What is ECC?
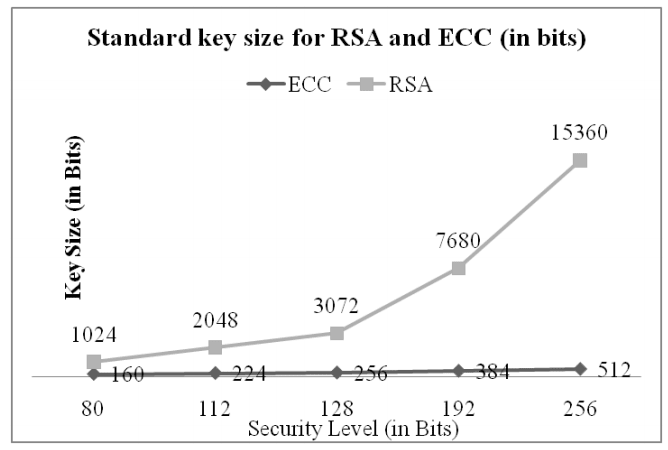
ECC is the latest encryption method. It stands for Elliptic Curve Cryptography and promises stronger security, increased performance, yet shorter key lengths. This makes it ideal for the increasingly mobile world.
How to reduce 20% Data Transfer in EC2 step by step and not die trying
Install Certbot:

Certbot is a fully-featured, extensible client for the Let’s Encrypt CA (or any other CA that speaks the ACME protocol) that can automate the tasks of obtaining certificates and configuring webservers to use them. This client runs on Unix-based operating systems.
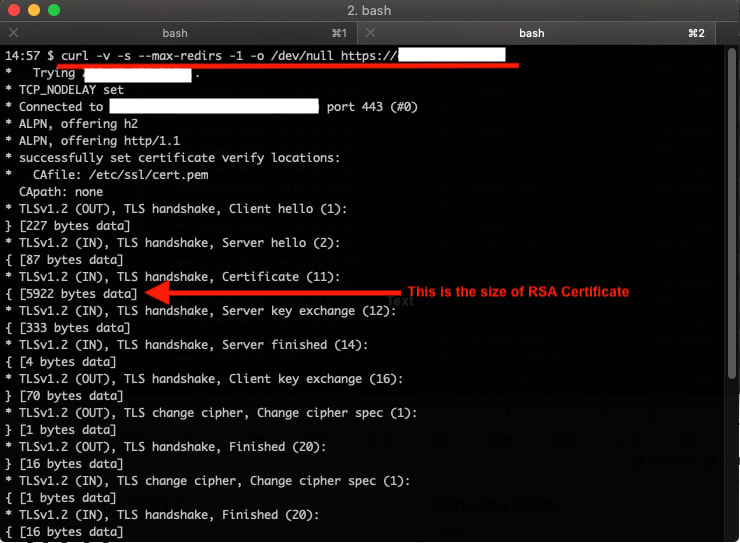
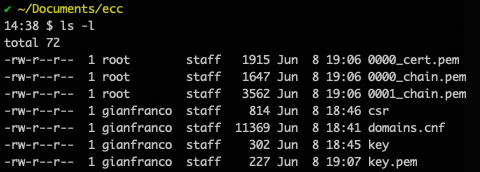
First, go to measure the size of our RSA Certificate with the following command:
Step 1: generate ECC key
mkdir ecc
cd ecc
openssl ecparam -name prime256v1 -genkey > key
Step 2: create a copy of OpenSSL config file
cp /etc/ssl/openssl.cnf domains.cnf
Step 3: editing config file
nano domains.cnf
Look for [ req ] section. Find add uncomment following line:
req_extensions = v3_req
If you don’t find a line like above, you can add one.
In [ v3_req ] section, add following line:
subjectAltName = @alt_names
It will look like:
[ v3_req ]
# Extensions to add to a certificate request
basicConstraints = CA:FALSE
keyUsage = nonRepudiation, digitalSignature, keyEncipherment
subjectAltName = @alt_names
Finally add a new section called [ alt_names ] towards end of file listing all domain variation you are planning to use.
[ alt_names ]
DNS.1 = *.example.com
Now you have your OpenSSL config file ready.
Step 4: generate Certificate Signing Request
Next, we will generate CSR using private key above AND site-specific copy of OpenSSL config file.
openssl req -new -sha256 -key key -out csr -config domains.cnf
Step 5: use Certbot to deploying Let’s Encrypt certificates.
