






Top comments (0)