There are different kind of passwords uses:
- the "my memory isn't that good" (also call the "I don't care anymore" method) with passwords like
qwertyor123456or literallypassword - the one that uses social information, ex:
199105Bob - the good ones
Let's be real, the first two aren't secure at all, not even a little. But what about "the good ones"? Well, they are what we are talking about.
Maybe sometimes you wonder if your password is safe enough, and you hope that your account will not be taken by someone else by any way. First, we need to take a look at what attacks can be done to find your password.
Brute-force attack
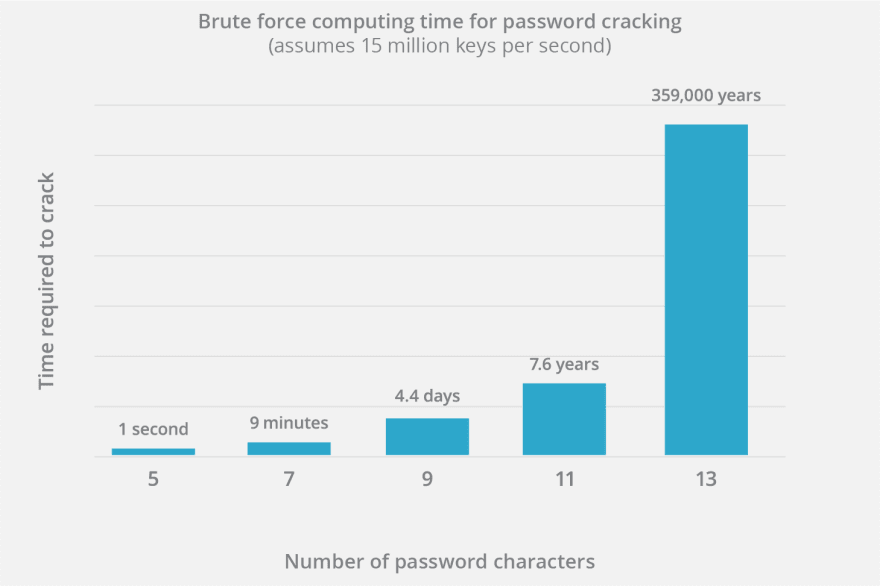
This method is used to try every possibility in a way find your password. It's not used a lot because it requires massive amounts of time and power to be achieved, depending on the target's password length.
The longer a password is, the longer it will take to try every possibility.
Dictionary attack
While brute-force attack tries every possible characters, security researchers found a way to escape the useless trials and focus on commonly used passwords.
A dictionary attack use pre-defined passwords list instead of random characters. Rules can even be added to match the target's information and remove passwords that may not work, like its birthdate, its name, etc... That's social engineering.
To prevent this method, don't use obvious personnal information in your password and check if it's not already in a database.
Your web browser's saved passwords
Maybe that you use the "Remember my password" option while using the internet. While this option can be very comfortable to use, it's not secure at all.
Web browsers cipher your passwords, but they also decipher them to fill password inputs, to make this happen, they use a stored key. So why can't we decipher them too? Well, we can, tools like LaZagne are the proof, that's why you should never use this option.
Solutions
Now that I told you how your password can be hacked, I must tell you how to create strong passwords that are not a plague to use.
Password managers
Those are softwares that helps you to manage your passwords. The best use of them is to export your password with a file (that can be transferred in a secure way using WarShield or something else).
You can find a lot of password managers on the internet, maybe you will find the one who match your needs.
Easy to remember strong passwords
A dream for your accounts, a nightmare for hackers, the sure thing is that you can remember sentences. What about using our brain's capacity in order to create passwords?
This method doesn't need a random sentence, just try to make logic. I will create John Lemmon, a man that live in London at 41 Abbey Street, his password will be MniJL@Il41ab&. I see you, behind your screen, with a face saying "wtf is that?", it can be really hard the first time you use a password like this but it's really easy to remember.
The sentence was My name is John Lemmon and I live at 41 Abbey Street, the ampersand (&) is a random character with no logic behind it.
Like you see, it's pretty easy to create a very strong password without breaking your mind every time you need to remember it.
Conclusion
Today, there is no excuse for not having a secure password.
I think that there should be computer security awareness in schools to teach children to protect their data in the digital world. In the next years, it will evolve, more and more peoples are learning security and the security war will never end.
Stay safe with your data.







