The continuation of the The AWS Well-Architected Framework and it's 5 Pillars Series.
For the others who haven't yet read the initial part of this series, please read the previous parts above or below this article.
Let's continue on diving deep and this time let's venture the Security realm to gain knowledge on what are the key areas, what questions you must conquer and what are the key phases involve in this pillar for us to satisfy it's standards.
Security
... the ability to protect information, systems, and assets while delivering business value through risk assessments and mitigation strategies...
Simply saying, We need to ensure that our workload will ONLY work as intended
To satisfy this pillar, your architecture needs to apply the best security practices by being aware on these key areas:
- Identities have the least privileges required
- Know who did what? When?
- Security is woven into the fabric of the system
- Automate security tasks
- Encrypt data in transit and at rest
- Prepare for the worst
Phases
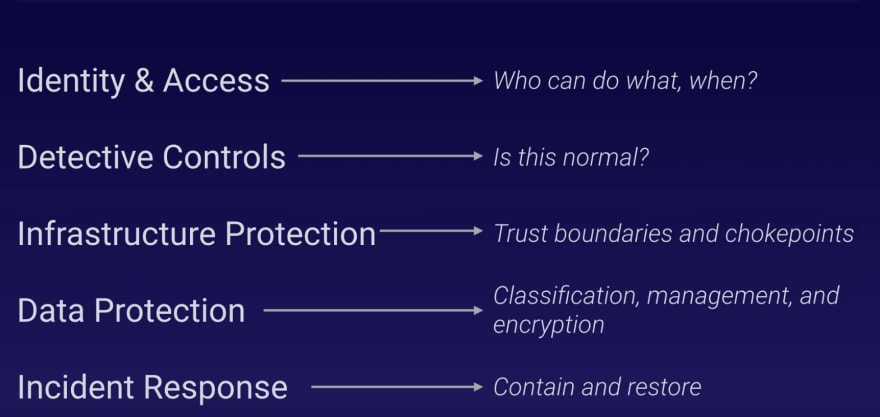
Identity Access Management (IAM)
Only authorized and authenticated users can take action:
- Who is allowed to do what? when?
- Are you applying least privileges
- Deny root and full access
- Regularly review access and privileges
Detective Controls
Look for abnormal behavior in your workload:
- Capture and analyze logs
- Regularly audit controls and configurations
- Look for unauthorized or unexpected changes
- Monitor workload behavior for abnormalities
Infrastructure Protection
Defense in depth:
- Establish trust boundaries
- Protect network in/out
- Protect all hosts
- Configure services to meet security posture needs
- Enforce service level protection
Data Protection
Classify and protect your data:
- How sensitive is the data
- Who should have access? when?
- Encryption in transit
- Encryption at rest
- Back and test backups of data
Incident Response
Contain and recover from unplanned events:
- Do you have a plan to tag affected resources?
- Can you adjust permissions to allow for containment?
- Can you redeploy to recover quickly?
- Did you learn from the incident and adjust?
The key takeaways in this pillar is Built-In, Not Bolt-On - Security is a critical part of the fabric of your workload. Whatever you built you need to ensure that it is doing what you want it to do, and only that.
Overall, the Well-Architected Framework and together with its pillars are the guiding lights on achieving value to you business.
Remember, it's all about balance, finding the right balance at the same time making trade-offs that depends on your workload.
Follow or Connect with me:







Top comments (0)