DEPLOYMENT OF FORTIGATE SSL VPN IN AWS CLOUD
There has been a significant increase in the deployment of enterprise applications and services in the cloud. This has necessitated the need for an additional layer of security and flexibility for services hosted in the cloud. Below are the advantages this deployment will offer:
a. It provides additional security to services and applications hosted on the AWS cloud.
b. It allows easy accessibility of services and applications hosted on the AWS platform.
c. Users do not need to have AWS accounts before they can access and modify applications hosted on AWS.
d. It provides privacy for services and applications.
WHAT IS SSLVPN?
Secure Socket Layer Virtual Private Network (SSLVPN), is an example of VPN (Virtual Private Network) technology that utilizes SSL/TLS protocols to provide secure remote access to a private network. SSLVPN enables users to securely access applications and resources on a private network from a remote location through an encrypted connection over the internet.
STEPS FOR FORTIGATE CLOUD DEPLOYMENT IN AWS
NETWORK DIAGRAM
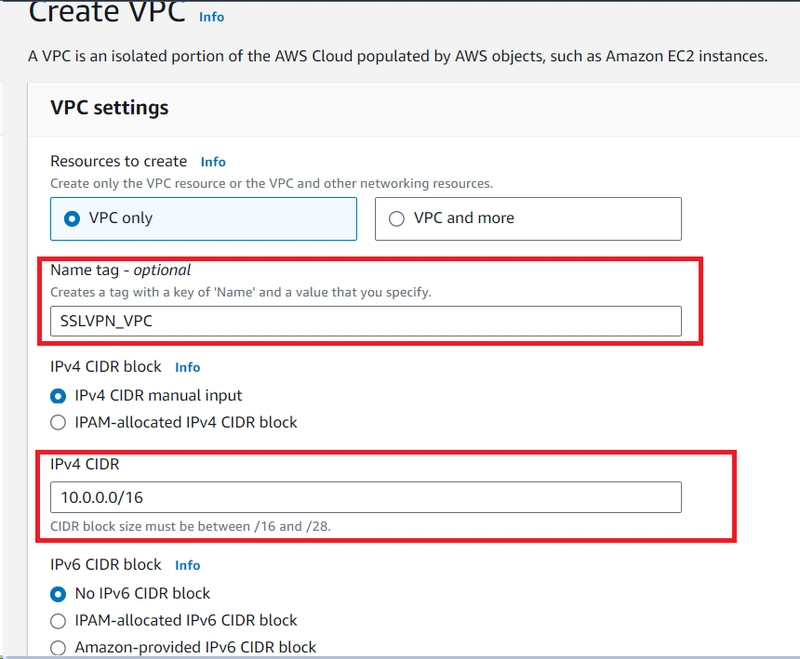
1.CREATE A VPC: The first thing that is required is to create a VPC inside the AWS cloud.
For this VPC 10.10.0.0/16 subnet will be used with name tag SSLVPN-VPC
2.CREATE SUBNET
Create a list of three subnets, with the first one being the public subnet and the remaining two being private subnets.
The subnets shall be named as follows:
10.10.1.0/24 = Subnet_A
10.10.2.0/24 = Subnet_B
10.10.3.0/24 = subnet_C
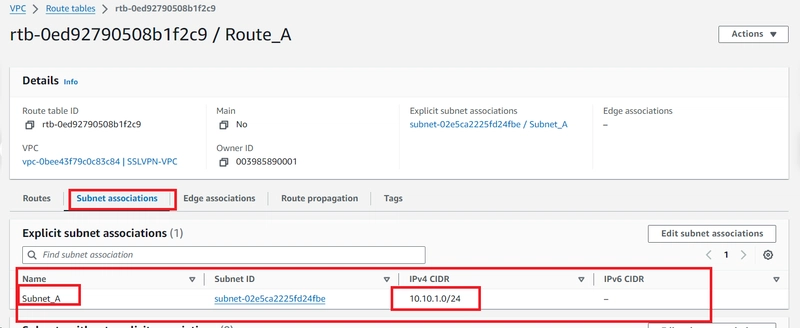
3.CONFIGURE ROUTING
Create a separate routing table for each of the three subnets. They will be named:
10.10.1.0/24 = Route_A
10.10.2.0/24 = Route_B
10.10.3.0/24 = Route_C
4. CREATE SECURITY GROUPS
Create a security group and allow the following protocols inbound, including ports 22, 80, 443, and 10443. The security group is named SSL-VPN-SG
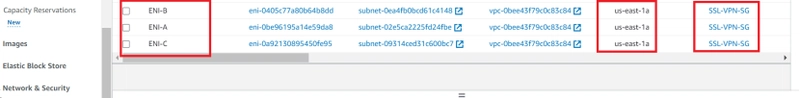
5. CREATE ENI FOR PRIVATE NETWORKS
Elastic Network Interfaces (ENIs) should be created for each subnet. They will be named as shown below:
