This is a series of posts on Blockchain, Ethereum, Smart Contracts and their security. The work was done in collaboration with Dr. Andrew Melnik, Marvin Koppka and Mustafa Erdogan at Bielefeld University under ISY Project: NFTs and Cryptocurrencies With Smart Contracts with the aim to provide a reference material on the blockchain technology.
Smart contracts are automatized applications running on blockchain that unlike their traditional Web 2.0 counterparts guarantee immutability of state and hence enable secure execution of distributed transactions. This attracts their use in digital finance and specifically in applications where ownership of digital assets is transferred, for example, NFTs.
However numerous successful exploits and hacks of smart contracts show that just relying on blockchain security is not enough and additional measures are necessary. In this post we give a brief overview of the blockchain technology, explain the smart contracts workflow and discuss some of those hacks that happened to smart contracts and security issues with NFTs.
Part 1. Blockchain
See also Part 2. Ethereum on its architecture and two consensus algorithms, Proof of Work and Proof of Stake, which allow all nodes in the network to agree on a single state of the blockchain, and Part 3. Smart Contracts for a quick overview, risks, including reentrancy attack, and NFT use case with the objective to examine its storage options and associated risks.
Blockchain is a chain of blocks where each block references a prior block. Under the hood it uses various technologies including Peer-to-Peer Networks, consensus and hashing algorithms, as well as data structures such as Merkle trees and the chain of Blocks, which are discussed in the following sections.
1.1 Chain of Blocks
1.1.1 Blockchain — Structure
Blockchains run on computers, also called nodes, that are interconnected into a Peer-to-Peer Network (see Figure 1 and Section 1.2).
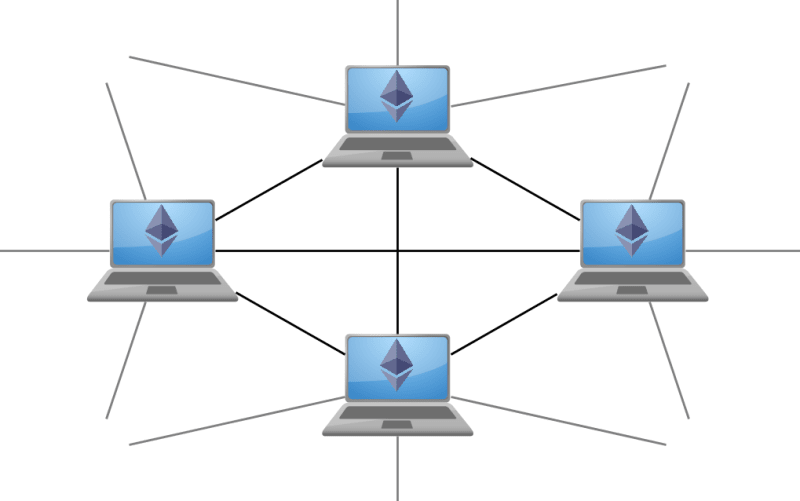
Each node tries to add a new block to the existing blockchain and announce that in the network, which yields rewards and sustains the blockchain. For Ethereum (discussed in Part 2. Ethereum), for example, these blocks consist of a Block Header, a list of Transactions and an Ommers List (see Figure 2).
The Transaction list contains transactions from a temporary memory pool, a waiting area for transactions, which a node includes into a candidate block to add to the blockchain if the node is deemed successful (see Figure 3).
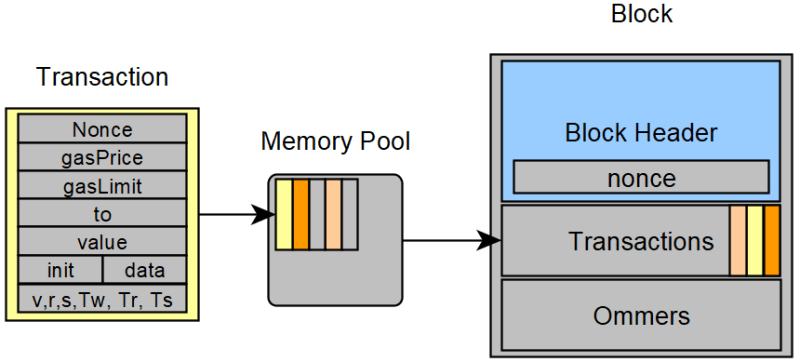
Sometimes multiple new blocks are ready to be added to the chain at the same time of which only one will be primarily used for the Blockchain. These other blocks are known as the Ommers or Uncles and yield a partial reward for adding blocks to the blockchain. The next section discusses how a chain of blocks is formed.
