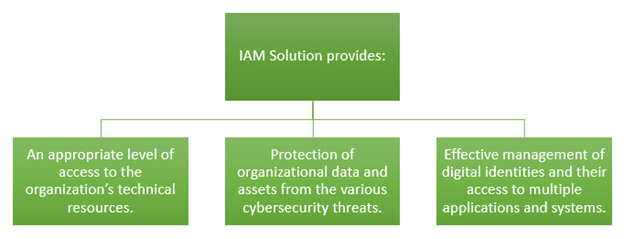
Criminal hacking, phishing, and other malware threats are growing at a fast pace. Today, it has become an alarming situation for every organization. Not only does it lead to financial loss, but it also results in brand value loss. To combat this, we need a robust solution like the IAM solution. Why? Have a look:
Now that you’re familiar with the benefits of IAM to your business. Let us move forward and discuss the best IAM tools and security protocols that can help your organization effectively manage complete privacy and cybersecurity concerns. Keep reading.
Top 3 IAM Tools for Business

Robust Security Protocols for Successful IAM
There are three significant protocols for IAM that controls data access without hampering operations and productivity.
Multi-Factor Identification
It is a security system that incorporates multiple authentication methods. It uses different and independent categories of credentials to validate the user’s identity for login, transactions, and other activities.
Identity Management Assessment
It is crucial to safeguard user identities via an access control mechanism. Enterprises various strategies and assessment services that help in:
Meeting business goals & objectives
1.Decreasing the risk of identity fraud and insider threat
2.Empowering collaboration and productivity
3.Managing regulatory compliances
4.Improving operational efficiency and cost-effectiveness
Implementation and Integration
It includes advanced integrations like ML, AI, biometrics, and risk-based assessment across multiple devices and geographic locations. Also, it ensures the safety of organizational data from both external and internal threats.
Summing Up
With the fully-fledged tools and protocols integrated into your IAM solution, you'll get robust security for your business. An effective and scalable IAM implementation requires excellent domain specialists.
At, Successive Technologies, you will get the best and certified IAM specialists who will take your business to the next level with their security-driven solutions. We help enterprises implement security protocols that manage data access control without hampering productivity. Contact us to get started.



Top comments (0)