Nowadays, Kubernetes is one of the most popular and loved platforms used by the community, to run and orchestrate container workloads.
It is present in several open-source and private projects as the base of its infrastructure. They trust to use Kubernetes as a platform.
The problem
The world of Kubernetes can be sometimes very complex and if we make use of it, we need to ensure we are doing it right.
There are lots of tools that can ease that work for us to simplify the process to get Kubernetes working correctly as our platform.
As you may know, the Kubernetes workloads are most commonly defined as YAML formatted documents. Sometimes, it is rather hard to express constraints or relationships between manifests files.
What can be done to help ease the process of using Kubernetes correctly?
There are existing tools to integrate static checking allowing catching errors and policy violations closer to the development lifecycle.
These tools gives us the guarantee around the validity and safety of the resource definitions is improved, therefore you can trust that production workloads are following best practices (which is a must nowadays).
As developers, we need to guarantee the validity and safety of our Kubernetes manifests to ensure the security and integrity of our production environments.
Here comes when the tool kube-score can help us.
Kube-score is an open-source tool that performs Kubernetes object analysis with recommendations for improved reliability and security.
How can we introduce kube-score in our CI/CD processes?
GitHub Actions to the rescue!
My Workflow
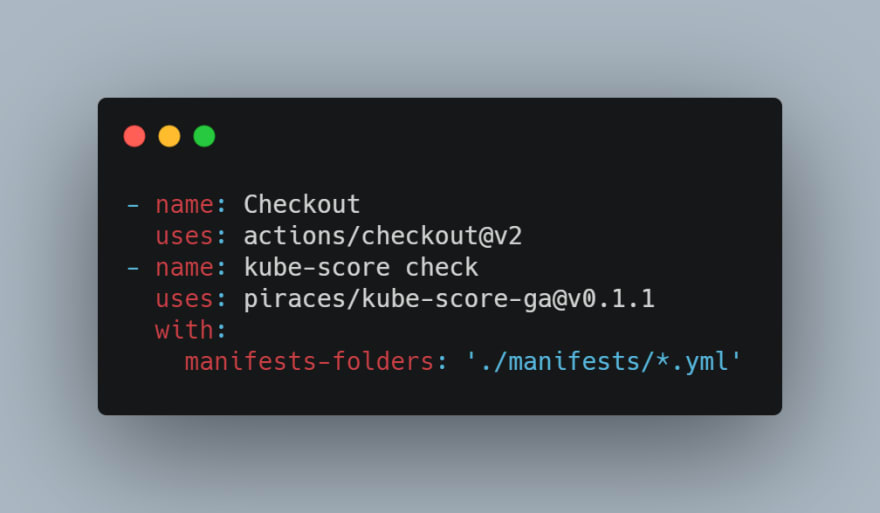
My developed GitHub action (kube-score check), allows GitHub users to execute kube-score in their workflows along other actions and guarantee the validity and safety of their Kubernetes manifests.
It is very simple to use, you only have to perform a checkout of the project repository and execute the action, which takes as input an array of manifests (or directories with manifests) which you want to validate and test (wildcards supported):
Read the full Readme of the project to see all options.
Submission Category:
Maintainer Must-Haves / DIY Deployments
Yaml File or Link to Code
Please take a look at the action repository, and give any feedback if you want!
Contributions are welcomed too!
 piraces
/
kube-score-ga
piraces
/
kube-score-ga
Github action to execute kube-score with selected manifests (YAML, Helm or Kustomize)
kube-score Github Action
This action executes kube-score with selected manifests (with support for YAML, Helm or Kustomize manifests).
Features
Inputs
kube-score-version
(Optional): The version of kube-score to use. Defaults to the latest available.
manifests-folders
Required: An array of relative paths containing manifests to analyze with kube-score (separated with commas). It is mandatory to establish a wildcard for the files or the concrete filename.
Example: ./manifests/*.yml,./other/manifests/*.yml
ignore-exit-code
(Optional): Will ignore the exit code provided by kube-score, will always pass the check. This could be useful in case of using the action in an information way.
See the YAML file for the action: action.yml
Additional Resources / Info
In the links below, you can see the GitHub action running with different forks of popular projects, such as the Application Gateway Ingress Controller (AGIC) of Azure, or the examples provided in the official repo of Kubernetes.
Take a look and see how AGIC Custom Resource Definitions (CRDs), are passing all validations and recommendations (as is a ready to use in production controller).
-
See the GitHub Action in use:
GitHub Repository: https://github.com/piraces/kube-score-ga
GitHub Marketplace: https://github.com/marketplace/actions/kube-score-check














Top comments (0)