ENI-A,ENI-B and ENI-C
6. LAUNCH FORTIGATE FIREWALL AND ATTACH ELASTIC NETWORK INTERFACE (ENI).
Launch the Fortigate firewall instance from the AWS Marketplace. In this scenario, I am using Instance type of t3.medium
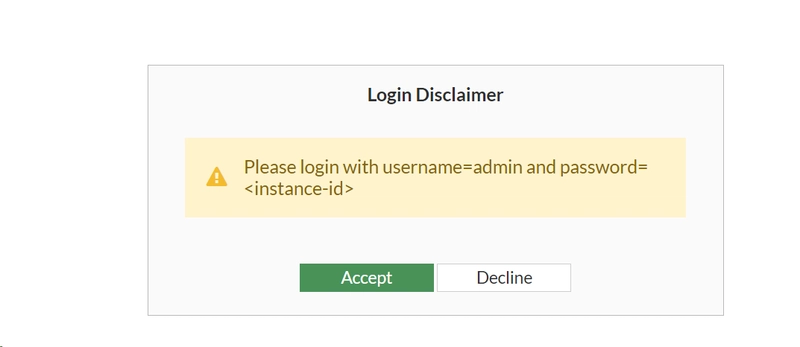
7. CHANGE THE DEFAULT LOGIN DETAILS
When you launch Fortigate Firewall, it gives you the default username as admin and the password as instance ID. It is mandatory to change the password
8. ATTACH TWO ADDITIONAL LOCAL INTERFACES TO THE FORTIGATE
BEFORE THE INTERFACES ARE ADDED
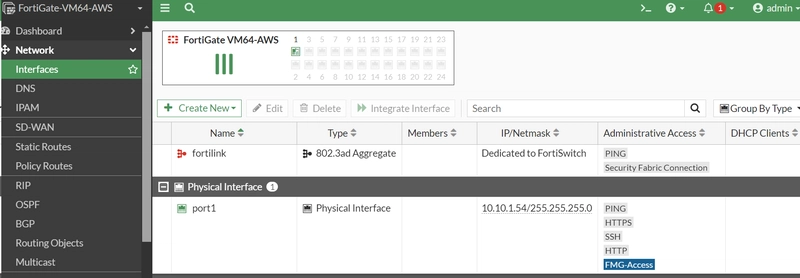
HOW TO ADD THE INTERFACE

AFTER THE INTERFACES ARE ADDED

9. CONFIGURE GATEWAY ADDRESS ON THE FIREWALL WITH THE IP ADDRESS OF THE NETWORK INTERFACES
10. CONFIGURE USER DEFINITIONS AND USER GROUPS.
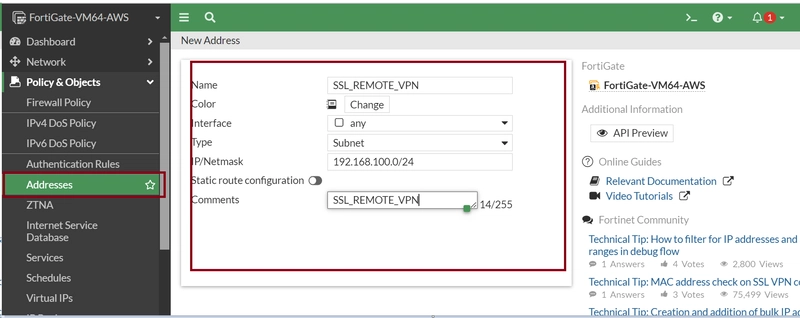
11. CONFIGURE IP SUBNET FOR SSL REMOTE VPN
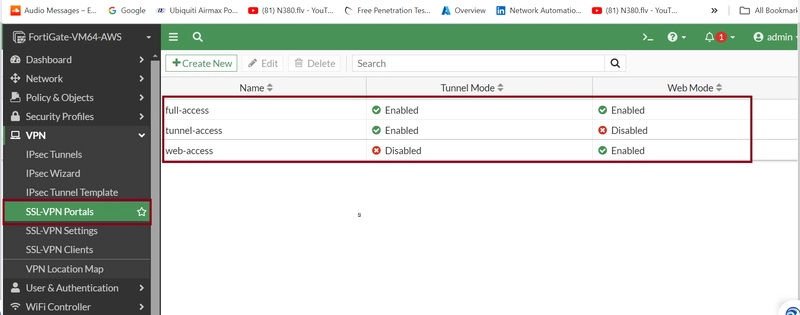
12. CONFIGURE VPN PORTAL
13. CONFIGURE SSL VPN SETTINGS

b. CONFIGURE OTHER USER GROUPS TO USE SSLVPN WEB MODE