Top comments (12)
I tend to use a lot of passwords inspired by xkcd.com/936/
I usually mix in a couple of nonsense words in them for more security (in case there's a password cracking program that's aware of xkcd 936)
I didn't know xkcd, thanks for sharing this! Random words are very nice, longer means stronger ( ͡° ͜ʖ ͡°)
Sorry I am late, but this technique reminds me of another one, very similar : Diceware which looks like a very strong password generator as well !
Hi Simon, thanks for sharing! I like this one much more as it appears to be well studied.
To add on to your suggestion, it is good practice to use different passwords for every website. Because not all sites treat passwords with equal security. If you use the same password everywhere, that random forum you signed up for 3 years ago might be pretty easy to hack, and therefore it will expose the same email/password you use for FB.
So, I have a strategy for varying passwords between websites that doesn't require a memory palace. I use a complex base password like the post above describes. But I add some characters to the password that are specific to the website. For example, for a bank website, you might choose
ba(the first 2 letters inbank) as your extra letters. You take your base password and add the extra letters to the front, middle, end, or some combination of positions. You can choose your extra letters from the kind of thing it is, or the name of the site, or just the first thing you think of for that site. Whatever your strategy, you only have to remember 2 bits of information: your base password and your extra letter formula. Then anytime you go to a site you can mentally calculate what the password should be.The placement of the letters (front, mid, back, etc) gives some variance for when sites force you to change passwords. Then you use the same letters, but put them in a different place. If you come back to the site sometime later and are having trouble logging in, you can try a different letter placements.
I didn't mention that the use of different passwords for each website is recommended, nice to mention it!
Your method is a nice way to handle multiple websites issue, like for dev.to it will be Dv or something like that.
Current guidelines suggest not having a new password for each website, as you can forget it and through frustration remove all safety precautions.
A better solution would be to have 3 interchangeable characters and use the website names shorthand for it. I.e:
If you have a password like fg24f!hyn%
Add 3 letters for what website: fg24f!HYn%fac (Facebook), fg24f!HYn%twt (Twitter), fg24f!HYn%gth (GitHub).
That way you have learned a master password, and then just remember what website you're trying to log in to... Which hopefully isn't difficult!
Thanks. Yeah, that's exactly what I was getting at.
Thanks for this article! I want to challenge/comment on a few of your statements, however. The web browser's password store gets you 60% of the way to "great" security. For most of the internet, getting them to use unique passwords generated, stored, and synced via their browser is a huge win. I would absolutely recommend browser password stores for the majority of people. It's the biggest win (60% of the way there) with the smallest change to user behavior. I agree that someone with access to the local filesystem can read those passwords in plaintext. That gets protected in the last 40%. For the vast majority of people on the internet, that's an OK accepted risk. For the readership of dev.to, I think your statement works because we're all super technical and ready to add a little complexity to make sure we're doing the right thing. (we all unit test, right?!)
Password managers are awesome and I would love if everyone used them. That gets you another 10% of the way to "great" security. I would include Lastpass and 1Password alongside Dashlane, as I believe those two have a larger market share. Going with the biggest password manager generally means you're going to go with the company with the most eyes on them and security issues will get fixed much more quickly. Lastpass's turnaround for notification, remediation, and publication to production is generally a couple hours. It's pretty incredible. I use a different open-source password manager but gotta give them credit where it's due.
In terms of your password creation recommendations, using a sentence you know to generate a passphrase is awesome. Although, last year NIST rolled back their recommendations that you need a bunch of numbers and symbols in your password. They've admitted their guy basically made up those rules and they heavily inconvenience users trying to remember them. That part I don't believe is in the report but said in an interview. The full publication is here, although it's dull so it's easier to read Auth0's summary of the report here. TLDR; if you have to remember a password, use a long passphrase made up of a sentence you will remember (from your favorite book or something). If you don't, let your password manager or browser generate a long one for you.
The last 30% of great security comes from setting up 2FA but that's not strictly password security so it's fine to leave out in a post like this. Including here so you get where the nice 100% comes from, in my mind.
I couldn't hope for a better comment 😮
You made a counter argument in your first paragraph, if only accessing your file system can lead to a theft of data then it's not safe at all. While browsers don't really protect your passwords because of a lack of master keys, password managers does that very well. But remember that some self-hosted password managers are stored locally, that means that it can be taken and deciphered (depending on your master key).
Auto-generated passwords can be really bad when it's generated from a website or a platform that has internet connection. They can store them in their database, so your password could not be really safe. On the other hand, it's safe to generate it locally.
By the way, every passwords can be taken by phishing (2FA inclued).
A quick and dirty solution to complex passwords:
One more time, a wonderful post.