This blog post will detail how to setup Tanzu Build Services in a test environment, and then create a container image from a dockerfile, fixing several vulnerabilities compared to the current container image.
What is Tanzu Build Service?
Tanzu Build Service uses the open-source [Cloud Native Buildpacks](https://buildpacks.io) project to turn application source code into [container images](https://github.com/opencontainers/image-spec/blob/master/spec.md).
Build Service executes reproducible builds that align with modern container standards, and additionally keeps image resources up-to-date. It does so by leveraging Kubernetes infrastructure with [kpack](https://github.com/pivotal/kpack), a Cloud Native Buildpacks Platform, to orchestrate the image lifecycle.
Build Service helps you develop and automate containerized software workflows securely and at scale.
You can read more about the Tanzu Build Services concepts here.
Pre-Reqs
Have an accessible Image Registry to both your local client and your Kubernetes cluster.
- I used Dockerhub for my lab environment.
Install the Carvel tools.
- kapp is a deployment tool that allows users to manage Kubernetes resources in bulk.
- ytt is a templating tool that understands YAML structure.
- kbld is needed to map relocated images to k8s config.
- imgpkg is tool that relocates container images and pulls the release configuration files.
brew tap vmware-tanzu/carvel
brew install ytt kbld kapp imgpkg kwt vendir
Install the kp cli tool.
# Download from the Tanzu Network pages
chmod +x kp-linux-0.4.0
sudo mv kp-linux-0.4.0 /usr/bin/local/kp
# Install using Brew
brew tap vmware-tanzu/kpack-cli
brew install kp
# Download from GitHub Releases Page
curl -LJO https://github.com/vmware-tanzu/kpack-cli/releases/download/v0.4.2/kp-linux-0.4.2
chmod +x kp-linux-0.4.2
sudo mv kp-linux-0.4.2 /usr/bin/local/kp
Installing Tanzu Build Services
Log in to your registry that will host the Build Services containers and be used by your Kubernetes cluster
Login to the Tanzu Registry using your Tanzu Network login details.
docker login registry.tanzu.vmware.com
Login to your local Image Repository.
docker login **{repo\_url}**
Copy the images from the Tanzu Registry to your registry suing the imgpkg tool.
imgpkg copy -b "registry.tanzu.vmware.com/build-service/bundle: **{version}**" --to-repo **{repo\_url}**
# Example
imgpkg copy -b "registry.tanzu.vmware.com/build-service/bundle:1.3.0" --to-repo saintdle/tbs
Pull the image manifests locally.
imgpkg pull -b **{repo\_url}** -o **{location}**
# Example
imgpkg pull -b "saintdle/tbs:1.3.0" -o /tmp/bundle
Now to deploy Tanzu Build Services, we’ll use the yyt tooling to map values across as needed into the various files:
- Local Image Repo URL
- Username and Password
- Tanzu Net username and password
ytt -f bundle/values.yaml \
-f bundle/config/ \
-v kp_default_repository='{repo_url}' \
-v kp_default_repository_username='{username}' \
-v kp_default_repository_password='{password}' \
-v pull_from_kp_default_repo=true \
-v tanzunet_username='' \
-v tanzunet_password='' \
| kbld -f bundle/.imgpkg/images.yml -f- \
| kapp deploy -a tanzu-build-service -f- -y
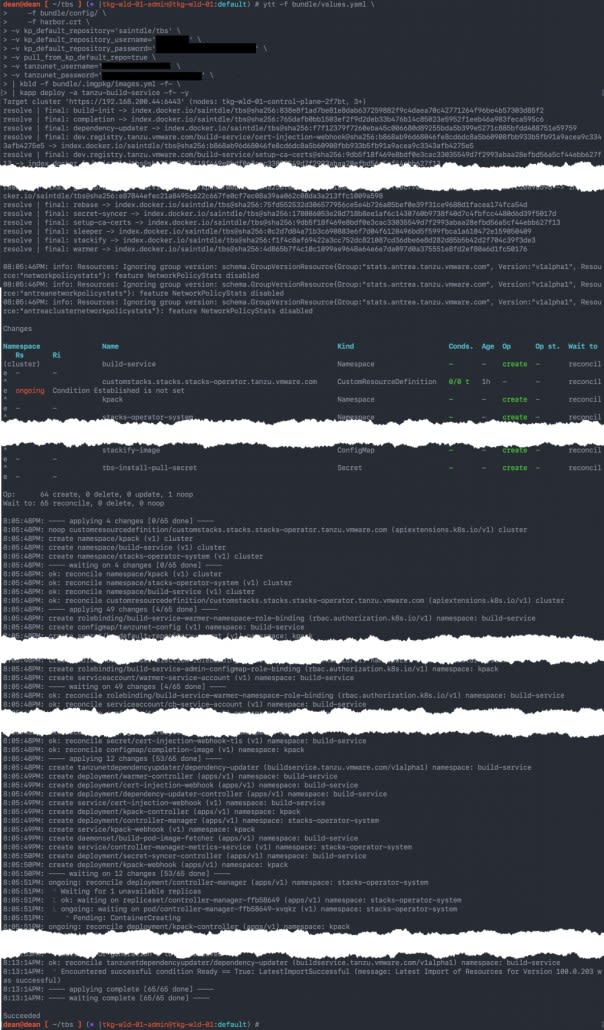
Below is a concatenated output once the command is run.
