🌟 What is RMF and why is it important? 🌟
RMF stands for Risk Management Framework, a guideline, standard, and process for risk management to help secure information systems (computers and networks) developed by National Institute of Standards and Technology (NIST)¹. RMF is the “common information security framework” for the federal government and its contractors⁴.
RMF is important because it provides a comprehensive, flexible, repeatable, and measurable 7-step process that any organization can use to manage information security and privacy risk for organizations and systems². RMF also links to a suite of NIST standards and guidelines to support implementation of risk management programs to meet the requirements of the Federal Information Security Modernization Act (FISMA)². FISMA is a law that requires federal agencies to develop, document, and implement an information security program to protect their information and information systems².
📚 How does RMF work? 📚
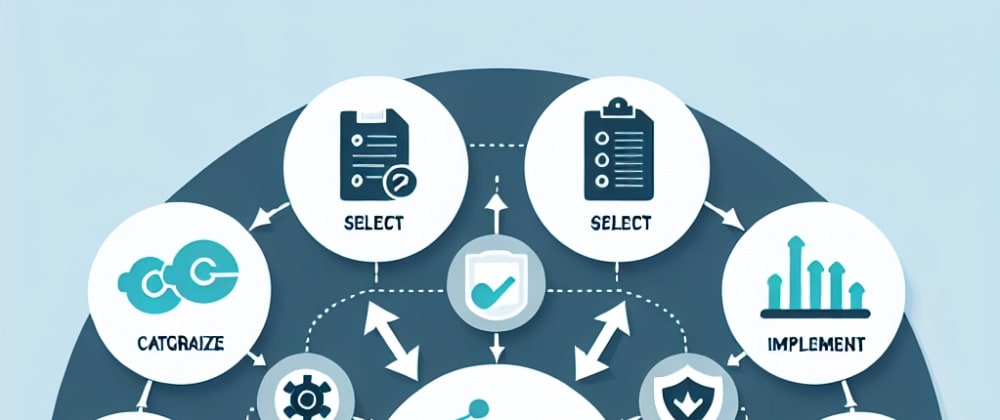
RMF works by following a 7-step process that integrates security, privacy, and cyber supply chain risk management activities into the system development life cycle². The system development life cycle is a process of planning, developing, testing, deploying, operating, and maintaining an information system². The 7 steps of RMF are:
- Prepare: Essential activities to prepare the organization to manage security and privacy risks². This step involves establishing the context for risk management, such as defining roles and responsibilities, identifying laws and regulations, developing policies and procedures, allocating resources, and conducting training².
- Categorize: Categorize the system and information processed, stored, and transmitted based on an impact analysis². This step involves determining the potential impact of a loss of confidentiality, integrity, or availability of the system or information on the organization's mission, operations, assets, or individuals².
- Select: Select the set of NIST SP 800-53 controls to protect the system based on risk assessment(s)². This step involves choosing a baseline of security and privacy controls from NIST SP 800-53 that are appropriate for the system's categorization and tailoring them according to the specific needs and environment of the organization².
- Implement: Implement the controls and document how controls are deployed². This step involves applying the selected controls to the system in accordance with the specifications in the security plan and documenting how they are configured and integrated².
- Assess: Assess to determine if the controls are in place, operating as intended, and producing the desired results². This step involves conducting independent testing and evaluation of the controls to verify their effectiveness and identify any weaknesses or deficiencies that need to be addressed².
- Authorize: Senior official makes a risk-based decision to authorize the system (to operate)². This step involves reviewing the assessment results and other relevant information to determine if the system's risks are acceptable or unacceptable for the organization².
- Monitor: Continuously monitor control implementation and risks to the system². This step involves collecting and analyzing security-related information from various sources to maintain situational awareness of the system's security posture and respond to any changes






Top comments (0)