What is a Proxy Server and How Does it Work?
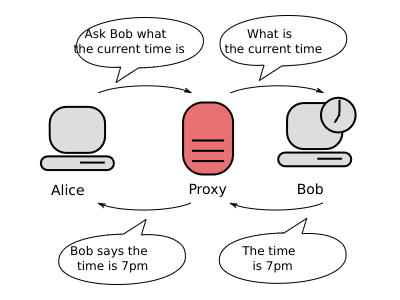
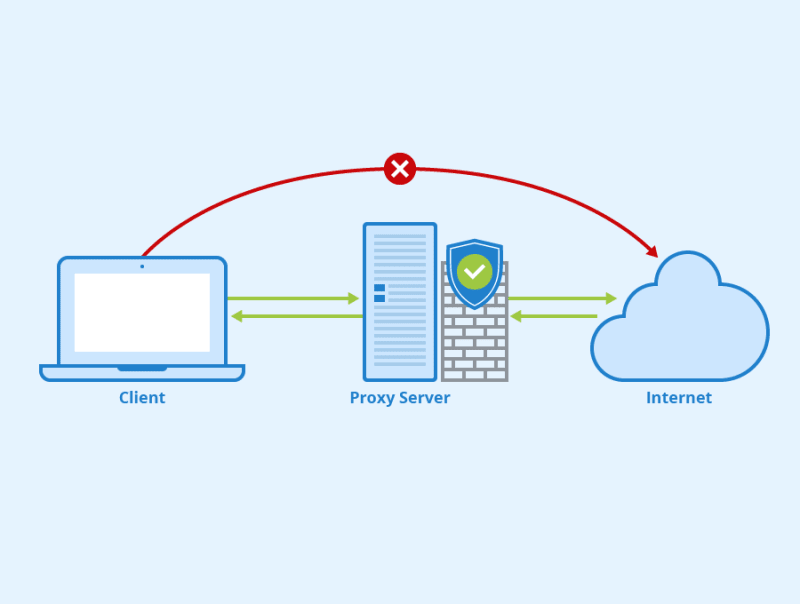
A proxy server acts as an intermediary between a user’s computer and the internet. When you use a proxy server, your internet traffic is routed through the proxy, which makes requests on your behalf. This can enhance privacy, improve security, and allow you to bypass content restrictions.
Types of Proxy Servers
-
Forward Proxy
- This is the most common type of proxy. It sits between a client and the wider internet, forwarding client requests to the internet. It can cache data, filter content, and manage bandwidth usage.
-
Reverse Proxy
- Reverse proxies handle requests from the internet to internal servers. They are often used for load balancing, caching static content, and enhancing security by hiding the details of backend servers from the client.
-
Web Proxy
- Specifically designed for web traffic, web proxies handle HTTP and HTTPS requests. They allow users to browse the internet anonymously by masking their IP addresses.
-
Anonymous Proxy
- These proxies hide the user’s IP address from the destination server, offering a basic level of anonymity. They are commonly used to prevent tracking and protect user privacy.
-
High Anonymity Proxy
- High anonymity proxies provide a higher level of privacy by frequently changing IP addresses and ensuring that the proxy server itself is not identifiable as a proxy.
-
Transparent Proxy
- Transparent proxies do not modify the request or hide the user’s IP address. They are often used in organizational settings for content filtering and caching.
-
Distorting Proxy
- These proxies provide a fake IP address to the destination server, offering an additional layer of anonymity by hiding the user’s true IP address.
-
Rotating Proxy
- Rotating proxies change the IP address for each request, providing higher levels of anonymity and reducing the risk of IP bans.
How Proxy Servers Work
-
Client Request
- The client (your computer) sends a request to access a resource on the internet. This request is directed to the proxy server instead of directly to the destination server.
-
Proxy Server
- The proxy server receives the client’s request, processes it, and then forwards it to the destination server. The destination server sees the request as coming from the proxy, not the client.
-
Fetching the Resource
- The destination server processes the request and sends the response back to the proxy server. The proxy server then relays this response to the client.
-
Caching
- Proxy servers often cache the responses from destination servers. If another client requests the same resource, the proxy can deliver it directly from its cache, improving load times and reducing bandwidth usage.
Benefits of Using Proxy Servers
-
Privacy and Anonymity
- By masking your IP address, proxies can help protect your identity online and prevent tracking by websites.
-
Security
- Proxies can filter malicious content, block access to harmful sites, and protect against some types of cyber attacks.
-
Access Control
- Organizations use proxies to restrict access to certain websites, ensuring that employees or users adhere to usage policies.
-
Bandwidth Savings and Speed
- Caching frequently accessed content reduces bandwidth usage and improves loading times for users.
-
Bypass Restrictions
- Proxies can help users bypass geographical restrictions and access content that might be blocked in their region.
Risks and Considerations
-
Lack of Encryption
- Most proxies do not encrypt your traffic, leaving it vulnerable to interception by hackers or third parties.
-
Trust Issues
- Users must trust the proxy server provider as it can potentially monitor and log user activities.
-
Performance
- Proxies can introduce latency and slow down internet connections, especially if they are overloaded or poorly configured.
-
Legal and Ethical Concerns
- Using proxies to bypass restrictions or access blocked content can sometimes violate terms of service or local laws.
Proxy servers are versatile tools that can enhance your online experience by providing privacy, security, and access control. However, it’s essential to choose the right type of proxy and understand its limitations and risks.
For more detailed information on proxy servers, you can visit resources such as Kinsta, Wikipedia, TechRadar, and AVG.







Top comments (0)