To check the installation
kp clusterbuilder list
(Re)Building the Pac-Man Application
Now that Tanzu Build Services is deployed within my cluster. Let’s look at taking an existing application and repacking it into a container using the functions of Tanzu Build Services to inject various layers into the container and resolve issues such as vulnerabilities.
I use the same Pac-Man application in my demos, as it’s fun, but also does somewhat mirror a real-world application, as it has a web front end and a database backend.
The Web Front end is a container built by Ivan Font.
- quay.io/ifont/pacman-nodejs-app:latest
Ivan has also provided his Dockerfile for this container here:
I forked this repo, and then without making any changes currently. I ran the commands for Tanzu Build Services to build me a new container and fix some of the dependency issues straight away.
First, we need to create a secret for the kp tool to use to upload our images to the registry.
kp secret create my-dockerhhub-creds --dockerhub saintdle
# you will be prompted to enter the password for the account
Next, we run the command to compile the new image.
kp image create pacman-test3 --tag saintdle/pacmantest:0.1 --git https://github.com/saintdle/pacman.git
# specify a certain branch
kp image create {name} --tag {repository location to create image} --git {git url} --git-revision {git branch or commit}
We can then monitor the build process with the following commands.
kp build list pacman-test3
# you can add the watch command infront of this to cycle the command/response
watch kp build list pacman-test3
You can view further build details by viewing the logs.
kp build logs pacman-test3
The build process goes through the following stages, and you check out the full output in my example in the image below:
- Setup CA certs for the repo that the process is pushing the image to
- Prepare the source files
- Detect the build packs that will be needed for this image build run
- Analyze if any elements reuse existing cached data
- Restore any cached data as needed
- Build our new image
- Export our image to our container image registry
- Completion – finalisation messaging
Testing the new Image
As I’m doing this as a first look and not really reading any documentation and jumping straight in, I don’t have this as part of a CI/CD pipeline.
I just ran the new container image in docker locally on it’s own to make sure it works and exposed the port 8080 to port 80.
Locally on my machine Pac-Man loads. However, fitting this into a wider deployment, there are more considerations to think about. And that is for another day and another blog post.
Comparing the original and new images
I uploaded the original container image and new container image to a Harbor repository, so that I could use the Trivvy Scanner functions to see the vulnerabilities in both container images.
The below screenshot shows the original container image that I’ve been using. As we can see there are a high number of issues that need to be addressed.
Below is my new container image built by Tanzu Build Services. As you can see there is far less CVEs reported, and the container image size is also a lot smaller as well.
The key thing here to note is, I have changed nothing here with the original dockerfile used to create the containers. I’m simply run this through Build Services, which has discovered the components, and made decisions about how this is packaged together.
Wrap up
In this blog post, I’ve covered a very quick setup in a lab environment to look at how Tanzu Build Services works and run a dockerfile of an existing application through it.
There is a lot more to cover here though:
- How to troubleshoot builds,
- How to tailor builds to specific needs
- Updating images when the sources are changed or have new commits
- Bringing this into a full CI/CD pipeline and tool chain
And I assume even more items I’m not currently considering.
Regards
The post First Look – Setup Tanzu Build Services and rebuilding Pac-Man appeared first on vEducate.co.uk.








Top comments (0)