A single sign-on solution is the holy grail of security for any enterprise, allowing users to log in once and then access multiple systems with a minimum amount of hassle.
In this article we will learn how to integrate Open edX with Auth0 in order to provide single-sign on.
There are many different advantages for using the system including passwordless sign up and logins, as well as easy management of user accounts.
Create an Auth0 account
Visit Auth0 Signup page and pick your preferred method to create an account there.
Default Tenant
After creating your account in Auth0 they automatically create a tenant for you. For this article we use the default tenant but if you need to change tenant name or region for your production site feel free to do it.
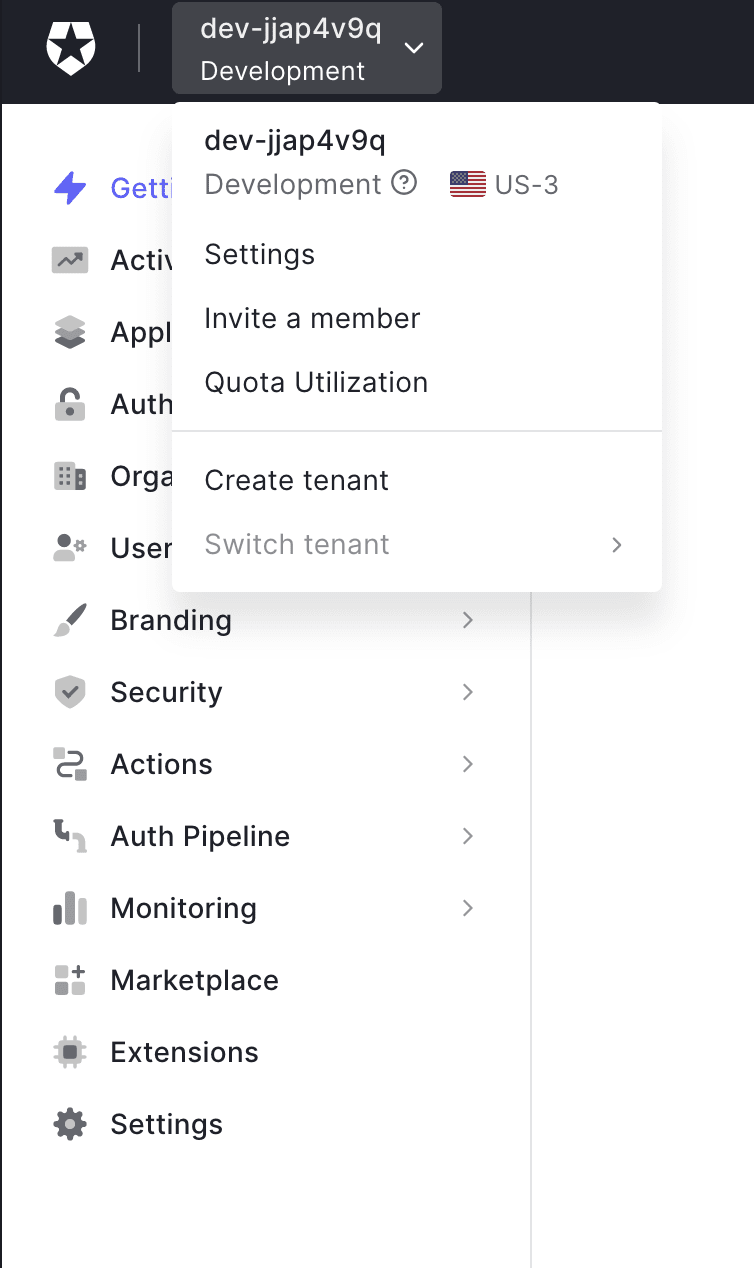
dev-jjap4v9q is my default tenant name in US region.
