Kubernetes RBAC
Role-based access control (RBAC) is a method of regulating access to computer or network resources based on the roles of individual users within your organization.
RBAC authorization uses the rbac.authorization.k8s.io API group to drive authorization decisions, allowing you to dynamically configure policies through the Kubernetes API.
Permissions are purely additive (there are no “deny” rules).
A Role always sets permissions within a particular namespace ; when you create a Role, you have to specify the namespace it belongs in.
ClusterRole, by contrast, is a non-namespaced resource.
ClusterRoles have several uses. You can use a ClusterRole to:
- define permissions on namespaced resources and be granted within individual namespace(s)
- define permissions on namespaced resources and be granted across all namespaces
- define permissions on cluster-scoped resources
If you want to define a role within a namespace, use a Role; if you want to define a role cluster-wide, use a ClusterRole.
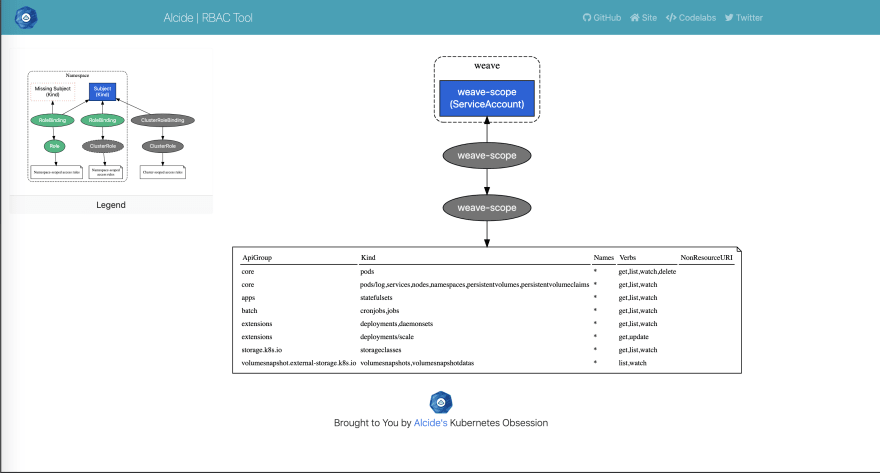
rbac-tool viz
A Kubernetes RBAC visualizer that generate a graph as dot file format or in HTML format.
By default 'rbac-tool viz' will connect to the local cluster (pointed by kubeconfig)
Create a RBAC graph of the actively running workload on all namespaces except kube-system
See run options on how to render specific namespaces, other clusters, etc.
Render Locally
rbac-tool viz --outformat dot && cat rbac.dot | dot -Tpng > rbac.png && open rbac.png
Render Online
https://dreampuf.github.io/GraphvizOnline
Examples:
Scan the cluster pointed by the kubeconfig context 'myctx'
rbac-tool viz --cluster-context myctx
Scan and create a PNG image from the graph
rbac-tool viz --outformat dot --exclude-namespaces=soemns && cat rbac.dot | dot -Tpng > rbac.png && google-chrome rbac.png
Installation instructions can be found here: rbac-tool







Top comments (0)