1.1.2 Metadata of Blocks — Block Header
The Block Header is the most essential part of chaining blocks. It consists of a digital fingerprint computed by using a hash function that takes its contents and a hash of a previous block as input. This allows participants to validate the full chain and detect any tempered blocks.
Besides the hash value of a previous block the block header has multiple other data structures such as Merkle trees, namely the World State Trie, Account storage content trie, Transaction Trie and Transaction Receipts Trie, which will be discussed in the next posts on Part 2. Ethereum and Smart Contracts.
1.1.3 Encryption Mechanisms
At the core of blockchain security lies a crucial feature of cryptography and its encryption mechanisms. "Cryptography can, for example, also be used to prove knowledge of a secret without revealing that secret (e.g., with a digital signature), or to prove the authenticity of data (e.g., with digital fingerprints, also known as "hashes"). These types of cryptographic proofs are mathematical tools critical to the operation of the Ethereum platform (and, indeed, all Blockchain systems), and are also extensively used in Ethereum applications."[22]
In blockchains, each Block is hashed with specific hashing algorithms. For Ethereum these encryption algorithms are Keccak-256 and the elliptic curve algorithm Secp256k1.[7][3] Elliptic curves are used to derive digital signatures and ensure that a transaction is valid and the user initiating it owns the corresponding assets. Keccak-256 is a one-way hash function used as a digital fingerprint ensuring data authenticity and is also used in the consensus algorithm to guarantee high computational effort for brute force attacks.
A good example of using these hashing algorithms is depicted in Figure 4. It shows a public key and address generation from a private key using elliptic curves and Keccak-256 function.
![Figure 4: Private Key, Public Key and Address Generation [19].](https://res.cloudinary.com/practicaldev/image/fetch/s--dE1Is23---/c_limit%2Cf_auto%2Cfl_progressive%2Cq_auto%2Cw_800/https://dev-to-uploads.s3.amazonaws.com/uploads/articles/hc1kqgoxdm78q0u0czb7.png)
1.1.4 Keccak Algorithm
According to the Keccak Reference and Keccak-256 Submission,[6][7] Keccak-256 is a hash function based on a sponge construction which takes any size of input and generates a chosen size of output. The key security property of hash functions is the collision and preimage resistance (see Figure 5) where two values mapping to the same hash cannot be found easily and neither can hash to a predefined output of the hash. This resistance in the case of Keccak-256 is achieved "By translating these computation complexities into physical quantities such as time or energy, both are simply out of reach and will remain so in the foreseeable future."[7]
To bring the unlikeliness of a hash collision of either an address or even a private key into perspective, let us illustrate that likelihood by using a simple example. Currently 8 billion people live on Earth, which is approximately equivalent to 2³³ ≈ 8.59 * 10⁹. If all people generated one million addresses (160 bits each, see Figure 4) per day for 10,000 years, it would amount to approximately 2⁷⁵ ≈ 3.78 * 10²² addresses generated out of all possible addresses 2¹⁶⁰ ≈ 1.46 * 10⁴⁸ with different bit combinations. In fact it would take about 2**(160–33–28) = 2⁹⁹ ≈ 6.34 * 10²⁹ years to generate a collision of an address. As private keys have even more bits, the years necessary to find a collision are astronomically high.
![Figure 5: Resistances when hashing [18].](https://res.cloudinary.com/practicaldev/image/fetch/s--UkKxw2CD--/c_limit%2Cf_auto%2Cfl_progressive%2Cq_auto%2Cw_800/https://dev-to-uploads.s3.amazonaws.com/uploads/articles/3zsf1s5x68qht81fobdu.png)
1.1.5 Merkle Tree
A Merkle tree is another data structure that is used to further enforce secure encryption of data. It is made up of hashes of various data sections that summarize all the transactions in a given block. Each leaf node in the tree is labeled with the cryptographic hash of a data block, and each non-leaf node is labeled with the cryptographic hash of its child nodes' labels. Implementations of a Merkle tree are mostly binary, with each node having two child nodes. This enables a quick verification of data consistency and quality across large datasets.
Figure 6 illustrates how data verification happens that uses a Merkle tree. The verifyCalldata function checks whether a leaf belongs to the Merkle tree defined by a root hash stored in a smart contract. Another parameter is a proof which is a bytes32 array created off-chain.
![Figure 6: Merkle Tree verification procedure [8].](https://res.cloudinary.com/practicaldev/image/fetch/s--INkkG2Tj--/c_limit%2Cf_auto%2Cfl_progressive%2Cq_auto%2Cw_800/https://dev-to-uploads.s3.amazonaws.com/uploads/articles/eyd05sdzmv2e5g0e3qr9.png)
Internally, this functions calls processProofCalldata function that iterates through each element in the proof array and computes recursively a resulting hash based on the proof elements and a hash computed on the previous iteration, starting from the leaf value. This hash is then compared to the root hash to see if they are equal.
