Have you ever realized the danger of a publicly accessible .git folder?
There are some developers who deploy their app to production using pure git clone method. They clone their app repository from gitlab/github/bitbucket directly to a web-root facing folder on server like /var/www/app/. That makes the .git folder exist in /var/www/app/.git.
If you don’t have proper permission to that .git folder, it will be accessible to the public. Like this:
And then hacker can download your .git folder using:
$ wget -c -r -np -R "index.html*" http://example.com/.git
After downloaded, it’s just an empty folder with .git folder on it. It also has all commit history.
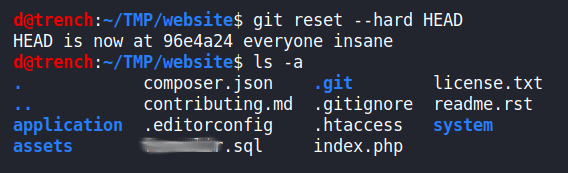
Hacker can reset to latest commit to restore the source code files.
$ git reset --hard HEAD
And boom, your source code is leaked!
Here is how to mitigate it:
Add/edit your .htaccess file to make the .git folder hidden
RewriteEngine on
RewriteRule .*\.git/.* - [404]
Why use 404 not found instead of 403 forbidden?
Hacker doesn’t even know if the .git folder exists, it’s 404. But if it’s 403 forbidden, hacker knows there is .git folder, only not accessible.
Hope it helps.
Salam.









Top comments (7)
The way you’re deploying, your source code is gonna be leaked anyway, as there is no build step.
Pushing
.gitfolder from the beginning is totally wrong, there should be a build process when you deploy your appWell, it depends, if you're using an app written in Python you need to deploy the source code.
In the case of Python you should containerize and deploy your app.
You are cloning repo on your app server? If so, DevOps is needed instead of this
So instead of creating a better build/release process, just stitch a thin patch over a gaping hole?
I don't think this is an ideal setup... I mean I totally understand the danger here, but you really should not be deploying this way at all.