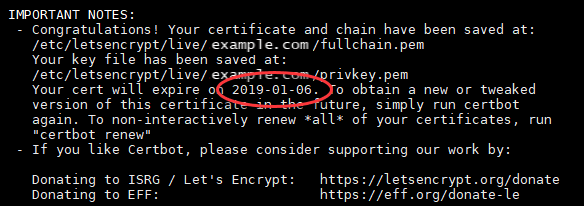
sudo certbot certonly --manual --key key --csr csr --preferred-challenges=dns --register-unsafely-without-email -d *.example.com
and it looks like:
Step 6: SSL Challenge
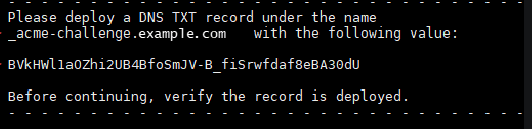
Now, go to Route 53, and find the Hosted Zone “application”. And then paste the value as TXT record:
Finally, they will see something like this:
The next step is to convert the key into a .pem:
openssl ec -in key -out key.pem
They should have this:
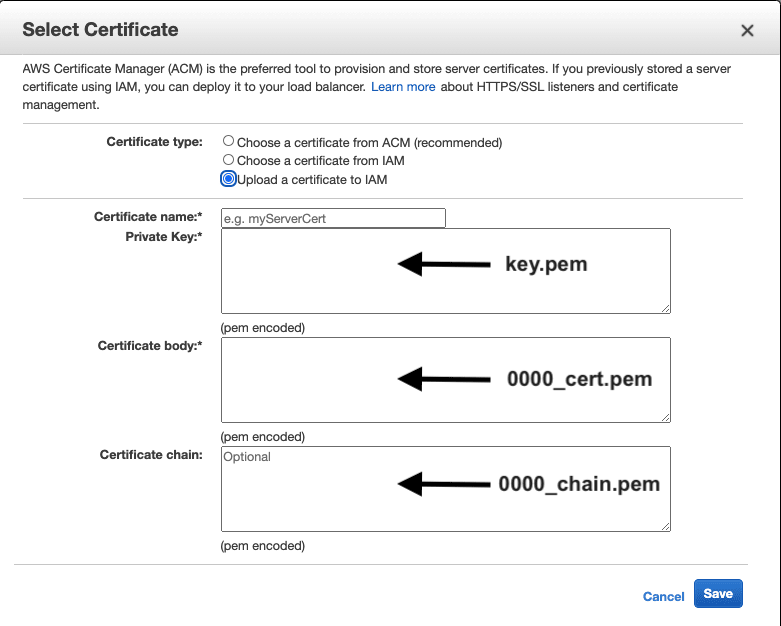
Now, go to AWS Console => Load Balancers => Listeners => Upload a certificate to IAM.
Paste the following keys:
Click to save and Enjoy!
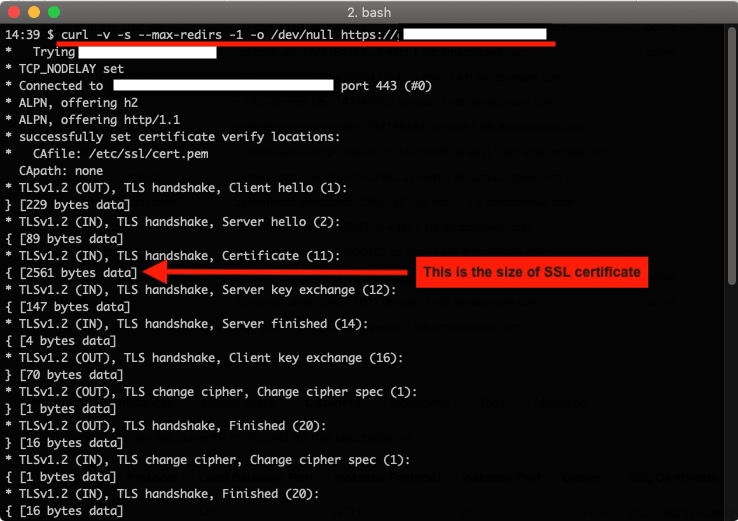
Finally, we can check the size of ECC Certificate with the following command:








Top comments (0)