On July 19, 2021, a consortium of news publications made shocking revelations that eminent persons of India, including the politicians, businessmen, journalists and activists were under illegal surveillance of the Government of India, who used a spyware named Pegasus, developed by a Israeli firm named NSO (standing for Niv, Shalev and Omri, the names of the company's founders).
Between 2016 and June 2021, Pegasus detected 50,000 phone numbers of persons who could be potential targets. At least 65 business leaders, 85 human rights activists, 189 journalists, and over 600 politicians and government officials, including heads of state, prime ministers, cabinet ministers, ambassadors, military, and security officers, are among the names on the list. There were over 300 Indian politicians, activists, business-people, and journalists on the list.
WHAT IS PEGASUS
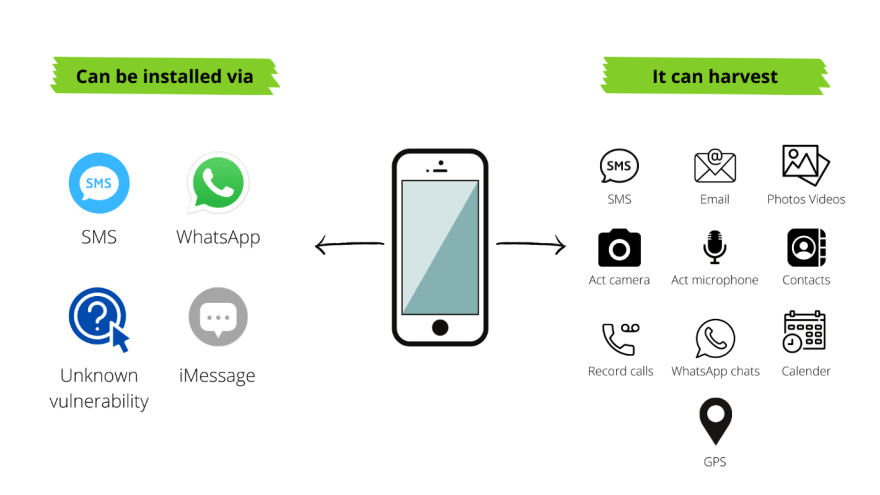
The ultimate spyware Pegasus developed by the Israeli cyber-arms firm NSO Group is making headlines. This malicious spyware can be surreptitiously installed on mobile phones and other devices that are running versions of iOS and Android. It is a Trojan horse computer virus that can be sent to infect cell phones. It is produced by NSO Group, an Israeli software company. More than 50,000 phone numbers were targeted by the Pegasus project. According to the reports, 300 verified phone numbers in India are on the list, numbers including- ministers, opposition leaders, sitting judges and over 40 journalists', activists', and business-people. However, NSO claims it is a tool for tracking criminals and terrorists for targeted spying rather than widespread surveillance.
WHAT IS SPYWARE
Spyware is a type of malicious software (also known as malware) that is installed on a computer without the consent of the user. It creeps into the device, collects sensitive information along with internet usage data, and then distributes it to advertising, data businesses, or any other third parties.
Spyware is considered one of the most common risks to the internet users. It monitors internet activity, tracks login passwords, and snoops on sensitive data once installed. Spyware's main purpose is usually to steal credit card numbers, banking information, and passwords.
HOW DOES IT WORK
Pegasus disguises itself as an anti-theft application so that they can’t be detected by anti-virus software.
It works by taking advantage of Android and iOS flaws that haven't been disclosed yet which indicates that even if a phone has the latest security patch installed there's a possibility that it could be infected.
Pegasus is very able to penetrate a device through a missed WhatsApp call and can even wipe the record of the missed call thus making it hard for the user to know they were being tracked.
Pegasus can also exploit bugs of iMessage to gain backdoor access to millions of iPhones. A wireless transceiver near a target can also be used to install Pegasus.
WHAT CAN IT DO
After installation Pegasus connects to the attacker's command and control (C&C) servers to receive and execute orders, alongside give back the target's confidential information, including- passwords, contact lists, calendar events, text messages, and live phone calls (even messages of end-to-end-encrypted messaging apps). With Pegasus the attacker has access to the most important features of a device namely phone's camera, microphone, and the GPS function, which allows to track down a target.
HOW PEGASUS IS DIFFERENT FROM OTHER SPYWARES
In early 2018, clients of the NSO Group predominantly used SMS and WhatsApp messages to persuade targets to click on a malicious link, resulting in infection of their mobile devices. This is known as Enhanced Social Engineering Message (ESEM).
In Pegasus, phone is routed to a server through a malicious link packaged as ESEM, then the operating system is checked and applicable remote exploit is delivered.
One unique feature of Pegasus is Zero-click installation. Pegasus has many tactics for achieving zero-click installations. Over-the-air (OTA) technique is one of them which can be used to send a covert push message to the target device, causing it to load the spyware with target being unaware of the installation, which she has no control over anyhow.
BRIEF HISTORY OF PEGASUS
2016: Pegasus was first discovered on the smartphone of human rights campaigner Ahmed Mansoor by researchers from the Canadian cybersecurity organization “The Citizen Lab”.
2018: According to a report issued by the Citizen Lab, Pegasus was used in 45 countries. India was featured in the list, as was the case with the most recent revelations.
2019: Journalists and human rights activists in India were targeted for monitoring by Pegasus operators, according to WhatsApp.
2021: According to the Pegasus Project, an international investigative journalism endeavor, various nations utilized the software to spy on government officials, opposition politicians, journalists, activists, and others. Between 2017 and 2019, the Indian government allegedly used it to eavesdrop on about 300 people, according to the report.
HOW TO CHECK IF YOUR DEVICE IS INFECTED WITH PEGASUS
Popular antivirus software cannot detect Pegasus since this spyware exploits zero-day vulnerabilities and these are unknown to the developers of operating systems and antivirus applications.
Amnesty International, a human rights organization, has developed a utility that allows you to identify Pegasus. It is called MVT, Mobile Verification Toolkit. The original source code for MVT can be found on GitHub. However, quick installation for MVT is still not available.
The application needs to be compiled for a specific device. It can be done only on computers that has Linux or MacOS. The utility saves a backup copy of the data from mobile device to computer and then scans through it. If the data can be compromised with any third party, it informs the user about it
HOW TO PROTECT OURSELVES FROM PEGASUS
There are some steps which can be followed to protect our information from Pegasus. They are-
i. When using our device, we should only open links from known and trustworthy contacts and sources.
ii. We should ensure that all required patches and upgrades are installed on our device.
iii. Send disappearing messages while transferring sensitive or personal information.
iv. We should avoid using public Wi-Fi. We should use VPNs at public places.
v. We should use firewalls. Firewall ability of packet filtering ability can exclude the traffic from an untrusted source. the firewall will stop any untrusted source from reaching the device.
vi. We should always encrypt our device's data and we should also use remote wipe features.
vii. Always stay updated with the latest version of Android if we are using android devices.
CONCLUSION
The Cyber-world is an expanding world. Along with the users, cybercrimes are also increasing at a rapid speed. We have to remain cautious and have to take precautionary steps to protect ourselves. It is our duty to remain safe. We should use all the security softwares and should maintain all the rules and regulations to remain safe in cyberspace. Stay safe and secure.







Top comments (1)
Great read @iuc4801 👏