What I built
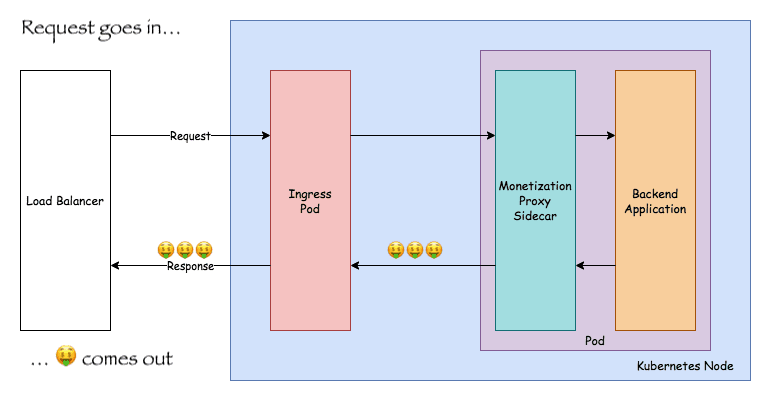
A simple proof-of-concept sidecar proxy1 that injects Web Monetization meta tags into HTML responses from the backend application. Offloading this responsibility to a sidecar is valuable for several reasons:
- It allows applications to benefit from Web Monetization without having to change the code of the application itself. Useful for cases where there are many applications being deployed or when the application is not modifiable (e.g. commercial off the shelf software).
- Platform operators could automatically deploy these sidecars across their entire cluster without application developer intervention.
While the proxy I built for this Hackathon is far from production ready, I hope that this proof-of-concept can inspire further work. One idea might be writing a WASM filter for Envoy proxies that does this work.
Included with the code is an example Kubernetes Deployment that showcases how the proxy can easily be added to an existing Pod as a sidecar container.
1 - What is a sidecar proxy? It is a sidecar container that runs a proxy sitting in front of your "main" application container. Sidecars are frequently used by service meshes to enable features like intelligent load balancing, rate-limiting, certificate / TLS management, and more. Envoy is a commonly used sidecar proxy.
Submission Category:
Foundational Technology
Demo
Demo: https://monetization-proxy.k8s.downey.dev/
I've deployed a sample Ghost blog running with the monetization proxy sidecar to a small development Kubernetes cluster running on Digital Ocean2. The site can be accessed at here. Additionally, you can view the Kubernetes deployment configuration here.
2 - This cluster costs money so I will tear it down in a few weeks.
Link to Code
 tcdowney
/
web-monetization-proxy
tcdowney
/
web-monetization-proxy
Simple Go proxy for injecting Web Monetization meta tags. Done as part of the Dev "Grant For The Web" Hackathon
web-monetization-proxy
Docker repo: https://hub.docker.com/repository/docker/downey/web-monetization-proxy
Simple proxy for injecting Web Monetization meta tags. Intended to be deployed as a sidecar process alongside Web Monetization unaware webapps.
disclaimer
This proof-of-concept project was created for fun as part of the DEV "Grant For The Web" Hackathon. It should not be relied on for production use cases and merely exists to demonstrate what is possible. In the future it might be worth exploring doing something similar using Envoy proxies and a WASM plugin that implements this functionality.
configuration
The proxy relies on the following environment variables:
-
PROXY_PORT-- the port the proxy listens on -
BACKEND_PORT-- the port of the backend application that requests are forwarded to -
PAYMENT_POINTER-- an Interledger Payment Pointer string
Reference the example Deployment to see how you might configure these in Kubernetes.
development
This project uses Go modules which work best with Golang 1.13+. To run the project's…
The proxy is available as a Docker image here.
How I built it
The proxy is built using Go and uses an httputil.NewSingleHostReverseProxy to do a lot of the heavy lifting around proxying. A response modifying function is applied to each response from the backend and does the following:
- Checks to see if the response
Content-Typeis HTML. If it is not, we leave the response alone since we don't want to injectmetatags into Javascript or CSS responses! - If it is HTML, we parse the DOM and inject the Web Monetization
metatag into the document head.
For unit testing I used https://github.com/sclevine/spec which provided some lightweight BDD goodies to Go's built-in testing library. It was my first time using it (I traditionally have used Ginkgo and Gomega) and I found it to be easy to work with.
For building the OCI images I used the Go Cloud Native Buildpack and kbld to streamline the build/push/deploy to Kubernetes flow. More details on that are in the project README.
To deploy the demo I set up a Kubernetes cluster on Digital Ocean. I used NGINX as my Ingress controller and set up automatic provisioning of TLS certificates using Cert-Manager and LetsEncrypt.
Additional Resources/Info
This was a fun little project for me. I got to write some Go, set up a a new K8s cluster, and play around with some new libraries / tools.
One thought I had while working on this though was "I sure wish there was just a Web Monetization HTTP header" instead of having to rely on meta tags. This would have let me just use an off-the-shelf sidecar proxy like Envoy which supports header manipulation and would have opened it up to support non-HTML applications.

![Cover image for Web Monetization Sidecar Proxy [Grant For The Web Hackathon Submission]](https://media2.dev.to/dynamic/image/width=1000,height=420,fit=cover,gravity=auto,format=auto/https%3A%2F%2Fdev-to-uploads.s3.amazonaws.com%2Fi%2Fl3ldnndzqnlih9sfcp06.png)









Top comments (2)
Thank you for teaching me something. Now to research sidecar proxies...
Thanks for leaving this comment! It made me realize that I've been living in the service mesh / Kubernetes world for a while and I've become numb to these terms.
I added a footnote with a short blurb explaining what is a sidecar proxy with some links to help explain it for other folks as well.