Data not Hashed/Encrypted Properly
Adopt algorithms/functions that are widely regarded as secure when it comes to password hashing or data encryption. MD5 can be handy in many occasions, but it's not really a strong candidate to be used solely for encryption.
For hashing, try argon2 or bcrypt, as suggested by OWASP. Those from the SHA family are alright too, be aware of the fact that they can be accelerated by a GPU though, making it more susceptible to brute-force attacks.
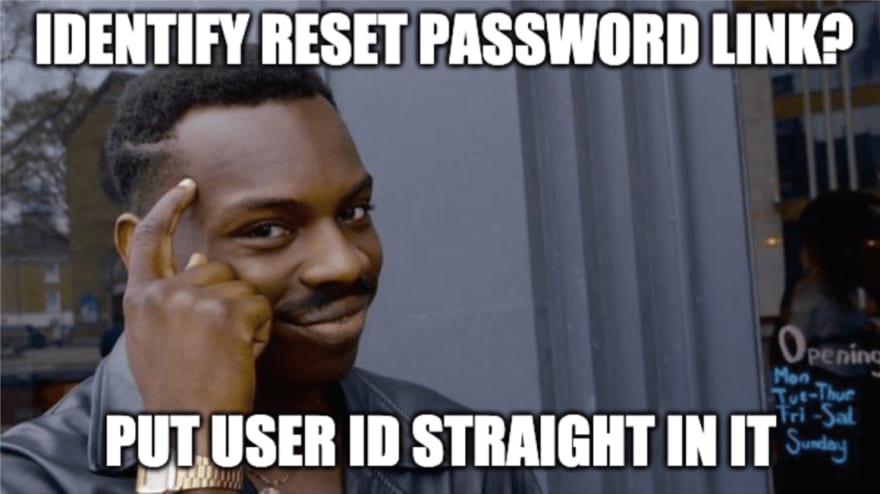
Hmm How to Identify a User when S/he Resets Password?
Please don't do this...
Avoid using any personally identifiable information (PII). Never take chances when it comes to PII. Even if encryption is applied, it can still be broken/decrypted by attackers, where they can then use the PII to match a user from your system.
We’ve seen “encrypted” user IDs being used as the password reset token passed in a URL, which is not a very good idea, as aforementioned. In our case, the token encryption wasn’t done properly where a cryptographically broken algorithm (MD5) was adopted, which resulted in the quoted word to be encrypted in the last sentence.
Always use randomly generated ID as the identifier. Give each generated ‘reset password’ session a life span and prevent brute-force matching attempts on the ID by implementing rate-limit mechanisms on the URL token.
No Expiry on Access Token
Let’s assume that you are generating access tokens properly with safe encryption. If there’s no expiry mechanism, the tokens that were already generated will haunt you forever. This is literally giving hackers unlimited time to pull off a token sidejacking. Just imagine an attacker getting their hands on an access token! They can authenticate themselves and go into your system and do whatever they want. This is quite likely to happen. Just open your cookies manager on your favorite browser and check how many access tokens are stored there.
Even if your machine is kept safe and all transits are conducted with HTTPs, access token with no limited life span can still pose serious threats. Even if your connection is protected by HTTPs, with enough computing power (which isn’t hard to come by nowadays) and time, an attacker can intercept your exchanged data and crack your sessions/tokens out of it.
For more details and in-depth solutions
Read the original post, served with more memes!








Top comments (0)