Create an application
-
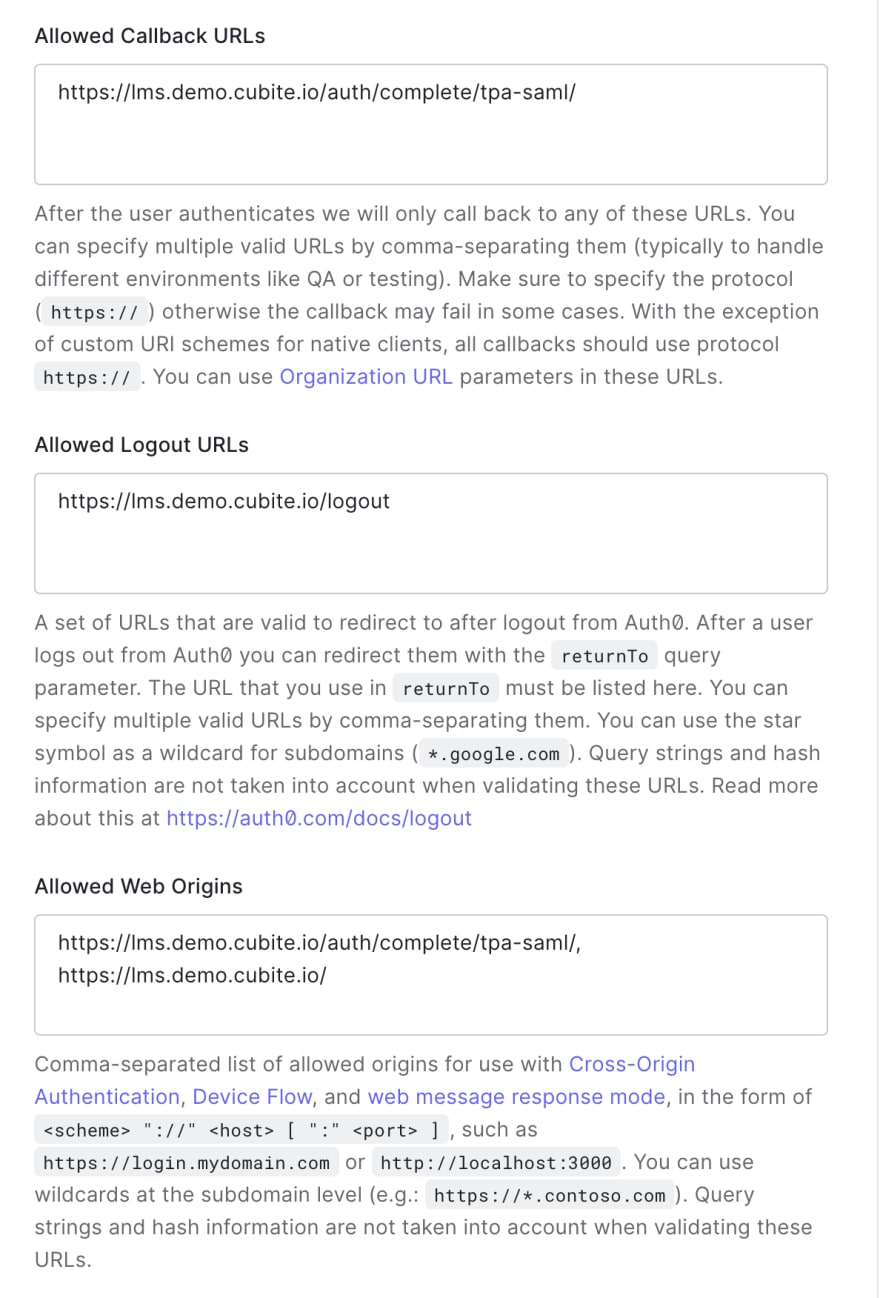
Allowed Callback URLs: [LMS-URL]/auth/complete/tpa-saml/ -
Allowed Logout URLs: [LMS-URL]/logout -
Allowed Web Origins: [LMS-URL]/auth/complete/tpa-saml/, [LMS-URL] - Allowed Origins (CORS): [LMS-URL]/auth/complete/tpa-saml/, [LMS-URL]
Enable SAML Addon
In the addons choose SAML2 and in settings tab click on enable button.
Download the
Identity Provider Metadataand upload it to your S3 or somewhere else to get publicly accessible link
Open edX Setup
Add SAML Configuration
First run openssl req -new -x509 -days 3652 -nodes -out saml.crt -keyout saml.key in command line.
