Have you ever been on a Public Network ?
I'm sure you had. We all had.
Nevertheless, if you did so, you opened your entire computer at risk. Because it then become vulnerable to Man in the Middle attack that can then lead to other attacks (Cookie spoofing, XSS, etc...).
Because I do believe into learning by doing, I made a Youtube video (french audio, english subtitles) to explain the theory of a Man in the Middle attack, show you a real attack in a CTF and then teach how you can get yourself much more protected to MitM attacks.
You can watch it here :
or read it below in a nice article.
1. The Theory behind Man in the Middle Attacks
Man in the Middle Attacks are pretty simple to understand.
Two people are communicating over a network and someone is just going to impersonate each of them to the other.
Let's make a quick picture of it.
You have two people. Let's call them Alice and Bob (see why here).
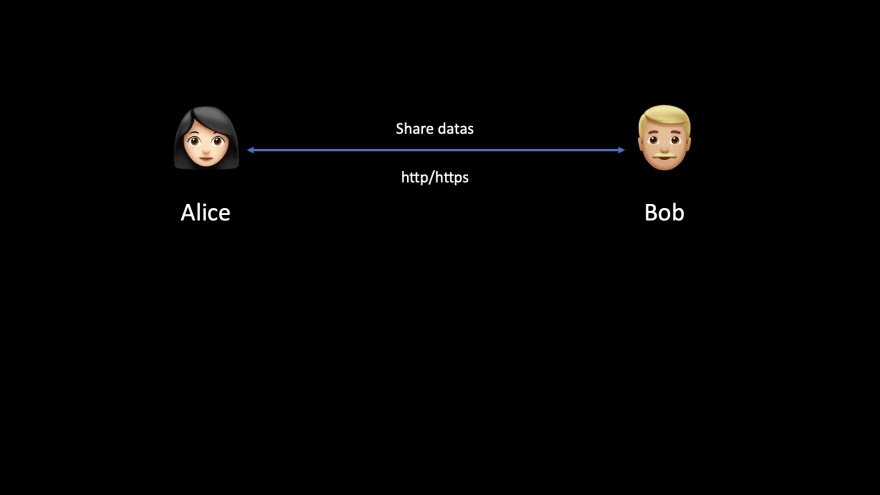
And someone wants to listen to what they are saying to each other. Let's call her Eve (see why here).
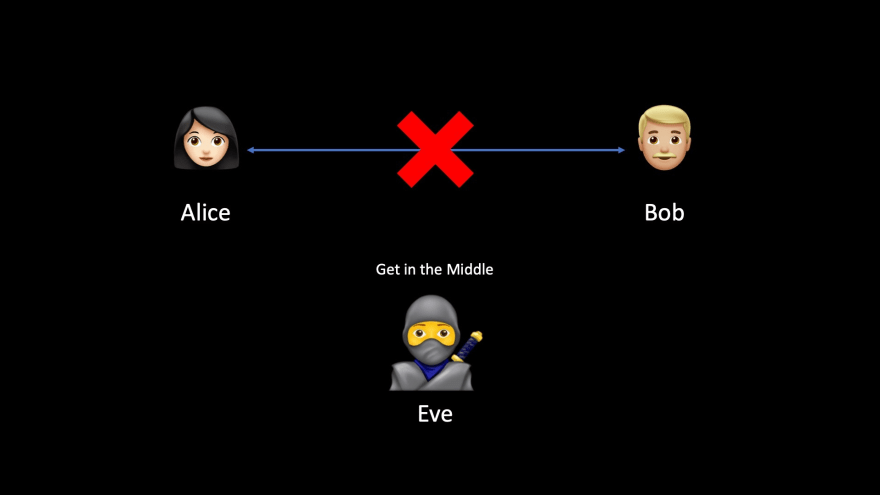
There are a lot of methods to get in the Middle. ARP Spoofing is the most common.
Now that Eve is in the Middle.
She is pretending to be Alice to Bob and she is pretending to be Bob to Alice.
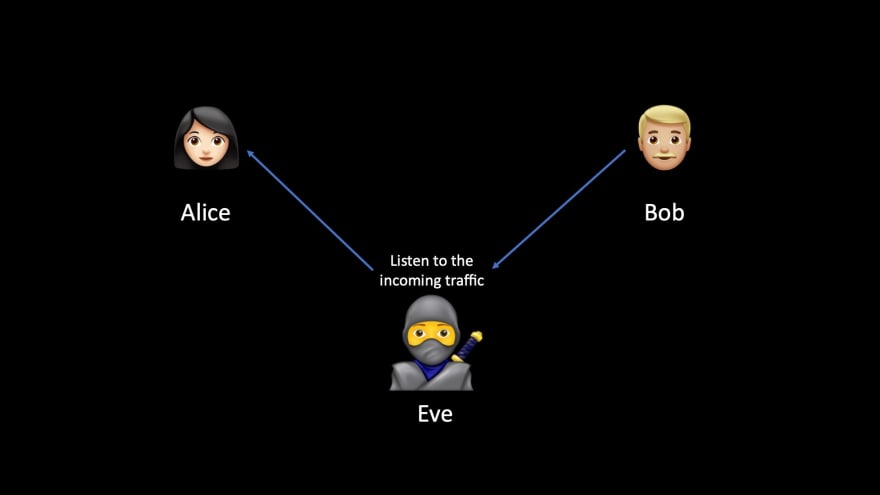
Eve can just listen to the communications silently.
