If you have seen your CI pipeline builds failed due to security vulnerabilities in some NPM packages, you have probably tried npm audit fix and boom! No sign of those found N high severity vulnerabilities in scanned packages messages!
In some cases, that command won’t solve your issue; sometimes the issue is caused by a transitive dependency (sub-dependency) and you can’t or don’t want to wait for a version patch for the package.
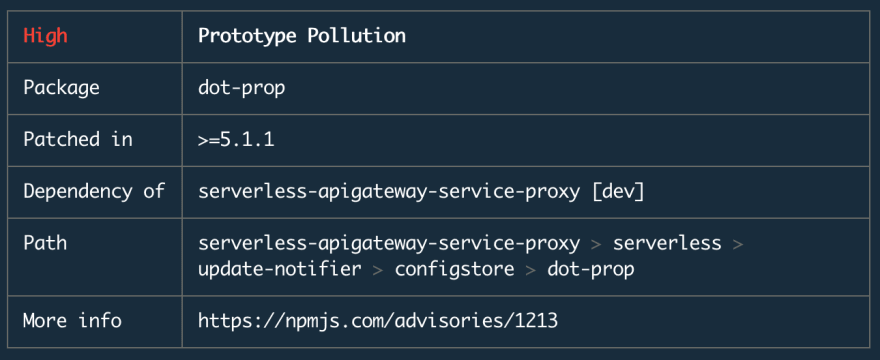
For instance, consider the following security vulnerability (https://www.npmjs.com/advisories/1213):
It says, the dot-prop package has a security issue which needs to get fixed, and serverless-apigateway-service-proxy and serverless depend on it. But if you run npm audit fix you’ll probably see a similar message:
fixed 0 of N vulnerabilities in X scanned packages
N vulnerabilities required manual review and could not be updated
You have some options here! One option is to ignore that specific vulnerability in your CI pipeline using another NPM package like audit-ci which is basically something like this:
npx audit-ci --allowlist 1213
That is a good way of skip security issues temporarily, however, this approach is not always recommended as your project may still be vulnerable even if it is a dev package.
The second option is to force a specific unaffected version of that package. This means we need to change our packahe.json and add the following:
{
"name": "project-x",
... "scripts": {
"preinstall": "npx npm-force-resolutions"
},
... "resolutions": {
"dot-prop": "5.1.1"
}
}
This will override the affected versions with the specified version. Again, this is not always recommended and should be used carefully and only if you have no other option! Normally, we need to wait for a version patch from the package maintainers to fix a vulnerability.
That’s it! Happy coding!






Top comments (1)
I'm always cautious with using
--forcewith any command!npm auditis no exception for me so I prefer to see what's going wrong and fix it step by step.