Ensuring safe digital communication may seem so simple at its core, yet can be the bane of a product's survival in the ever evolving market. This may seem like an overstatement, but when the risks are fully considered, it becomes apparent why so much money and effort is invested to evolve security practices and mitigate new risks as they are discovered. At the core of ensuring safe communication, lies one of the fundamental building block, Cryptography.
Cryptography can simply be defined as the practice of applying techniques to conduct secure data communication in the presence of adversaries. The key principle of cryptography is to ensure confidentiality, integrity and authenticity during communication.
TLDR: Cryptography is one of the core building blocks for secure communication in software development.
Core principles
- Confidentiality: act of concealing data from unauthorised access.
- Authenticity: ability to trace data identity back to its origin of creation.
- Integrity: concept of determining if data has been altered since its creation.
Methodologies
There are several techniques upon which security of data is ensured, below is a brief summary of some of this concepts:
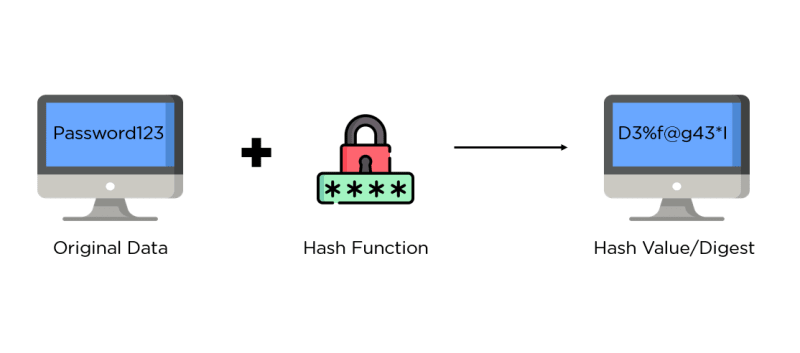
Hashing
- This is a pattern of encoding data in cipher text such that the process is deterministic, irreversible, and collision resistant.
- In simpler terms, this means that no data, plain text for example is redeemable from its encoded cipher text, making it an irreversible process.
- Different cipher texts are formed for any slight change in the value of the plain text, hence deterministic.
- Collision resistant refers to its ability to create a unique cipher value for every plain text hashed, ensuring that no two plain text have the same cipher text.
- The cipher text, also known as hash is created by unique algorithms that are designed to operate by relying on specific mathematical theories. Examples of such theories are the discrete logarithmic problem and modular arithmetic.
- One application of hashing can be illustrated in Public Key Cryptography, a pair of related key values that include a public and a private key. The public key is generated from the private through hashing.
- By leveraging on cryptographic hashing, other important techniques have been designed, such as checksums and digital signatures.
Checksums
- These are small values generated from the cryptographic hashing of specific data, typically much larger than the checksum itself.
- The process of generating a checksum is a simple process, aimed at ascertaining the integrity of data during transmission or storage.
- This is important because, some of the data may be accidentally misplaced or otherwise corrupted.
- Its simplicity makes computing its integrity easy and efficient to ascertain.
- It is typically used by data storage and transmission systems to enforce efficiency of the process.
- Although they aren't a full proof solution to data security, they are useful for preserving data integrity.
Public Key Cryptography
- This is an application of cryptographic hashing that consists of a Public Key, a Private Key and a Signature.
- The public key is a value that serves as a means of public identity for its corresponding secrete private key.
- Private keys are kept secret specifically for the power that it wields. Unauthorised access to a private key enables the possessor to impersonate the actual owner of the key.
- By convention, private keys are generated from randomly generated data to maximise its security. Digitally, this randomness is simulated by relying on algorithms known as pseudorandom number generators.
- Although private keys can be generated manually, this may compromise its security, hence advised against.
- The private key can be used to form a binding relationship between the Public key pair and a signed piece of data, producing a corresponding signature.
- Using the public key, the signed data, and the resulting signature, the authenticity of the signed data can be verified by any third party without accessing the private key.
- This means that the signed piece of information can be verifiably proven to originate from the public key pair without the owner ever disclosing the private key, therefore establishing trust.
- There are various types of digital signatures, each formed from by unique algorithms. Examples are the Elliptic curve digital signature(ECDSA) and Knorr signature.
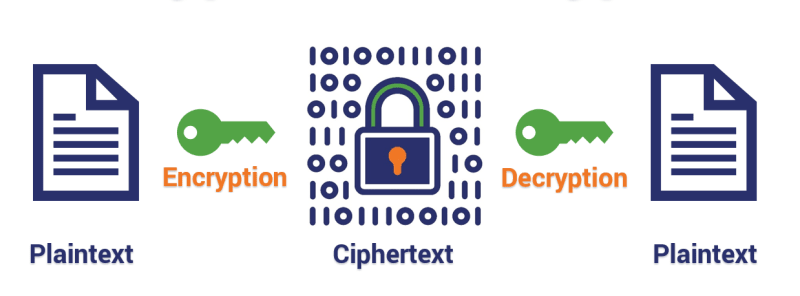
Data Encryption
- This is a cryptographic technique specifically aimed at enforcing confidentiality of data.
- It is the process of encrypting or encoding data as cipher text such that it is confidential, reversible, yet difficult to decode by unauthorised adversaries.
- This process is not aimed at preventing interference during transmission of data, rather it is designed to ensure intelligibility to any unauthorised interceptor.
- This is achieved by using a secret key during the encoding of the data to secure it.
- There are two forms of commonly used encryption techniques, Symmetric and Public-key encryption.
- Symmetric encryption involves the use of the same key to encrypt and decrypt data, hence they’re easier to compute in comparison to Public-key encryption.
