Part 01: https://dev.to/randiakm/deploying-apps-to-aws-with-terraform-01-3fne
2. What we are going to build
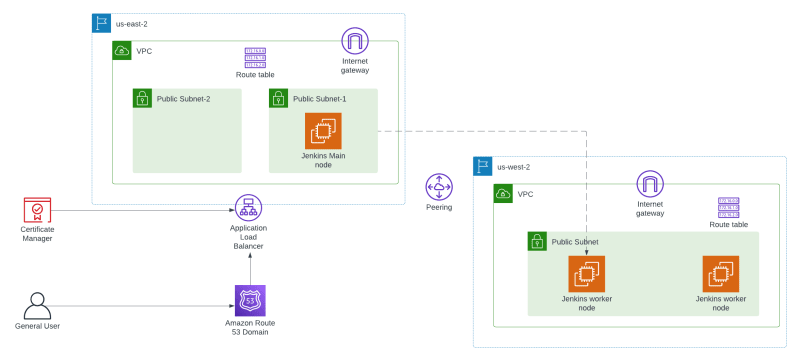
We are going to focus on constructing a sophisticated, distributed Jenkins CI/CD Pipeline across multiple regions.
Deployment Overview:
The core of our project involves deploying a multi-region Jenkins CI/CD Pipeline, specifically across two AWS regions: us-east-2 and us-west-2. Our deployment strategy is detailed and comprehensive, ensuring a solid foundation for our CI/CD pipeline.
Initial Setup:
We start by establishing Virtual Private Clouds (VPCs) and public subnets in both regions, along with essential security groups. This foundational step is crucial for creating a secure and isolated network environment for our pipeline.
Inter-Region Communication:
To facilitate communication between the two regions, we'll implement VPC peering and adjust the route tables accordingly. This setup ensures seamless connectivity across regions, vital for the distributed nature of our Jenkins pipeline.
Internet Connectivity and EC2 Deployment:
The next phase includes attaching Internet Gateways to VPCs in both regions. This step is preparatory for deploying EC2 instances that will host our Jenkins main and worker nodes, thereby establishing the distributed architecture of our pipeline.
Role of Ansible:
Ansible plays a critical role in this stage. It will be used to install the required Jenkins software and configure the integration of the worker nodes with the main Jenkins node. This automation ensures a smooth and efficient setup process.
Application Load Balancer and SSL Configuration:
Our Jenkins main node will be placed behind an Application Load Balancer (ALB). We'll utilize the AWS Certificate Manager service to generate an SSL certificate, ensuring secure HTTPS traffic. The ACM certificate will be validated against a domain in a Route 53 public-hosted zone for functionality.
DNS Routing and Final Touches:
Finally, we will configure Route 53 to route DNS queries to our load balancer's DNS name, allowing external traffic access to our Jenkins CI/CD Pipeline. This step marks the culmination of our deployment process.
3. Setting Up Terraform
Requirements for Installation:
To install Terraform, two primary steps are necessary:
1.Downloading the Terraform Binary: The binary can be downloaded from the HashiCorp website. It is crucial to select the correct version for your operating system and architecture.
2.Setting Up the Path: After downloading, you need to place the binary in a directory where your operating system can easily run it without specifying the absolute path each time.
I'm using the Windows environment for setting up the Terraform.
Testing the Installation:
Once the binary is moved to the path directory, test the installation by running the Terraform version. Successful execution of this command confirms that the Terraform binary is working correctly on your system.
4. Setting Up AWS CLI
Configure AWS CLI with AWS Account Credentials: Use the command aws configure and enter your AWS access key ID, secret access key, default region, and preferred output format.
Verifying the Installation: To ensure that both Ansible and AWS CLI have been installed and configured correctly, you can test them:
Test AWS CLI: Execute aws --version. Successful output indicates the installed version.
5. AWS IAM Permission For Terraform
When deploying resources using Terraform, such as EC2 instances, S3 buckets, or load balancers, Terraform needs the right permissions.
This can be achieved in two primary ways:
1.Creating an IAM User: This involves creating a separate IAM user within your AWS account, equipping it with the necessary permissions, and then using its access and secret keys with AWS CLI to authorize Terraform.
2.Creating an EC2 IAM Role: Alternatively, you can create an IAM role attached to your EC2 instance that grants permissions to Terraform.
Setting Permissions:
Regardless of the method chosen, the same level of permissions is required for both the IAM user and the IAM role. The permissions needed are both granular and comprehensive, allowing Terraform to create and destroy resources as needed.
Steps to Configure IAM Permissions:
1. Navigate to IAM Console: Log into your AWS Management Console and access the IAM console.
2.Create a Policy: Under Policies, create a new policy with the necessary JSON configuration that outlines the permissions Terraform needs.
3.Create an IAM User or Role: Depending on your choice, create either an IAM user or an EC2 role and attach the previously created policy to it. Ensure that the user has programmatic access and the role is tagged appropriately.
Save Credentials Safely: If creating an IAM user, make sure to download and securely save the access key ID and secret access key.
Policy: URL






Top comments (0)