Introduction: APIs Are Everywhere—And So Are the Threats
Have you ever ordered food from an app, checked your bank balance online, or used a weather widget? If so, you’ve already used an API, whether you knew it or not.
You may not see them, but APIs (short for Application Programming Interfaces) are working hard behind the scenes, helping apps talk to each other and making everything feel smooth and seamless.
Think of APIs like digital messengers. They carry data between apps, like your food order from the app to the restaurant’s system. Pretty cool, right?
But here’s the catch: If APIs are the highways for your data, then hackers are the ones looking for backdoors and shortcuts to sneak in. And trust me, they’re getting creative.
When I started diving into backend systems, cloud tools, and how frontend apps talk to servers, I had a “aha!” moment: API security isn’t just nice to have—it’s absolutely critical.
Whether you're just starting out in tech or you’re building complex systems, knowing how to secure your APIs is something you can’t afford to ignore.
So, let’s break it down. What exactly is API security? Why should you care? What are the common threats out there? And most importantly—how can you keep your apps safe?
What Is API Security?
API security is the measures, practices, tools and technologies used to protect APIs against unauthorized access, misuse, injection attacks, and other cyberthreats and vulnerabilities.
If they’re not protected, attackers can:
- Steal personal data
- Modify records
- Crash services (DDoS attacks)
- Hijack user sessions
In short, an insecure API can be the last straw of an otherwise secure system.
Example:
In 2018, Facebook experienced a breach affecting over 50 million users. The culprit? A vulnerability in their Graph API that allowed attackers to steal access tokens (like passwords) and take over accounts.
Imagine being logged into your Facebook account—and someone else doing the same from another country, without your knowledge. That’s the kind of damage an insecure API can cause.
Common API Security Threats
Let’s break down some of the most common threats
- Broken Authentication
If an API doesn’t properly verify who is making a request, anyone can pretend to be a valid user.
Example: An attacker guesses or reuses a token or session ID to gain access to another user’s account.
- Rate Limiting Issues
If an API doesn’t enforce any type of rate limiting on how many requests you can make, an attacker can effectively start to make their own denial of service attack and overload it with requests, bringing it down.
Example: Someone scripts a bot to hit your API 10,000 times in a minute, crashing your server (DDoS attack).
- Injection Attacks (SQL, NoSQL, etc.)
If you don’t sanitize your input, hackers can inject their own code.
Example: If you created an API endpoint like “/api/users/{id}” and your backend directly uses the “id” parameter in an SQL query like: “SELECT * FROM users WHERE id = ${id}”. and I send. “DROP TABLE users;” as the “id”, , the final query becomes: “SELECT * FROM users WHERE id = 1; DROP TABLE users; --
This would delete your entire “users” table — a classic SQL injection attack. And yes, this has actually happened in the real world.
- Data Exposure
If an API ever returns too much data, or sensitive data that’s not needed in the first place, it’s a goldmine for attackers.
Example: You send a user's email to the frontend but also accidentally include their SSN or password hash.
- Insecure Endpoints
APIs going through HTTP, can be easily intercepted (man-in-the-middle attacks).
How to Secure Your APIs (Best Practices)
Securing your API means protecting your data and ensuring only the right people can use it.
Here are some easy-to-understand tips:
1. Always Use HTTPS
When people use your app, they send data (like passwords, credit card info, etc.). Without HTTPS, this data can be stolen by hackers during transfer.
- Use an SSL certificate on your server.
- Force all traffic to use
https://instead ofhttp://.
It’s like putting your messages in a locked envelope instead of a postcard.
2. Add Authentication & Authorization
You don’t want everyone to access everything.
- Authentication checks who you are, not what you can access.
- Authorization checks if you are allowed to do it.
Use JWT (JSON Web Token) or OAuth 2.0.
Imagine JWT as digital pass. You log in and server gives you a pass (token). In every request you use it to proove that you're allowed.