- Public-Key encryption, also known as Asymmetric encryption, employs the use of a public key cryptography to encrypt data.
- This is achieved by using a public key to encrypt data, such that only the bearer of its private key can decrypt it.
- Because of this additional layer of separating concern, they offer more security, and as a result require more computing resource than symmetric encryption.
- Ideally, data encryption does not guarantee full proof security from interceptors, but a well encrypted data will require a good amount of both skill and computational resource to decode without the required secret key.
- Authorised decoding of encrypted text with the secret key on the other hand is as easy as cracking a nut, requiring relatively much lesser computational resource.
Practical Applications
Transport Layer Security (TLS)
- This is a Cryptographic protocol that ensures security of transit data over networks.
- It operates by providing end to end security of data sent between applications over the internet.
- It leverages the cryptographic encryption of data during transit.
- This encryption includes both Symmetric and Asymmetric types to maximise security.
- A random session key is generated for the transmission session by the client.
- It further uses the server's public key to encrypt it such that the server can only decrypt this session key using its private key, and transmits it to the server.
- Upon receival and decryption of the session key by the server, both participants would bear the session key in their possession.
- Further communication would then be encrypted and decrypted with the session key.
- It is used in applications such as email, VOIP, instant messaging, DNS and web applications.
Data storage
- The secure storage and transmission of data is one of the most important factors to consider when building software products.
- A “minor” breach of data, either due to unauthorised access or accidental corruption can mar the reputation of any product.
- The detriment of this risk is why software developers apply a combination of techniques to maximise security and ensure integrity.
- An example is in the encryption of data during transit, between a client and its server, rather than leveraging only on network security. This additional measures further reinforces data protection.
- Data hashing prior to storage is another means of storing extremely sensitive information, by reducing risk of exposure upon a breach. This pattern of storing hashes rather than actual data provides an elevated level of security to sensitive data. It is frequently applied in the storing of passwords and credit card information.
- Lastly, Checksums are frequently used to establish the integrity of data at various point during its lifecycle.
JSON Web Token (JWT)
- This is a mechanism designed to communicate authenticity of any entity, such as a user, by ascertaining their identity.
- JWT is a standard for representing claims of ownership in modern applications.
- It provides a secure alternative to storing login credentials such as username and passwords, on servers after initial authorisation, to verify future claims.
- After the user's initial authorisation, a token is generated by the server.
- This token is generated from the claim, such as a user’s credentials and an additional secret, known only to the server.
- The token consists of three integral parts, namely an header, payload and signature.
- The header contains the type of token created and the hashing algorithm used to create the signature.
- The payload contains the claim, such as the identity of the user in this scenario.
- While the signature is the cryptographic hashing of the header, payload and the secret data, known only to the server.
- This token can then passed around back to the requesting client for use.
- Whenever the client requires further access to any protected resource, alongside its request for the resource, it presents the previously received token for authentication.
- Upon receiving this request, the server verifies the authenticity of the token, then grants access if successful.
- JWT introduces better efficiency by removing a round trip, that would have been used by the server to authorise access requests with login credentials.
Decentralised systems
- Thanks to recent boom in popularity of Bitcoin and decentralised systems in general, cryptography has gained massive popularity, prompting many to believe it is a recent innovation.
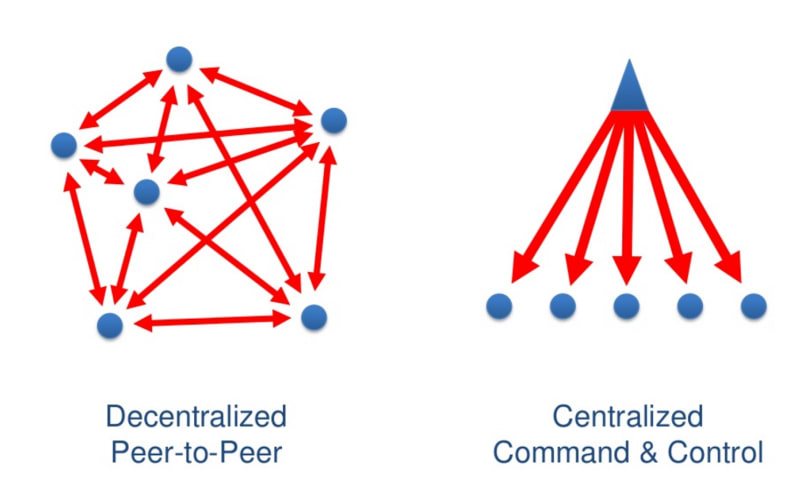
- Decentralised systems are designed such that they rely heavily on the super powers of cryptography to function.
- This results from the decentralised approach to authority in the system.
- What this means simply is that unlike centralised systems which rely on a central authority for trust, to verify claims, or direct the affairs of the system, participants of most decentralised systems operate at the same level of control, with no participant ranking higher in authority than another.
- This design to decentralise trust by distributing control, also prevents censorship of participation, promotes transparency, maximises both scalability and resillience of the system.
- To enforce trust in a trustless system, cryptography is leveraged, from public key pair identities, to transactions integrity, authentication of claims, to network wide state consensus, creation of currency and much more.
- The application of cryptography is evidently the glue that holds the several moving components of decentralised systems, operating efficiently as one.
Conclusion
I hope that with these few ramblings of mine, I have been able to successfully convince you and not confuse you of the importance of security in digital communication, the role of Cryptography and the need to ensure strict adherence to best security practices during software development.
Sources
Encryption
Cryptography Digital signatures
TLS Basics
JW Token
What Is JWT and Why Should You Use JWT
How Is Cryptography Used In Applications?








Top comments (0)