Hey there!
Have you ever asked yourself who has access to my AWS resources? or who outside of my account has access? Honestly, the second one most important, because nobody wants to be a subject of news about a new data breach :). AWS made a tool for us to figure it out. It is called IAM Access analyzer. You can find it in the IAM Service.
Short overview
In a few words, what it does, it evaluates your resource policies and finds all external principal that has access to resources in your account. It takes your account as the zone of trust and informs you about everything outside of the zone, but has access to the zone.
Other important things worth to mention:
- Access analyzer is region-specific, so you have to enable it for each region, where you want to use it.
- Access analyzer currently supports a limited list of resource types
Ok, enough for theory, time to practice.
Practice
You can find the Access analyzer in IAM. For creating a new Analyzer just press create and provide a name or use default one.
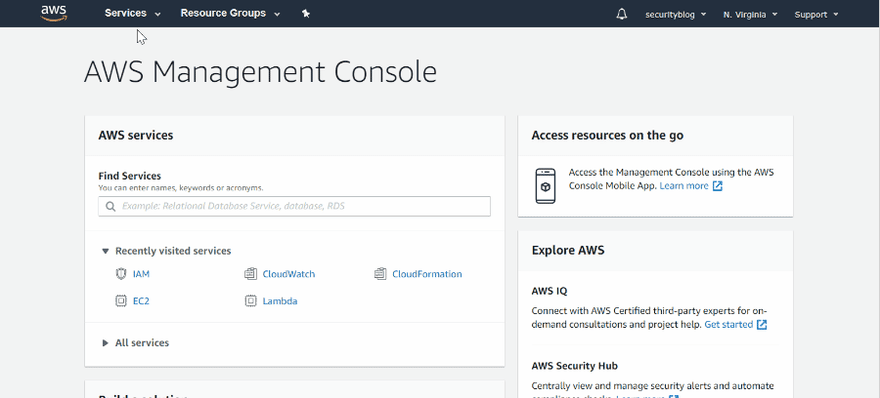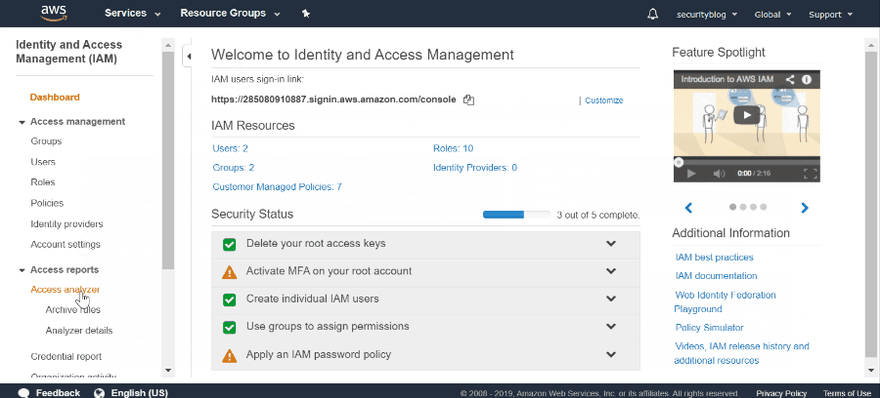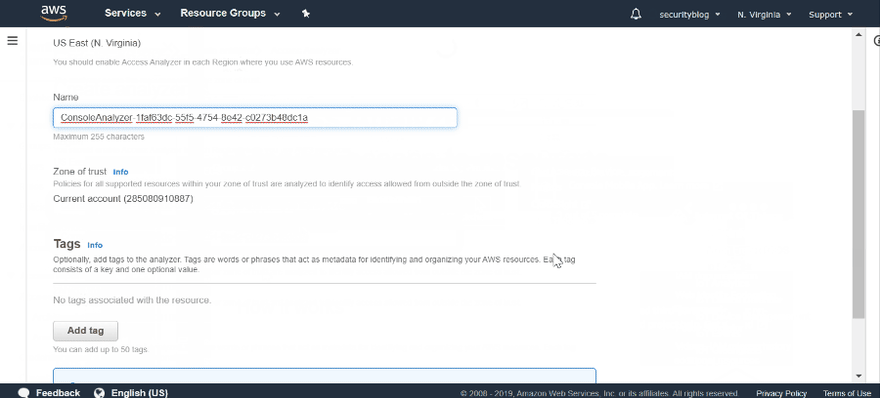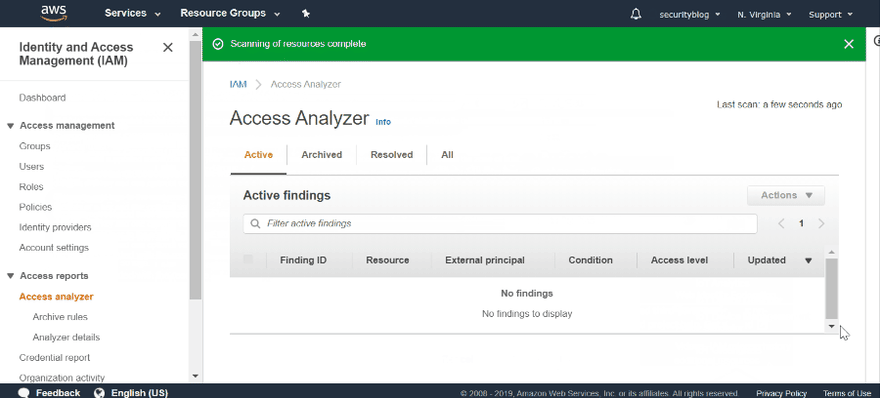
Once the scan is done, you may see all the findings. Yes, it is such simple. At first, you have to go through all findings and either archive or resolve them. Archiving means that access is intended, once you archive a finding it will not appear till resource policy will be changed again. The resolve status appears only after you fix unintended access and it obviously means that found access does not exist anymore.