Go to [LMS-URL]/admin/third_party_auth/samlconfiguration/add/ and create new configuration like following

- The
slugshould be set asdefault - The
Private key:should be content of the saml.key file - The
Public key:should be content of saml.crt file - It's recommended to set the entity id as the Auth0 issuer id you have in auth0 addons for SAML
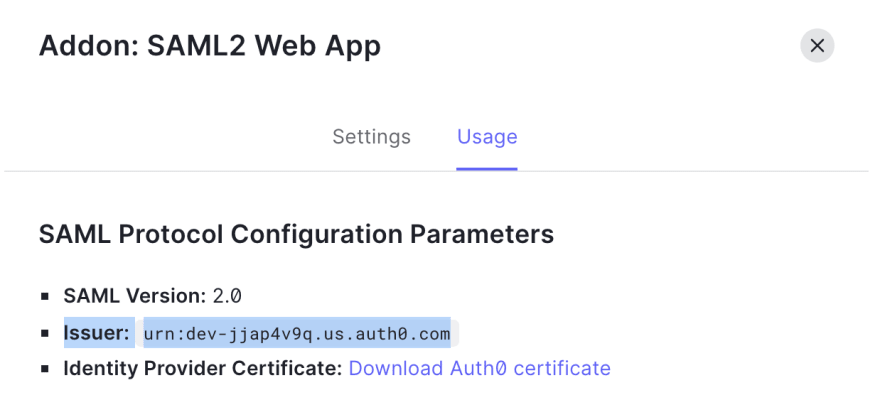
Add SAML IDP
Go to [LMS-URL]/admin/third_party_auth/samlproviderconfig/add/ and create a new IDP as following

-
slugshould be set asdefault
-
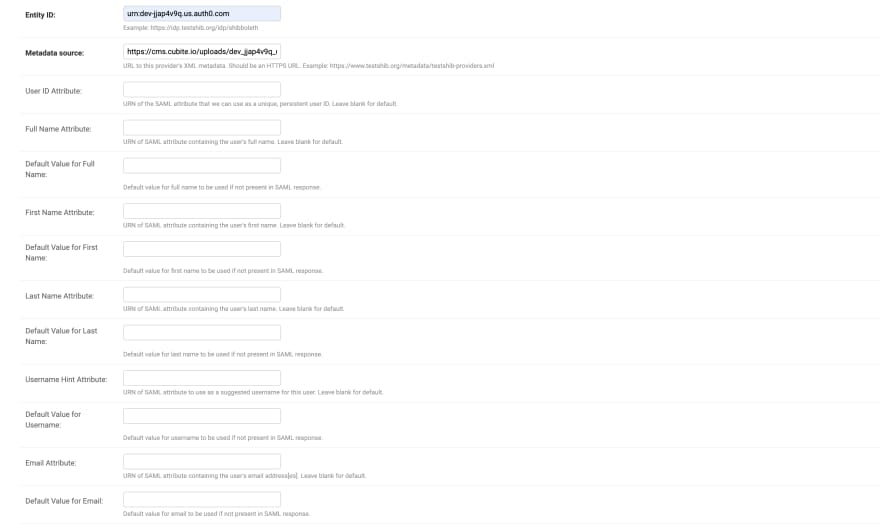
User ID Attribute:as http://schemas.xmlsoap.org/ws/2005/05/identity/claims/nameidentifier -
Full Name Attribute:as http://schemas.xmlsoap.org/ws/2005/05/identity/claims/name -
Username Hint Attribute:as http://schemas.xmlsoap.org/ws/2005/05/identity/claims/nameidentifier Email Attribute:as http://schemas.xmlsoap.org/ws/2005/05/identity/claims/emailaddress

Metadata source:should be the link to theIdentity Provider Metadatathat you uploaded earlier.Entity ID:should beIssuername that Auth0 addons saml generatedSaml configurationShould point to the configuration you created previously
Check the SAML provider data
Now go to [LMS-URL]/admin/third_party_auth/samlproviderdata/add/ and make sure the provider data for Auth0 got created automatically. If not give it around 5 minutes and if it's still not there make sure public key and private key you set earlier is correct and the link to metadata is accesible.
What is Next
We are preparing an article about how to add extra registration field to the Auth0 and also customizing login/registration flow. Stay tuned!
Meanwhile you can read this article about how we decoupled open edx frontend and how we improved the UI.
The #monolithic system is a relic of the past with all its pain and drawbacks. Luckily, modern frameworks like #Nextjs and @strapijs can bring the joy back to your developers and users. Read this post on how we did just that for #openedx!
strapi.io/blog/decouple-…17:36 PM - 15 Jul 2021
If you need any help contact us at hello@cubite.io













Top comments (0)