C. CONFIGURE SSL_GROUPS TO USE SSLVPN TUNNEL MODE
14. ADD DEFAULT ROUTE FOR ALL THE SUBNETS.
a.POINT DEFAULT ROUTE FOR SUBNET_A TO INTERNET GATEWAY (IGW)
b.POINT DEFAULT ROUTE FOR SUBNET_B AND SUBNET_C TO FORTIGATE ENI.

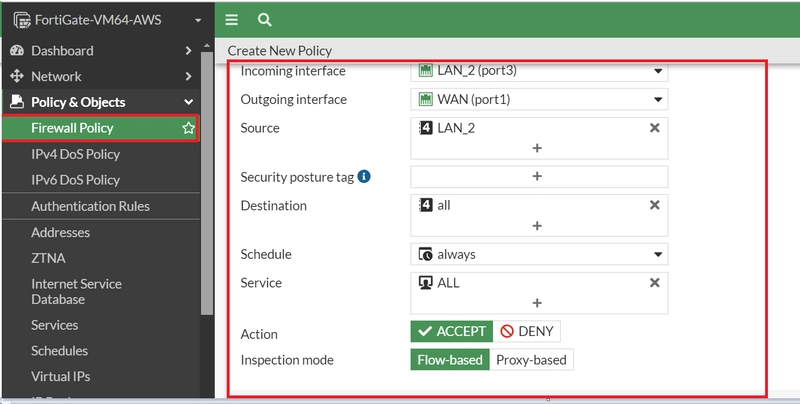
15. CREATE FIREWALL POLICY
a. Create a firewall policy that allows local LAN_1 access to internet .
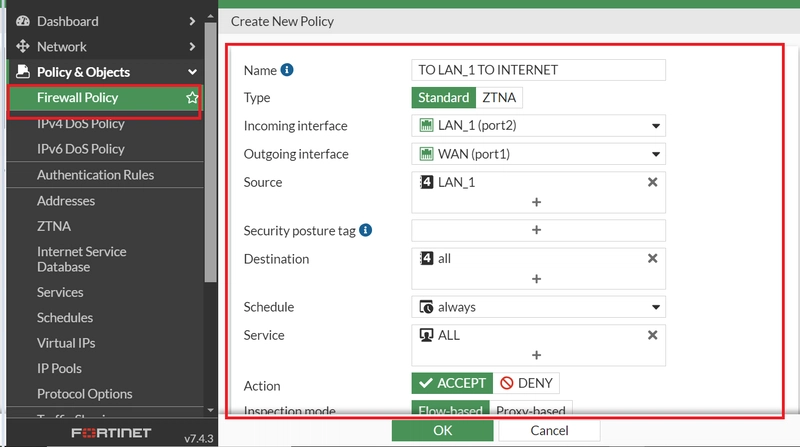
b. Create a firewall policy that allows local LAN_2 access to internet
c. create a firewall policy that allows internet (inbound traffic) access to LAN_1
d. create a firewall policy that allows internet (inbound traffic) access to LAN_2