In the next section, we will discuss the third technology that is necessary for blockchains to operate, peer-to-peer Networks.
1.2 Peer-to-Peer Networks
Blockchains are upheld, shared and expanded in a decentralized fashion through the use of a peer-to-peer network (see Figure 1). Nodes in the network refer to computers running instances of a given Blockchain client software and forming connections to other computers.[2] They expand the blockchain by adding blocks to their local copy of the existing blockchain and sharing newly found blocks with others.
In addition to propagating transactions and blocks among the network, nodes validate data to achieve consensus and thus strive to maintain a single state of the blockchain. Interaction with this decentralized data structure from a user’s perspective happens via a node or a wallet.[17] A wallet can send transactions to a node which then adds the transaction if verified to a temporary pool of transactions called the memory pool. This transaction gets propagated over the network enabling every node to include this transaction in the next block.
A fee for the transaction hereby indirectly orders the transactions, as nodes are more likely to include transaction into the, to be added, candidate block if the fees they receive are higher. Nodes add their own address to a block, as the first transaction in the block in the case of Bitcoin and as a beneficiary field in the Block Header for Ethereum, in order to collect rewards for adding a valid block to the blockchain.
Next we will look at how the consensus mechanism is realized in blockchain that enables all nodes to agree on its single state.
1.3 Mining: Consesus among the Network
Consensus algorithms exist in order to realize consensus among the network on a single state of the Blockchain. Each transaction gets approved before being added to the node memory pool, which involves adhering to the Blockchains rules and confirming the ownership of the currency for the transaction as well as getting validated by other nodes in the network after a given block has been broadcasted. This helps avoid erroneous blocks and adhere to a single state of truth. Additions of blocks to the Blockchain are thereby controlled by the consensus algorithm. Different algorithms exist, such as Proof of Work which entails adaptable complex calculations and Proof of Stake requires staking of currency.
Proof of Work (PoW) describes the consensus mechanism of providing work in the form of solving complex calculations. The block header of the candidate block gets hashed together with an iterative value called nonce (the number used once). The result of the hash needs to be below a specific target value chosen by the network and adapted relative to the computing power in the network (see Figure 7).

If a fitting nonce value leading to a hash being below the given target was found, the block is deemed valid and can be added and shared among the network. It will then be executed, verified and added by each node. Afterwards, a new candidate block is brought about with new transactions and the process continues.
Nodes participating in the PoW mechanism are referred to as miners. As finding a nonce requires substantial computation resources, miners usually group together in mining pools to solve the mathematical problem. This increases their chances of success and distributes the reward among them.
1.4 Energy Consumption
When Satoshi Nakamoto created the first cryptocurrency in 2009, his goal was to establish a decentralized payment system that would facilitate quick and borderless transactions. Although not in the manner Nakamoto desired, Bitcoin has become mainstream more than ten years later. Cryptocurrencies now serve as speculative assets rather than transaction tools, attracting investors who think they may sell their holdings in the future with profit.
A consequence of that demand for Bitcoin is its high price that attracts mining companies to install more nodes in the network to get highly-valued rewards for mining new blocks. This results in a growing competition between the nodes and since Bitcoin uses Proof of Work consensus algorithm, which requires nodes to solve a difficult mathematical problem, ultimately that competition leads to a high electricity usage by the network. Figure 8 outlines how Bitcoin energy consumption changed from January 2017 to September 2022.
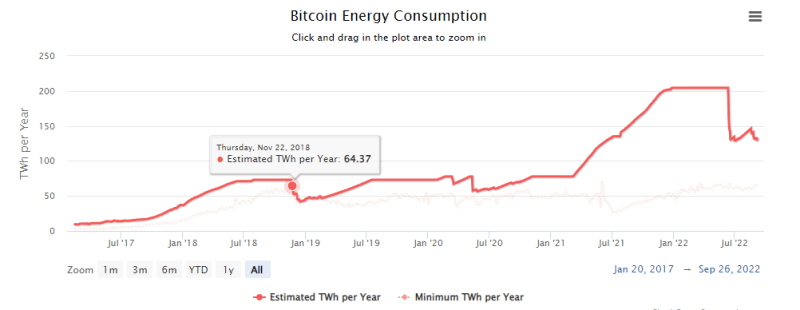
The estimated yearly electricity usage of Bitcoin is 127 terawatt-hours (TWh). This is greater than Norway’s whole annual electricity use. In fact, Bitcoin needs more electricity than Ethereum (see Part 2. Ethereum), roughly 11 times as much (707 kilowatt-hours (kWh)) for every transaction, even though Ethereum runs 1.7 times as many transactions per second (TPS) as Bitcoin. Furthermore, as will be mentioned in the next post, Ethereum recently changed its consensus algorithm from Proof of Work to Proof of Stake, which reduced its energy consumption by 99.95%.[1] If more blockchains adapted Proof of Stake, their energy consumption and the need for special hardware could be reduced significantly.