Or Eve can modify the communications and send modified request or response to Alice and Bob.
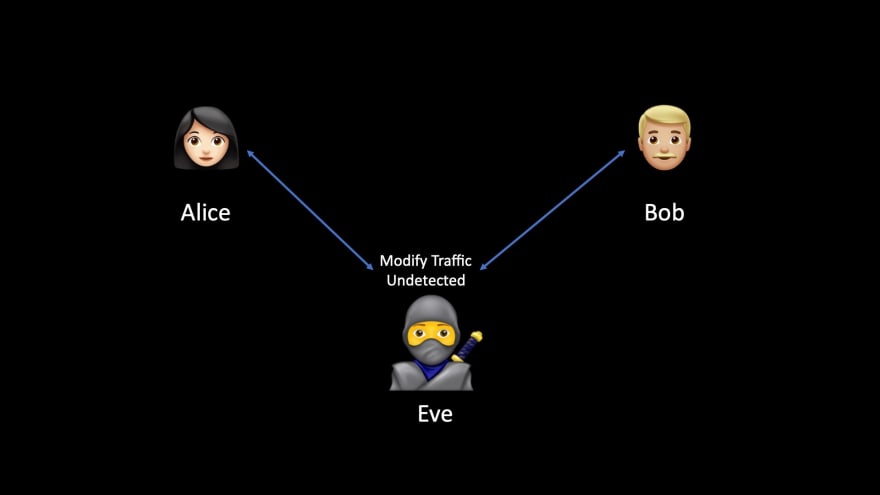
It can help to steal things (like cookie to your Gmail account, even if you are not browsing your Gmail account).
This can be pretty bad as Eve can be totally unnoticed to both Bob and Alice.
Here is a sum up of all the steps.

2 - Man in the Middle Attack - Hands on
You can see it here in a lab (designed for that) at 4:18 from a video I made to explain all Man in the Middle Attacks related.
Video starting at the Labs Step
or
The all video :
3 - Steps to Up your Game against MitM Attacks
OK, now you understand how easy it is for an attacker to get in the middle, unnoticed and gather a lot information from your computer or impersonate your identity to do things.
But how can we stay protected from it ?
1 - Don't connect to Public Wifi is the most easy way to stay safe.
If you don't connect to this nasty Public Wifi, no one can connect to your computer.
2 - Remove the Public Wifi ssids from your list of "auto-connect" ssids.
Why ?
Because as soon as it is in your computer list of "auto-connect" ssids, an attacker can create a Wifi Hotspot named Starbucks and your phone or computer is going to connect to it automatically. Because it's what you asked for.
Usually your iPhone's hotspot is named "iPhone" and you have a wifi password to connect to it but you can name whatever you want and remove the Wifi password.
Make an experiment, name it "Starbucks", remove the Wifi password and look at how many people are connecting to it.
No imagine doing that with a Raspberry Pi Zero (it costs 5$, that's pretty cheap) and you leave it on in a Starbucks and just exfiltrate any peace of data that is going through it.
That's pretty easy and pretty cheap.
3 - Use a VPN
A VPN or Virtual Private Network is a piece of software that runs on your computer or phone and that encrypts any data that is going out of your device and decrypt any data that is going in your device.
But, it goes through the VPN service provider infrastructure, so, you have to really trust that VPN service provider to leave your data alone (ie. do your research about that VPN provider you are about to use 😉).
If you use a VPN for your communication, an attacker can still get in the middle. It can read your communication. Nevertheless, that doesn't mean anything because everything is encrypted, thanks to the VPN. So, it is pretty useless for an attacker.
4 - Be Sure that you are using HTTPS
You should always check that the website you are visiting is using https.
That means, that the communication are encrypted between the client (you) and the server (the website). It makes things a little harder for an attacker to understand your communication when it is encrypted.
5 - Use Certificate Pinning whenever you can
On mobile application, you can use Certificate Pinning which makes it impossible for an attacker to use a self-signed certificate it pushed on your machine as a legit certificate.
The only valid certificate is the one that was pushed at the build time and integrated into the application.
If you are developing iOS or Android application, be sure to always use certificate pinning.
And that's pretty much it.
I hope you enjoyed that article about Man in the Middle attack and enjoyed the video (especially about the hands-on attack).
Feel free to ask me any question in the comment below if you want to know more how to try this method against your website to see if you can be vulnerable to this kind of attack.
Cheers
Video produced by Wild & Secure, your consulting firm to all things security and real estate.
If you want to receive weekly quality content about security, subscribe to our newsletter on our website.







Top comments (0)