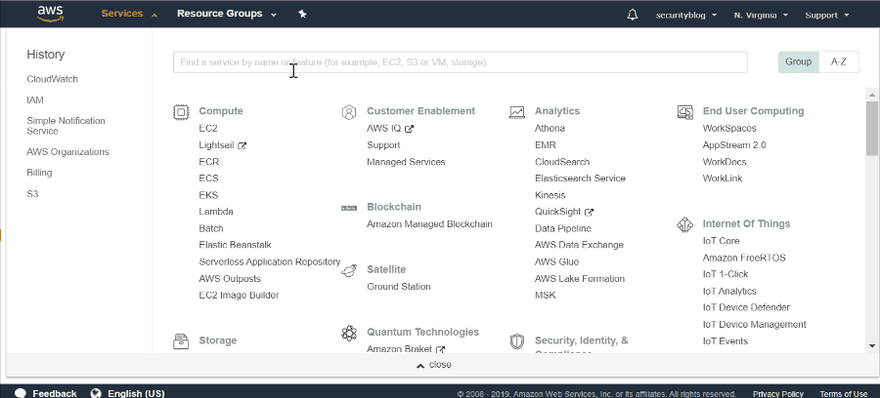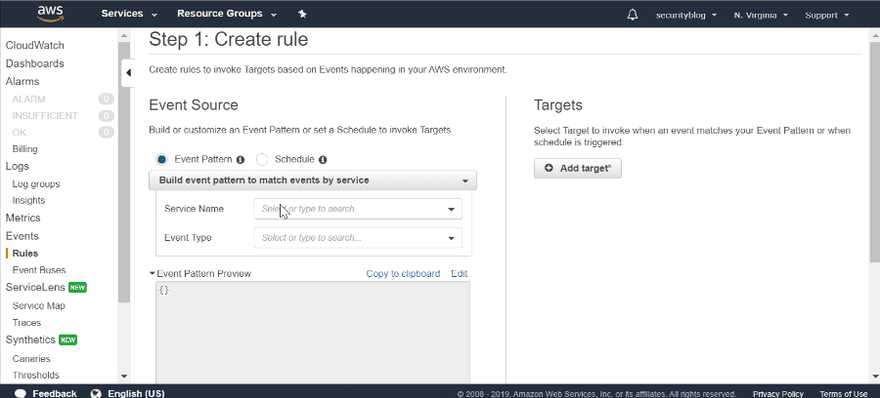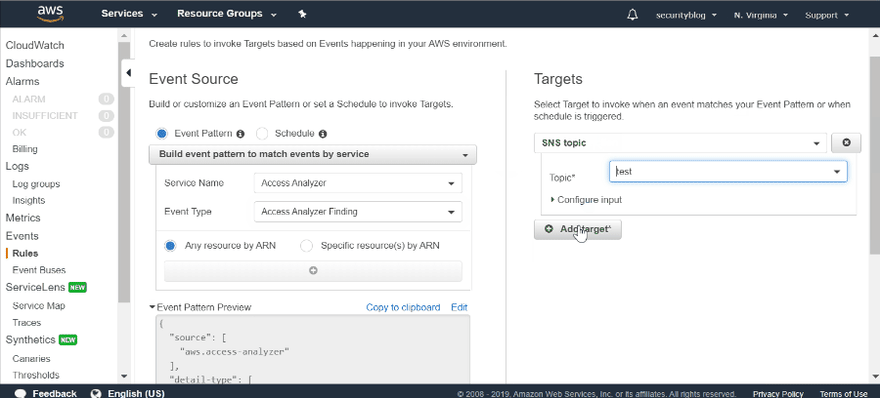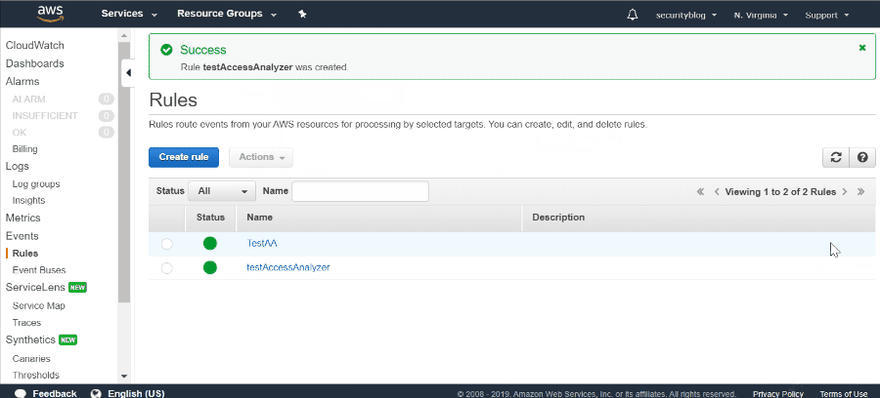
After you are done, you probably would like to receive notification about new findings. You can do it via CloudWatch Events. Just create a new rule and define necessary action for new findings. I've used SNS topic to send an email once new findings appear.
If you want to white-list some resources or external principal you can use archive rules for it. Go to Archive rules click add and define a condition.
Access analyzer is fast to implement and simple to use tool that you definitely need to check out.







Top comments (0)