1.5 Decentralization Issues
Another issue is the size of specific Blockchains. Due to the structure of the Blockchain and the usage of peer-to-peer networks in order to uphold it and achieve consensus, computing power and users are essential. Without users the Blockchain could neither be sustained nor reasonably agreed upon a single state. As a result, majority attacks (51% attacks) could be performed much easier than on large Blockchains, such as Bitcoin or Ethereum, in which 51% computational power would be hard to achieve by any party. Currently, rewards and fees serve as an incentive for miners to produce new blocks. This however will not be always the case because some Blockchains will leave only fees as the sole incentive for miners, most likely reducing their number.
Furthermore, because miners form mining pools to have a higher chance of solving the mathematical problem to generate new blocks, the success of a majority attack can become possible. In some cases only two or four mining pools would have to combine in order to achieve >51% mining power, which could then alter the Blockchain, albeit limited, to their needs.[21]
Summary
This concludes the first post about Blockchain, its security fundamentals and issues arising from the choice of its consesus algorithm to create a single chain of blocks that all the nodes in the Peer-to-Peer network agree on.
In the next post about Ethereum Blockchain we will consider the building blocks of Ethereum in detail and then return to discussing risks and issues.
References
- The Merge on Ethereum, https://ethereum.org/en/upgrades/merge/.
- Ethereum nodes and clients, https://ethereum.org/en/developers/docs/ nodes-and-clients.
- Chapter 4. Cryptography — Elliptic Curve Cryptography Explained, https://www.oreilly.com/library/view/mastering-ethereum/9781491971932/ch04.html.
- Ethereum Yellow Paper, https://ethereum.github.io/yellowpaper/paper.pdf.
- Functionality of smart contracts, https://www.ibm.com/topics/smart-contracts.
- The Keccak reference, https://keccak.team/files/Keccak-reference-3.0.pdf.
- The Keccak SHA-3 submission, https://keccak.team/files/Keccak-submission-3.pdf.
- Merkle Tree, https://soliditydeveloper.com/merkle-tree/.
- Blogpost of Vitalik Buterin — Merkling in Ethereum, https://blog.ethereum.org/2015/11/15/merkling-in-ethereum.
- NFT Metadata, https://www.weforum.org/agenda/2022/02/non-fungible-tokens-nfts-and-copyright/.
- Reentrancy attack in a Solidity smart contract, https://cryptomarketpool.com/reentrancy-attack-in-a-solidity-smart-contract/.
- ERC Token Standards - The Ultimate List, https://www.blockchain-council.org/ethereum/erc-token-standards/.
- Why Does Bitcoin Use So Much Energy? https://www.forbes.com/advisor/ca/investing/cryptocurrency/bitcoins-energy-usage-explained/.
- ERC-721 Non-Fungible Token Standard, https://ethereum.org/en/developers/docs/standards/tokens/erc-721/.
- Ethereum block architecture, https://ethereum.stackexchange.com/questions/268/ethereum-block-architecture.
- Ethereum Virtual Machine, https://ethereum.org/en/developers/docs/evm/.
- Ethereum Wallets, https://ethereum.org/en/wallets/.
- Cryptographic Hashes and Bitcoin, https://freecontent.manning.com/cryptographic-hashes-and-bitcoin/.
- Private and public keys on Ethereum, https://www.massmux.com/private-and-public-keys-on-ethereum/.
- What Is Sleepminting And Will It Ruin NFT Provenance? https://timdaub.github.io/2021/04/22/nft-sleepminting-beeple-provenance/.
- Pentagon finds concerning vulnerabilities on blockchain, https://www.techrepublic.com/article/pentagon-finds-concerning-vulnerabilities-on-blockchain/.
- A. M. Antonopoulos and G. Wood. Mastering Ethereum: Building Smart Contracts and DApps. O’Reilly Media, 2018.
- Bitcoin Energy Consumption Index, https://digiconomist.net/bitcoin-energy-consumption.








Top comments (4)
Thanks for sharing! This is really a good introduction.
Hi Victor, nice to meet you and thanks for your feedback! Next week I am planning to publish Part 2 where we will examine Ethereum architecture and two of its consensus algorithms, Proof of Work and Proof of Stake. Stay tuned!
Great blog, @yuryoparin 👍
Cheers and welcome to the blog!