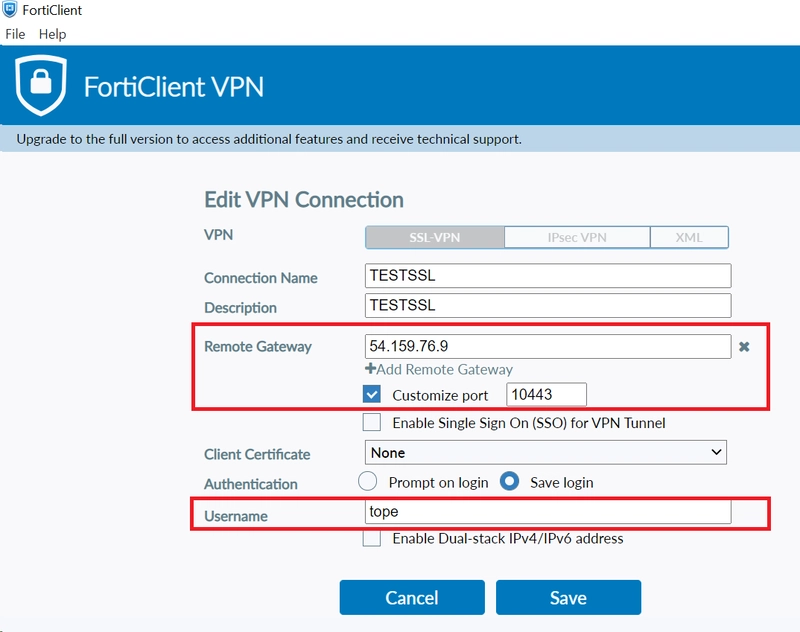
16. CONNECT TO AWS SERVICES ON A PRIVATE CLOUD USING SSLVPN WITH FORTICLIENT.
17. LAUNCH AMAZON INSTANCE INSIDE LAN_2 SUBNET
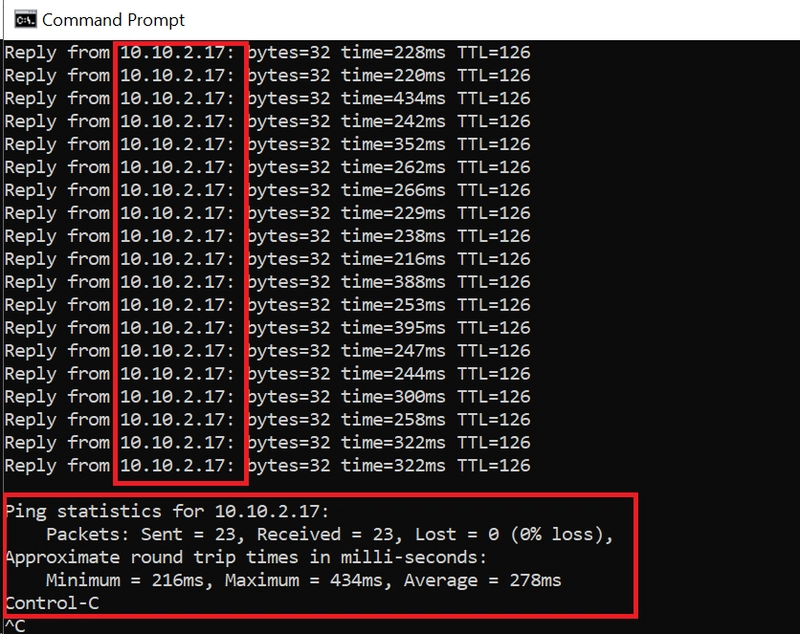
18. TEST CONNECTIVITY FROM USER PC ON INTERNET TO AMAZON INSTANCE LAUNCH INSIDE LAN_2 SUBNET
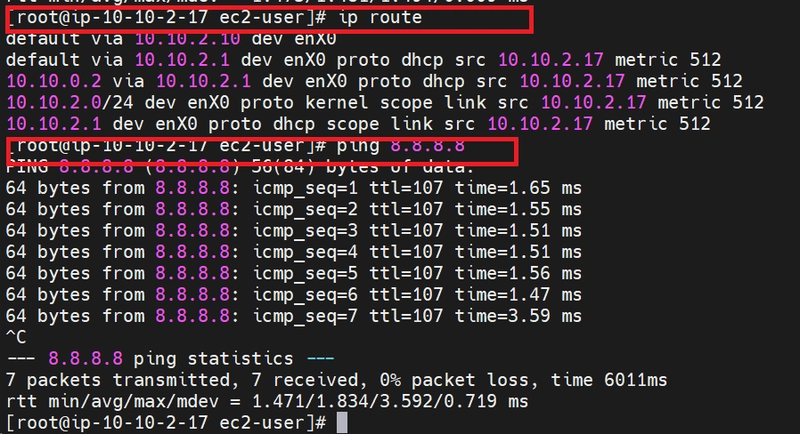
19. CONNECT TO AMAZON INSTANCE LAUNCH INSIDE LAN_2 SUBNET AND TEST INTERNET ACCESS
CONCLUSION
This guide outlines a straightforward process for deploying an SSL VPN using FortiGate in the cloud. I trust it will be beneficial as you embark on your deployment journey. Please be aware that utilizing the FortiGate AWS Marketplace will incur charges for both instance usage and software. However, opting for a lower instance type on AWS can help minimize instance costs. Additionally, you can use a trial unit of this product for 30 days without incurring software charges, though AWS infrastructure charges will still be applicable.



















Top comments (0)