3. Limit the Number of Requests (Rate Limiting)
Prevents people (or bots) from making too many requests and taking down your server.
- Set limits like “max 100 requests per minute”.
- After that, either block or slow down the requests.
Basically stopping someone from refreshing a webpage 1000 times in a second.
4. Validate Inputs & Sanitize Outputs
Hackers could try to put harmful code in your api (like an SQL or script attack).
- Check every input: Is it a number, text, email, etc.?
- Eliminate or reject the unexpected.
If you expect a name, don’t allow things like alert(‘hack’).
5. Use API Keys or Tokens
When apps or users talk to your API, you should know who’s calling it.
- Give every user/app a unique API key or token.
- Make your API check that key on every request.
Think of it like a membership card that gets checked before entering a club.
6. Share Only What’s Needed
The less you reveal, the safer your app is. No one needs to see internal data like passwords.
- Don’t send back extra data in your API response.
- Always filter sensitive fields before sending the response.
It’s like giving a receipt with only the necessary items listed — not the full inventory.
7. Log Activities & Monitor for Problems
You need to know when something unusual or dangerous is happening.
- Log every request (what was called, by whom, when, and what happened).
- Use tools like Sentry, Datadog, Splunk, or even Postman Console.
Like having security cameras to review what went wrong if something breaks.
API Security Quick Checklist
- Use HTTPS - Secure data transfer
- Authenticate Users - Know who's accessing
- Limit Requests - Prevent abuse
- Validate Inputs - Stop attacks
- Use Tokens/API Keys - Identify callers
- Share Less Data - Minimize risk
- Monitor Logs - Detect issues early
Tools You Can Use
- Helmet (Node.js) - Secures HTTP headers
- JWT.io - Token-based authentication
- Postman - Testing with API keys, headers, rate limits
- OWASP ZAP - Scans APIs for vulnerabilities
- Firebase Rules - Secures Firestore and Firebase APIs
- API Gateway (AWS/GCP) - Rate limiting, auth, key validation
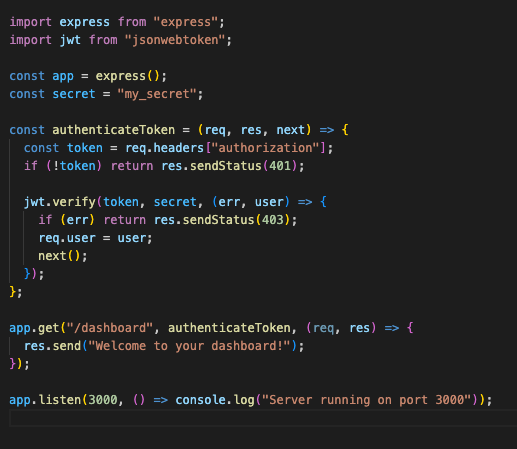
Simple Code Example: Securing an Express API with JWT
Conclusion
At the core of any good app is a secure API and it’s not about writing code, it’s about protecting real people, real data, and real experiences. When you’re using HTTPS, validating inputs, securing endpoints and monitoring usage; You don’t build only secure APIs but trust also. In the world where humans are increasingly plugged in digital world trust means everything. So don’t treat security as an afterthought but consider it as a foundation of your APIs. As Secure API = Secure App = Reliable App = Respected App.
Happy coding—and even happier securing! 🙂



Top comments (2)
This is fantastic! Really well explained! 🤩
Weldone, this is cool post with clarity.
Additionally: apart from applying all possible security, ensure the number one security the app developer can apply is encrypt every data for all requests. So that even if an attacker by which ever means gains access to some how manipulate the secure headers, your data will need another decryption keys to be able to decrypt it.
We know that as far as we "THE TECH WORLD" are CONCERNED, the creators of SSL definitely know how to view the headers, so additionally adding your own request data encryption is key. I call that second lavel request encryption.
Regards.