Welcome back to the Identity Trends blog series! The first post provided a comprehensive guide to leading identity trends—check it out here if you missed it. The next three posts will dive deeper into each of the major trends and explore how Prove solutions can help you stay ahead of the game. Today, we’ll be focusing on Trend #1: Passwordless Authentication.
What is Passwordless Authentication?
As its name suggests, passwordless authentication uses factors other than traditional passwords, such as biometric data (fingerprints, facial recognition, or iris scans), hardware tokens, and other forms of digital identification to verify the identity of a user. There are many different benefits to going passwordless from both a security and user experience perspective.
What are the benefits of going passwordless?
Did you know that roughly ⅓ of online purchases are abandoned at checkout because consumers cannot remember their username and password? Considering that the average consumer has around 100 passwords and usernames to remember, the rate of cart abandonment is not surprising. In addition, because consumers have too many passwords to remember, they often use the same password across different accounts, creating a dangerous domino effect in which a data breach at one company can result in dozens of accounts being compromised per user. As a result, many companies are phasing out passwords and replacing passwords with more secure options to improve user experience, bolster security, and boost their bottom line. That’s where Prove Auth comes in.
With the increasing prevalence of cybercrime, it's more important than ever to protect ourselves from hackers and identity thieves. Fortunately, there's a technology that is changing the game when it comes to online security: Prove Auth.
Prove Auth
One of the major benefits of Prove Auth is that it is incredibly user-friendly. Instead of requiring users to remember complex passwords and constantly reset them, Prove Auth works seamlessly in the background, verifying their identity without any extra steps or hassle. Plus, because it is based on real-time data analysis, Prove Auth can detect and respond to potential security threats in seconds, ensuring the user’s information stays safe and secure.
But what about privacy concerns? With so much personal information being shared online, it's understandable to worry about how that data is used. Prove Auth is designed with privacy in mind, using secure encryption protocols to protect your information and keep the user’s data anonymous and confidential. And because it works in real-time, Prove Auth doesn't store sensitive data on your device or in the cloud, minimizing the risk of a data breach.
Keep reading for details on our Prove Auth Flow as we dive deeper into how to integrate Prove Auth. Prove Auth is an umbrella service representing various forms of authentication. The product currently consists of Device Auth and Mobile Auth.
Device Auth
Device Auth is a form of passive authentication where the enterprise can verify the possession of the phone in real-time without any interaction from the user. Mobile Auth is also a form of passive authentication where the possession of the phone happens in real-time with coordination from the MNOs (mobile network operators). Prove Auth provides flexibility by allowing control of which authentication forms to execute for any given use case.
Mobile Auth
Mobile Auth is based on a 3-call flow; the first and last calls are handled in a server-to-server environment, while the intermediate step occurs on the phone being queried.
Our Server Integration Guide outlines how to implement the two API calls of /authenticateByRedirect and /authenticateByRedirectFinish in an API-only flow.
Our Native App SDK Integration Guide and Web SDK Integration Guide cover integrations on the device through one of Prove’s SDKs—whether through an app or mobile web browser—providing a quick and easy way to retrieve the data needed, even if your user is on Wi-Fi. This is important for the Device Auth call.
Mobile Auth Flow
The first step is orchestrating a server-to-server call to the /authenticateByRedirect endpoint, which requires the device IP of the cellular connection. The second step is a middle call that the Prove SDK handles; this happens over a cellular connection and attempts to reach the authentication URL (redirect URL). The third step takes the response from the second step, which is then passed to the client’s backend, making a server-to-server call to /authenticateByRedirectFinish. It’s important to note that the customer’s app must complete steps one and three, and is not done by the SDK. The SDK orchestrates when steps one and three are to be executed.
The mobile SDK provides a quick and easy way to retrieve the data needed to make those server-side calls. In addition, since the middle call must happen over the cellular network, the SDK helps by retrieving the cellular IP address of the device and potentially performing a Wi-Fi override for the middle call.
First Call: /authenticateByRedirect
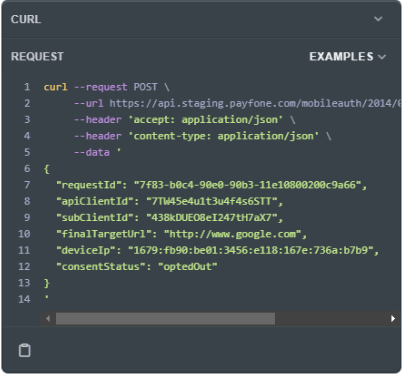
The first server-to-server call, the /authenticateByRedirect endpoint, requires the mobile device's cellular IP from the mobile data session, entered in the “deviceIp” field, plus the URL for your server needed for the mobile device to send the verification fingerprint (VFP, i.e., a one-time, time-bound authentication for unique identification) via the “finalTargetUrl” field.
The “RedirectTargetUrl” generated in the response is a one-time, time-bound authentication URL with the first VFP specifically for this mobile device and request. The VFP value is a one-time use key that ensures that man-in-the-middle attacks are impossible.
Middle Step: Device Auth
Next, the mobile device must execute an HTTP GET directly to the “RedirectTargetUrl” returned from the /authenticateByRedirect call; the device makes the request directly to Prove and is authenticated.
The network enriches the request with subscriber identifying information, typically encrypted into a new, one-time use, time-bound, SIM-signed VFP token that is shared back to the device. The new VFP returns in the HTTP 200 or 302 responses, even in the case of an error. The 302 response in the web browser implementation returns the device to the FinalTargetUrl specified in the first call, which then starts the final call of the flow.
See our Native App SDK Integration Guide and Web SDK Integration Guides for details on integrating Device Auth.
Final Call: /authenticateByRedirectFinish
The final API call, the /authenticateByRedirectFinish endpoint, obtains the results of authentication from the second call, passing the “verificationFingerprint” (VFP) value returned by the mobile device.
If successful, the “MobileNumber” associated with this particular consumer is returned to your server in this step, indicating Mobile Auth has been completed.
Overall, Prove Auth is an excellent choice for passwordless authentication. It’s perfect for businesses and organizations prioritizing security and protecting their sensitive information from unauthorized access. In addition, its use of MFA and fraud detection algorithms and ease of use make it a reliable and effective authentication solution. Using Prove Auth, businesses can ensure that their online accounts and services are secure and their customers' data is protected.









Top comments (0)